
- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
This blog written by Mitch Rappard.
Celona and Palo Alto Networks recently announced an exciting technology partnership that allows enterprise customers to use their joint solutions for greater visibility and security of the devices on their private wireless networks. Using this enhanced visibility, customers are able to achieve Zero Trust security for the users and devices attached to the private wireless network. This blog covers some of the details of this solution along with several use cases. For additional information please see our Joint Solution Brief located here.
Private 5G networks enable new enterprise use cases not previously possible, allowing for industrial-scale IoT/OT networks, such as factories, distribution centers, oil refineries, mining operations, with ultra-low latency, mission-critical reliability, and a high degree of mobility. The growing interconnectivity of IoT and OT devices, encompassing scanners, tablets, cameras, AGVs, AMRs, and diverse sensors, poses cybersecurity challenges that organizations must address.
Zero Trust, put as simply as possible, ensures that every flow on the network is understood down to the application/protocol/service level and maps to some device and application that is allowed to be on the network. In short, to offer a Zero Trust security posture, you must eliminate implicit trust, and answer the following questions for each flow, as defined by the Kipling Method:
For mobile networks, the “who” can be thought of as the IMSIs and IMEIs of the devices attached to the network. The integration with Celona equips our joint customers to gain visibility into Subscriber-IDs (IMSI for 4G, SUPI for 5G) and Equipment-IDs (IMEI for 4G, PEI for 5G) for their traffic. This functionality coupled with Palo Alto Networks App-ID and Content-ID technology, allows customers to adhere to Zero Trust security principles by removing implicit trust while gaining visibility into the applications, services and threats on their network.
This integrated solution brings together key components of both companies' product portfolio to enable unprecedented visibility and control into the mobile IoT devices on a private wireless network allowing for Zero Trust security out of the gate.
The solution includes Palo Alto Networks Next-Generation Firewall (NGFW), enterprise IoT security, the most comprehensive Zero Trust solution for IoT devices, along with our security orchestration automation and response platform, Cortex XSOAR. Celona is providing the private wireless network via the Celona 5G LAN, a turnkey private wireless solution uniquely engineered for enterprises.
The Palo Alto Networks NGFW offers a prevention-focused architecture that’s easy to deploy and operate. Powered by AI and ML, the NGFWs inspect all traffic, including all applications, threats, and content, and tie that traffic to the subscriber and equipment, regardless of location or device type. Enterprise IoT Security provides visibility, risk assessment, and protection against known and unknown threats, Zero Trust policy enforcement, and operational insights in a single platform.
Using a custom Integration, Cortex XSOAR ingests the device information for all the endpoints on the private wireless network. It then stores these as Indicators, and ensures that key elements like the IMSI, IMEI, and IP address are passed to the correct NGFWs. By doing this the NGFW is able to use its Subscriber-ID and Equipment-ID features to enact policies based on IMSIs and IMEIs or groups of these identifiers.
Now that we understand our approach to Zero Trust for private wireless and the ways that Celona and Palo Alto Networks work together to accomplish this, let's shift gears and focus on some use cases.
Imagine you have a cellular connected PLC in an OT network, and it needs to securely communicate with a HMI using Modbus. We want to ensure that only the correct protocols are sent to/from the HMI and that this data is coming from the right device or set of devices.
To do this, we could configure policies on the NGFW that allow only the Modbus protocol coming from the relevant PLCs. Instead of using an IP address for the PLC, we could use its hardware ID, which is its IMEI. If the IMEI for a device was “123456789011111” a policy might look like:
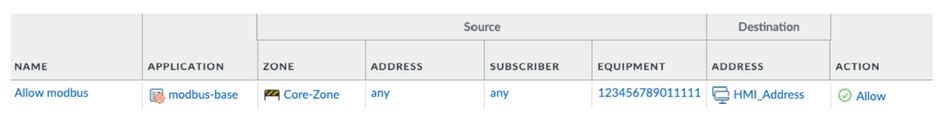
In this example, a device on the network has been infected, and is now trying to see if it can successfully execute a SCADA specific attack towards vulnerable devices on the network. In order to accomplish this, it sends a payload aiming to exploit a dated CVE that is specific to Schneider devices. The NGFW, using its threat prevention capabilities, detects the threat and blocks it. It generated logs which are forwarded to a SIEM and possibly other entities. As these notifications are sent out, the NGFW identifies the exploit, the application used, the criticality, and perhaps most importantly, the IMEI and IMSI which is infected with the malware.
