
- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources

Cloud-based systems offer a lot of convenience to users. They allow for remote access and collaborative work, which can be very beneficial in many scenarios. However, they also come with their own set of risks that must be considered before using them in any type of environment.
Cloud attacks are becoming more common with the rise of cloud computing. The security measures for cloud computing systems are still in progress and there is a lack of understanding on how to protect them. This blog will explore some of the best practices for protecting against types of attack vectors.
The idea of a "Cloud" is that it is a network of servers with access to data and resources that can be accessed remotely. However, there are many risks associated with this type of setup. One major concern is the lack of control over what happens on these networks. There are many publicly accessible resources on these networks that are not secured. This means that anyone who finds the right path can access them and potentially steal information or cause damage to the network itself. There are various ways in which hackers can exploit cloud networks. They can use brute force attacks, denial of service attacks and phishing techniques to gain access to these networks and steal data from them.
Cloud Network isolation is the process of isolating a cloud-based network from other networks. This process can be done for a number of reasons, but one of the most common is to ensure that data cannot be transferred from one network to another without authorization.
One way that this can be done is by using a firewall. The firewall will only allow traffic to pass if it has been authorized. This means that any traffic coming from an unknown source will not be able to get through the firewall.
As more and more businesses move to the cloud, it's important to have a robust security solution in place to protect your data and applications. Prisma Cloud's Network Security Solution from Palo Alto Networks is a great solution for cloud-based networks. It protects your network from threats and provides real-time visibility into your network traffic.
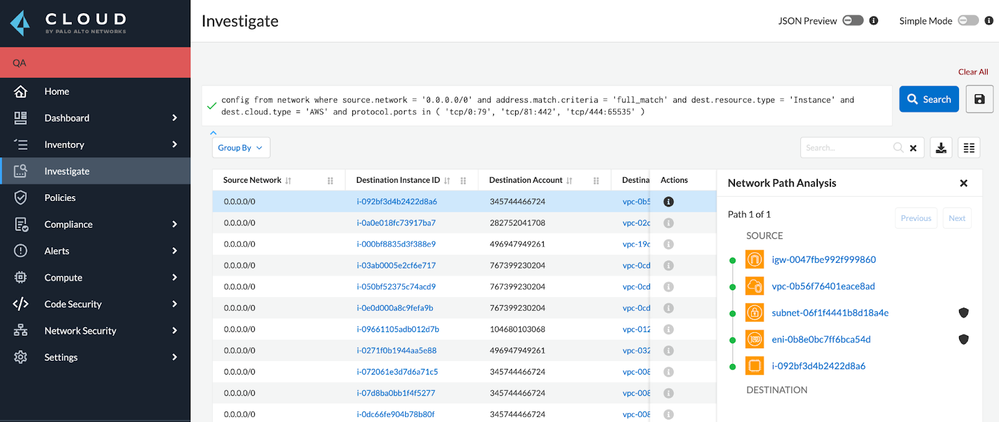
The cloud has drastically changed the way we access and store information. In the past, access to information was typically limited to those who had physical access to the data. However, with the advent of cloud computing, access to information is now much more accessible. This increased accessibility has led to new challenges in terms of security and control.
Identity access management is a process that helps to control and secure access to information in the cloud. This process typically includes authentication, authorization, and auditing. However, It’s important to understand the risks of overly permissive access and Wild card permissions. Granting access to all resources, can leave your data and resources vulnerable. Cross-account access is another risk factor if one account is compromised, all of the accounts with access to that account are also at risk.
Access control is the process of determining who is allowed to access what resources. Access controls should be based on the principle of least privilege, which means that users should only have the permissions they need to perform their job.
Role-based access control (RBAC) is an authorization system that provides fine-grained access management powered by Identity and Access Management (IAM). RBAC provides complete visibility and oversight into application permissions and the ability to easily manage who has access to resources, what areas of the network can be accessed by users, and what types of actions users can perform with the resources they are permitted to use.
If you're looking for a great Cloud Infrastructure Entitlement Management (CIEM) tool, Prisma Cloud's CIEM is a great solution. With Prisma Cloud, you have complete control over permissions and can detect unauthorized access so that your cloud infrastructure is safe and secure.
