
- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources

If you are reading this blog, there’s a high chance that you already have dozens, if not hundreds, of virtual networks in Azure. Whether your migration was a “lift-and-shift” or “ landing zone” type, you have likely come across the virtual wide area network (vWAN) and the benefits it offers while expanding your Azure footprint. Let’s quickly go through the main characteristics of the vWAN to explain why securing it is a big deal.
The vWAN is a routing service from Azure. It manages dynamic routing for you and simplifies connectivity by leveraging the Azure backbone network. The user-defined routes (UDRs) sprawl is real and vWAN helps with connecting the spokes and advertising prefixes across the network. Whether it’s workloads in VNets or your on-prem assets connected to them via ExpressRoute, the vWAN hub is where the traffic is aggregated and routed in Azure. Add to the mix site-to-site VPNs, Border Gateway Protocol (BGP)-peered multi-cloud routers, branch connections, and multi-region deployments with traffic going across wider geographies.
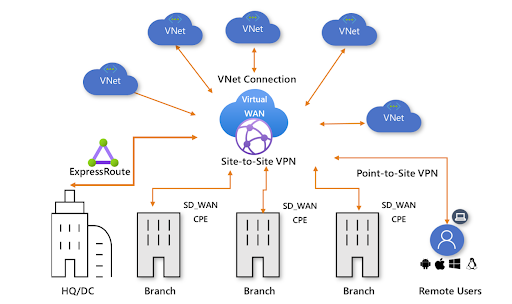
[Source Image Link: https://learn.microsoft.com/en-us/azure/virtual-wan/media/virtual-wan-about/virtual-wan-diagram.png#...]
As you can see from the diagram above, vWAN plays a central role in connecting and managing network traffic between various Azure regions, on-premises locations, and branch offices. Priority tasks for network security and cloud infrastructure teams involve enforcing strict boundaries and preventing unauthorized access, as well as identifying and responding to malicious activities, network attacks, and intrusion attempts. By implementing robust security measures within an Azure vWAN, you gain better visibility into your network traffic. This enables you to monitor and detect any anomalies, suspicious activities, or potential security breaches. What’s more, this visibility allows for proactive incident response and ensures timely mitigation of security incidents.
When it comes to securing the vWAN, existing solutions typically either lack the threat efficacy of a Next-Generation Firewall or are so clunky they can’t be considered cloud-native. Relying on native NSGs to control access to and from the VNets is simply insufficient. Forcing cloud traffic back to on-prem to be inspected by a perimeter firewall is far from optimal. It is also crucial to inspect outbound connections, especially for something like Azure Virtual Desktop.
The next available and easy-to-use option is Azure Firewall, which provides essential network security capabilities. However, this tool should be augmented by some advanced features available in other dedicated firewall solutions. Depending on the complexity of the deployment, more granular control, sophisticated threat intelligence, and advanced monitoring capabilities are required for compliance and adequate protection.
For example, if you have a multi-cloud or hybrid cloud strategy, relying solely on Azure Firewall might limit your flexibility and make it challenging to integrate with other cloud providers or on-prem solutions. If you already have Palo Alto Networks firewalls on-prem and in other clouds, you’d want to keep a consistent security posture across these deployments and manage your security policies in one place. Thankfully, Panorama provides centralized management while ensuring the threat protection efficacy of a long-time leader in the Gartner Magic Quadrant for Network Firewalls.
Traditionally, firewalls in Azure are deployed as the Network Virtual Appliances (NVAs). This approach requires deploying virtual machines, procuring licenses, configuring and managing them completely by the network security team. On top of that, you have to manage your own High-Availability (HA) by deploying and running load balancers and monitoring the cluster's health. Software upgrades aren’t necessarily easier than on-prem hardware firewalls as you still have to take down and upgrade individual firewalls in a maintenance window. On the vWAN side, you have to deploy the NVA in a transit VNet that in itself becomes a spoke connected to the vWAN hub. This still requires configuring user-defined routes to steer traffic via the firewall or using BGP on the firewall itself to control which traffic gets inspected.
A step in the right direction is a managed NVA approach. It simplifies the deployment into the vWAN hub. While it provides high availability by use of Microsoft-managed infrastructure, it still requires procuring the license from the vendor and use of its orchestration solution to deploy it. As for networking, you are required to set up BGP peering with the virtual hub to exchange routes. It lacks autoscaling as no one is monitoring the utilization of the NVA. The experience is still quite far from “firewall-as-a-service."Managed-NVAs might not provide seamless integration with native Azure security services or can lack compatibility with certain network protocols or configurations. This can limit the overall flexibility and interoperability of your network infrastructure.
Cloud NGFW for Azure is an Azure-native, ISV-managed Next-Generation Firewall service. What that means is Palo Alto Networks performs all the infrastructure management. High availability, load-balancing, software upgrades, and scaling is all continuously delivered as a cloud-native Azure service. The service is consumed by creating a Cloud NGFW resource, which Palo Alto Networks manages; this means it lives and breathes in the Azure Resource Manager (ARM) framework, which enables all kinds of integrations using Azure API, Azure CLI, PowerShell, and Terraform.
The Palo Alto Networks Panorama management is also enabled to manage the Cloud NGFW for Azure, just as it would for any other Palo Alto Networks firewall, but in this instance, via the Azure plugin. This way you can have a consistent security posture across the firewalls deployed on-prem and in the public cloud, and it doesn’t matter whether the firewalls are Cloud NGFW, VM-Series virtual firewalls, CN-Series container firewalls, or hardware PA-Series.