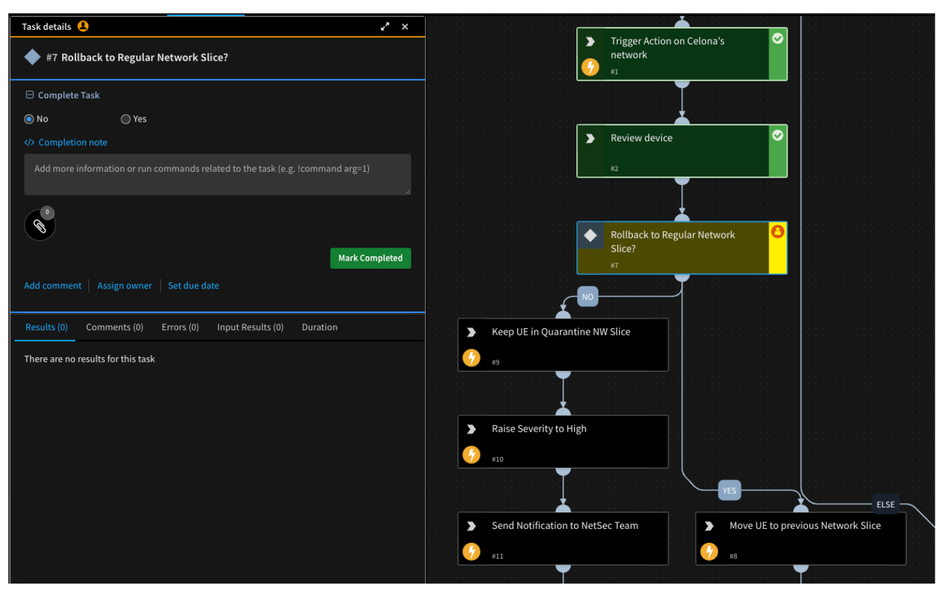
To demonstrate the power of machine speed automation, Palo Alto Networks and Celona created a XSOAR playbook which calls an API on the Celona Orchestrator to move an infected device to a quarantine Device Group. After this action is taken, the SOC analyst, upon further investigation, can move them back to the previous Device Group, or keep them in quarantine.
Customers face multiple challenges in addressing use cases for OT Visibility. A key one gaining momentum is the convergence of information technology (IT) and operational technology (OT) networks, and the increasing adoption of private wireless networks over legacy Ethernet or Wi-Fi technology. Deploying a Celona 5G LAN, and Palo Alto Networks NGFW, customers are able to easily enable OT security for wireless devices by simply turning on our IoT Security Subscription on the NGFW. With this solution no additional agents are needed on the endpoints. The NGFW, using its Layer 7 visibility into all the applications and protocols, is able to pass on enhanced logs to our IoT Security subscription to be analyzed.
The details of our Zero Trust OT security offering is covered in a previous blog. For OT security Zero Trust starts with visibility, but not just network flow visibility. For OT networks, it is crucial that customers have access to high fidelity asset visibility and risk assessments for all their OT devices.