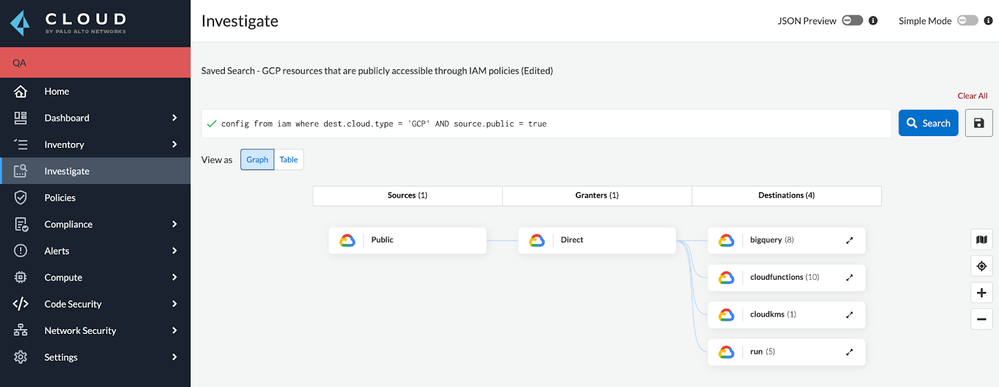
Data exfiltration from the cloud is a serious security concern. Enterprises are storing more and more data in the cloud, and this data is often sensitive. hackers are well aware of this, and are increasingly targeting cloud data in attempts to steal it.
Data exfiltration from the cloud can have serious consequences. sensitive data may be leaked, and companies may be subject to regulatory penalties. To protect against data exfiltration, enterprises should carefully control access to cloud data and monitor for suspicious activity.
As data becomes increasingly digital, organizations must take steps to protect their information from unauthorized access. One way to do this is through encryption, which encodes data so that it can only be read by those with the decryption key. Cloud data encryption is the process of encoding data so that only authorized users can access it.
When data is stored in the cloud, it is often encrypted by the service provider. However, organizations should also encrypt their data before it is uploaded to the cloud to ensure that it is protected from unauthorized access.
Prisma Cloud's Data Security is a great solution for organizations that want to keep their data secure. It provides a number of features that help to protect data, including data classification and malware detection.
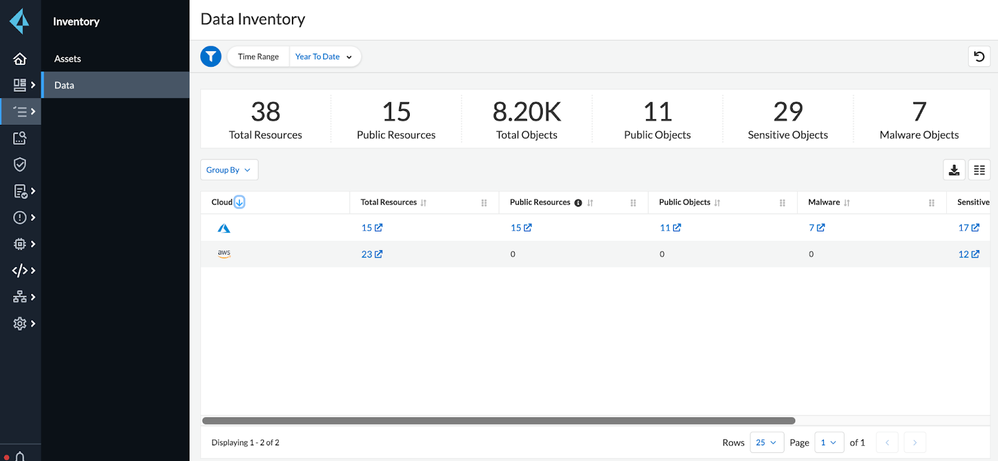
A Cloud security misconfiguration is a type of security vulnerability that arises when a cloud resource is incorrectly configured. Such misconfigurations can leave data and systems exposed to attack, and can happen at any stage in the cloud computing lifecycle. The most common cause of cloud security misconfigurations are human error, default configurations, architectural design issues, and lack of understanding of security services are all potential sources of problems.
Cloud posture management is the prime mitigator of cloud security misconfigurations. By automating security audits on change, implementing strict network rules and designing well architecture, an organization can keep its cloud environment secure.
Using Cloud posture management, they can perform regular audits of their cloud environments, and put processes and controls in place to prevent accidental or unauthorized changes. following are a few key things you can do to help mitigate these misconfigurations:
Prisma Cloud’s Cloud Security Posture Management (CSPM) is a great solution for keeping track of your cloud security posture and ensuring compliance with various security standards. It can help you identify and fix misconfigurations that could lead to breaches, and it can also monitor for compliance with various security standards.