With respect to the vWAN, Cloud NGFW is deployed directly into the Azure Virtual Hub with no additional configuration or requirements. There is no need to touch BGP or any other routing configurations outside of vWAN-native Routing Intent and Policies configuration. Cloud NGFW for Azure leverages the SaaS Solutions framework; deployment is accomplished in just a few minutes.
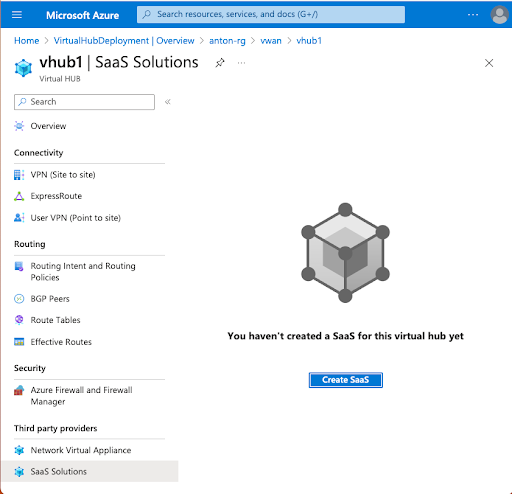
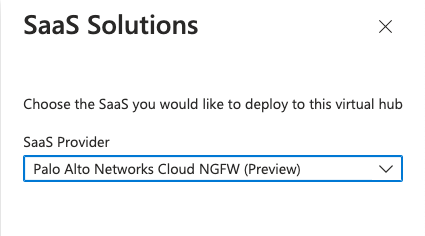
Cloud NGFW security policies can be managed by Panorama via the Azure plugin, which provides a unified interface to manage security policy across multiple clouds and on-prem environments. For more flexibility, another option is available: Manage the security policy right in Azure Portal using Rulestack to create rules leveraging App-ID, URL filtering, Decryption, and Security Profiles.
Once the firewall is up and running, all you have to do is set the Routing Intent and Routing Policy to send traffic via the Cloud NGFW resource. That’s it! No need to manage a myriad of UDRs or risk advertising something wrong via the BGP.
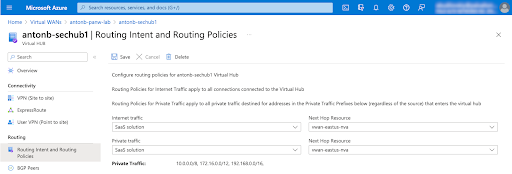
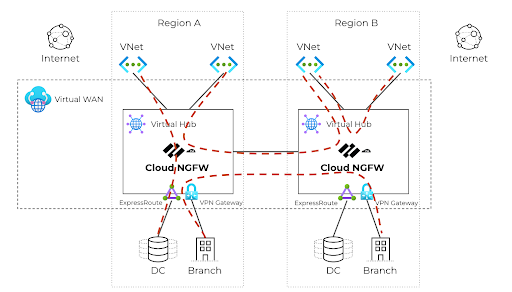
Cloud NGFW supports all VWAN traffic patterns including the ones listed below
Lateral Traffic Inspection
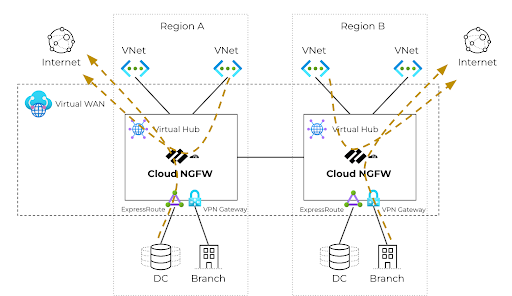
Outbound Traffic Inspection
On-prem/Branch/VPN-to-Internet - traffic from ExpressRoute and VPN connections routed through and inspected by the Cloud NGFW via the local virtual hub
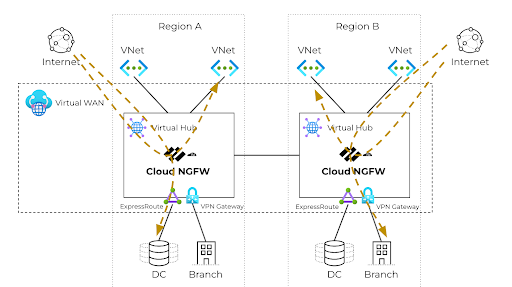
Inbound Traffic
With Cloud NGFW for Azure, your vWAN security is elevated to heights network security has simply not seen until now. You get the first-class security of a Palo Alto Networks Next Generation Firewall delivered as an easy-to-use managed service. There is no infrastructure to worry about. So let that pager be quiet and enjoy your weekends. You get to apply the same security policies used throughout your organization and its deployment whether on-prem or in the public cloud without complex integrations and multiple interfaces to wade through. And while we are at it, it’s the first NGFW natively integrated into vWAN Hub, which allows you to secure your vWAN deployment in a cloud-native way — while accepting no compromises for security itself.
Cloud NGFW for Azure is currently in public preview with a 30-day free trial available to anyone who’s looking to secure Azure vWAN with a Palo Alto Networks Next Generation Firewall.
References:
https://www.paloaltonetworks.com/network-security/cloud-ngfw-for-azure
https://docs.paloaltonetworks.com/cloud-ngfw/azure/cloud-ngfw-for-azure
https://learn.microsoft.com/en-us/azure/virtual-wan/how-to-palo-alto-cloud-ngfw
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
| Subject | Likes |
|---|---|
| 5 Likes Likes | |
| 5 Likes Likes | |
| 4 Likes Likes | |
| 3 Likes Likes | |
| 2 Likes Likes |
| User | Likes Count |
|---|---|
| 7 Likes | |
| 5 Likes | |
| 5 Likes | |
| 4 Likes | |
| 1 Likes |