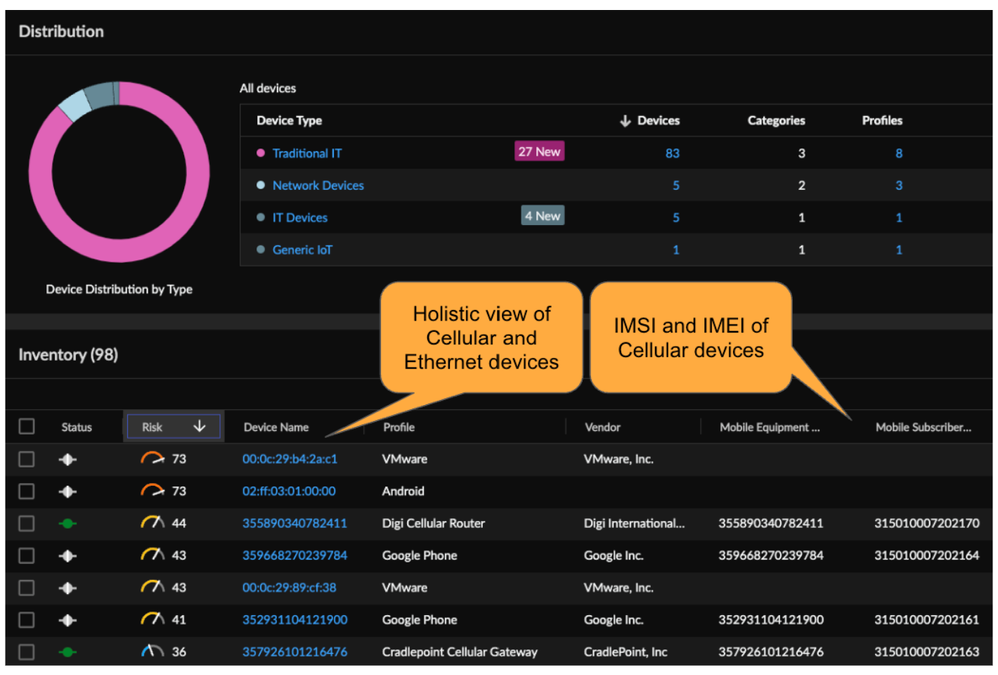
Palo Alto Networks recently announced several new OT related capabilities including industry-leading asset identification and risk visibility for 5G connected devices. Using a combination of GSMA’s device database, and machine learning, we are able to now provide comprehensive visibility, in a single pane of glass, for all your ethernet and cellular OT devices. Below is an example of the details we provide across both cellular and non-cellular IoT/OT devices.
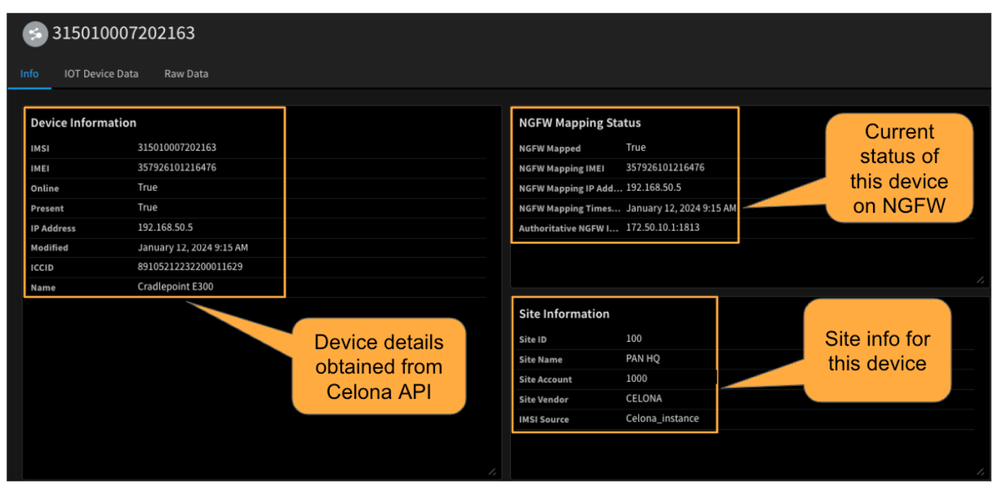
In XSOAR, device information is stored as Indicators, accompanied by additional metadata such as the device's site information and the corresponding NGFW with its current state. This proves beneficial when executing workflows on XSOAR, especially when specific actions like policy changes or updates are necessary at a designated NGFW.
A Zero Trust security foundation is key to a successful digital transformation. Enterprises must maintain continuous real-time visibility and precise control over 5G network traffic to swiftly detect and stop malicious activities and threats, and establish an effective and scalable defense against adversaries.
Is your enterprise preparing for 5G adoption? Delve into the collaborative integration on the Palo Alto Networks and Celona partner page, and uncover the means to extend zero-trust security into your private 5G networks. To explore the capabilities of our joint solution and discover how it can drive meaningful results for your business, simply reach out to request a demo.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
| Subject | Likes |
|---|---|
| 3 Likes | |
| 2 Likes | |
| 2 Likes | |
| 2 Likes | |
| 1 Like |




