
- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources

This blog written by Tomer Haimof.
As applications are deployed across multiple clouds - public, private, hybrid - organizations are using a wide array of compute architectures. You have virtual machines (VMs), containers, Kubernetes, containers as a service (CaaS), platform as a service (PaaS) and serverless cloud entities that have to be monitored and secured.
Prisma Cloud Compute provides cloud workload protection, regardless of their underlying cloud technology or the cloud they run on. This includes runtime security, API protection, compliance coverage, and vulnerability management. Cortex XSOAR seamlessly integrates with Prisma Cloud through the Prisma Cloud Compute by Palo Alto Networks pack, providing a focused solution for efficiently handling various cloud security needs.
Imagine a scenario where a container within your infrastructure is compromised, triggering runtime audit events. The aftermath demands meticulous investigation, and this is where the Cortex XSOAR Prisma Cloud Compute - Audit Alert v3 playbook, a part of the Prisma Cloud Compute pack, steps in.
Each incident processed through this playbook yields a wealth of information for the security analyst. This not only expedites the investigative process but also empowers teams for automatic handling and response, saving precious time and ensuring no runtime audit event goes unnoticed.
Before we delve into the incident layout, let's explore the playbook sections to see how automation is applied to remediation.
Container, images and hosts information enrichment: Gather comprehensive details, including compliance and vulnerability information, to help the analyst understand the context of the incident.
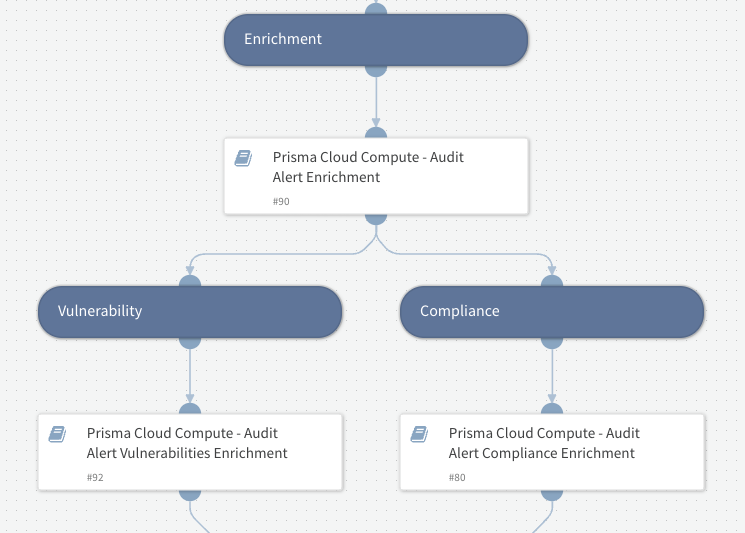 Fig 1: Data enrichment
Fig 1: Data enrichment
Defender logs: Access detailed logs to gain insights into potential threats and vulnerabilities.
Extract forensic data from containers and hosts: Extract forensic data for a deeper understanding of the incident.
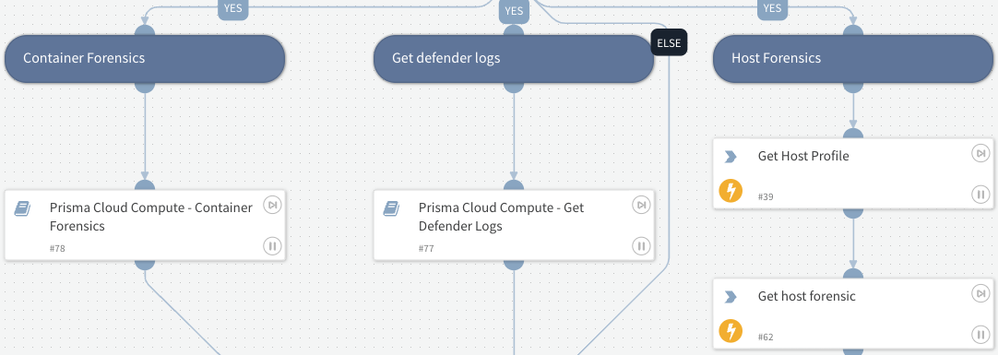 Fig 2: Extract forensic data
Fig 2: Extract forensic data
Retrieve relevant alerts: Retrieve historical alerts to piece together the security puzzle.