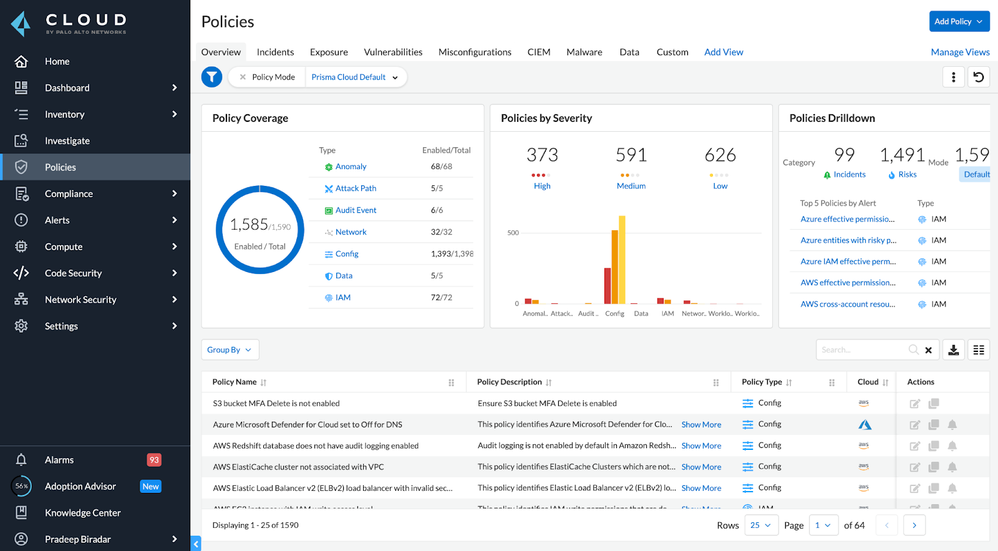
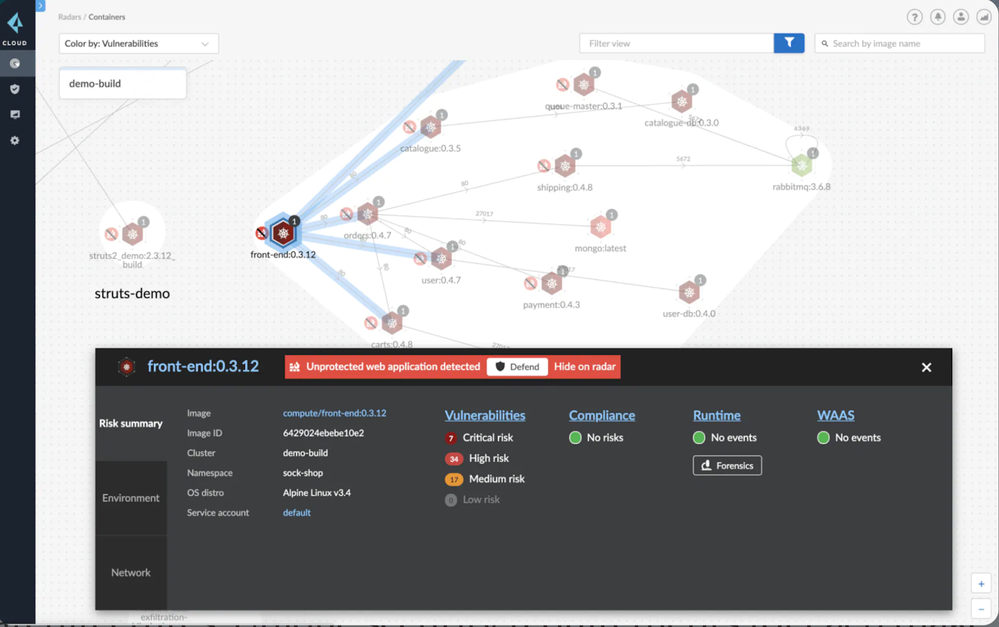
Cloud Vulnerability exploits are becoming more and more common. With the rise of cloud computing, many businesses are moving to the cloud to store their data. While cloud computing has many benefits, it is important to be aware of the vulnerabilities that exist.
Unfortunately, many companies are still using vulnerable software and leaving themselves open to attack. One of the most common ways for attackers to gain access to a system is by exploitation of vulnerabilities in out-of-date or unpatched software. Often times, attackers will use malware or viruses to exploit these vulnerabilities, which can be difficult to detect and protect against.
Vulnerability management is a critical part of mitigating the risk of cloud vulnerability exploits. Keeping systems up to date with the latest patches and versions is the best defense against attacks. However, sometimes patches are not released in a timely manner, or they are not applied properly. This can leave systems and applications vulnerable to attack.
To help protect against these types of attacks, there are a few things you can do. First, use a good antivirus and antimalware program and keep it up-to-date. Second, use a Web Application Firewall (WAF) to detect and block malicious traffic.
With Prisma Cloud’s Cloud Workload Protection you can secure hosts, containers and serverless applications across the full application lifecycle. Prisma Cloud delivers a centralized view to help prioritize risks in real time across public cloud, private cloud and on-premises environments for every host, container and serverless function.
By understanding the cloud attack vectors and how to prevent data breaches, organizations can keep their data safe and avoid costly security breaches. Palo Alto Networks Prisma Cloud can help you increase your cloud security and prevent breaches.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
| Subject | Likes |
|---|---|
| 3 Likes | |
| 2 Likes | |
| 2 Likes | |
| 2 Likes | |
| 2 Likes |