Get potential owner information: Identify responsible parties swiftly for a targeted response.
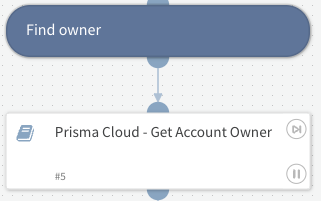 Fig 3: Get account owners
Fig 3: Get account owners
Perform automated remediation: Leverage out-of-the-box playbooks like Block Indicators - Generic v3 and Cloud Response - Generic for effective remediation.
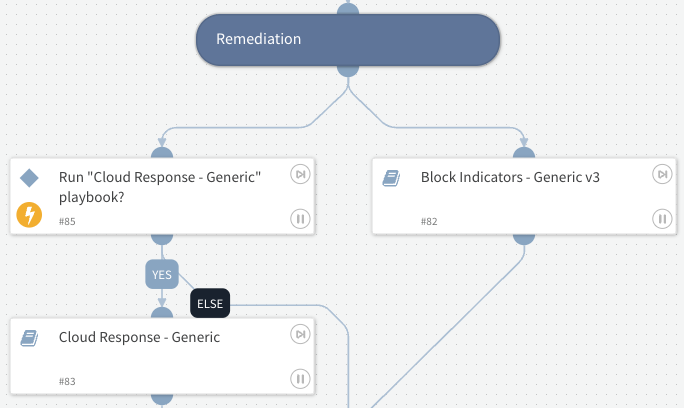 Fig 4: Run OOTB playbooks for automated remediation
Fig 4: Run OOTB playbooks for automated remediation
Now, let's explore how the playbook sections manifest in the incident layout, where key details are neatly organized:
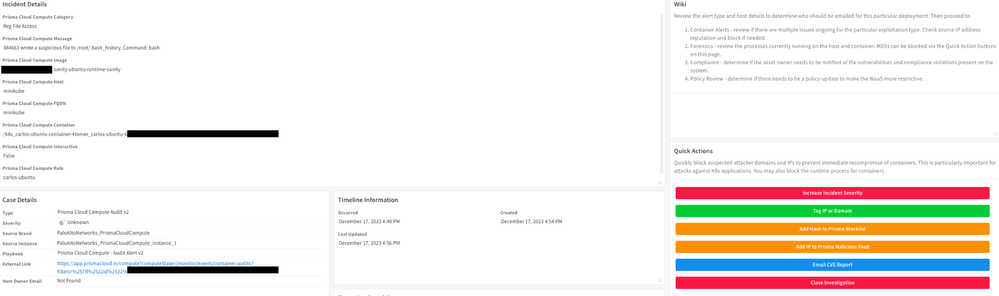 Fig 5: Incident layout with custom Quick Action buttons
Fig 5: Incident layout with custom Quick Action buttons
Container Alerts Tab
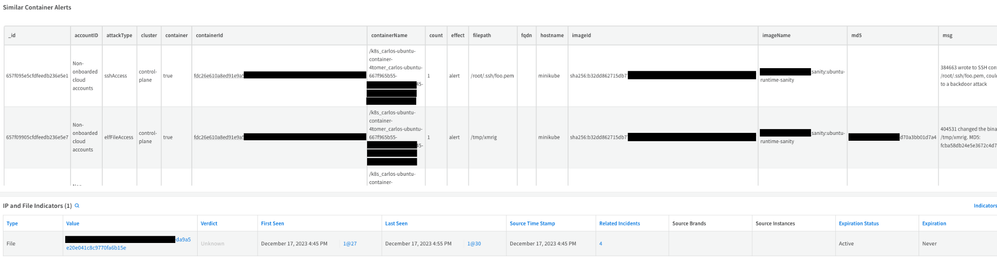 Fig 6: Container alerts details tab
Fig 6: Container alerts details tab
Forensics Tab
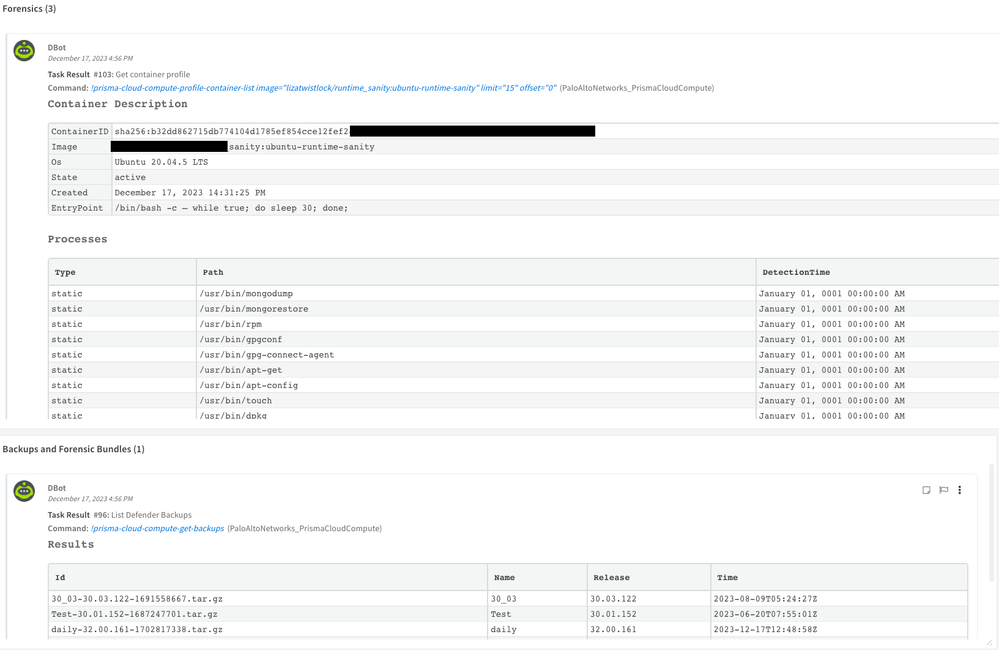 Fig 7: Forensic data details tab
Fig 7: Forensic data details tab
Compliance Tab
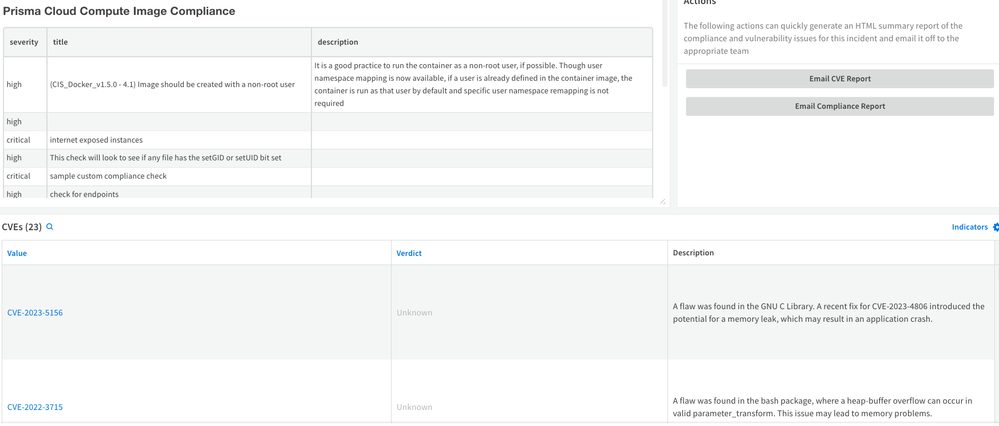 Fig 8: Compliance issue details
Fig 8: Compliance issue detailsConsider a scenario where a container communicates with a C2 server, triggering a runtime audit event. This event is ingested into XSOAR, triggering the playbook. Cloud security and SOC analysts can swiftly access all relevant information, communicate with stakeholders, and implement automated or manual remediation.
The result?
A significant reduction in investigation time and fortified security defenses.
The Cortex XSOAR Prisma Cloud Compute - Audit Alert v3 playbook, part of the versatile Prisma Cloud Compute by Palo Alto Networks pack, offers an automated approach to handling runtime audit events. As we navigate the complex terrain of cloud security, this playbook serves as a valuable asset, guiding security teams towards efficient incident resolution and comprehensive threat management.
In a dynamic cloud world where seconds matter, the Cortex XSOAR's Prisma Cloud Compute - Audit Alert v3 playbook emerges as a reliable ally, ensuring runtime audit events are not just responded to but proactively managed.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
| Subject | Likes |
|---|---|
| 3 Likes | |
| 2 Likes | |
| 2 Likes | |
| 2 Likes | |
| 1 Like |




