- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Threat Intelligence using MITRE ATT&CK and Cortex XSOAR
- LIVEcommunity
- Products
- Security Operations
- Cortex XSOAR
- Cortex XSOAR Articles
- Threat Intelligence using MITRE ATT&CK and Cortex XSOAR
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Printer Friendly Page
In today’s security landscape, there are three important players - threat actors with the intent, capability and opportunity to cause widescale disruption to business functions, defenders working to undermine attacks and safeguarding these business functions and assets, and people, who ultimately become privy to collateral damage as a result of compromises in security and privacy. Day by day, threat actors are becoming increasingly sophisticated with their methods, and the general perception is that defenses are not tracking at the same pace. The thought process behind this is that threat actors need only a single orifice to exploit, whereas defenders have a significantly larger surface area to cover. It is purely a numbers game. To level the playing field, organizations are realizing that the need to adopt a threat-informed defensive strategy becomes key. The ATT&CK framework, originally designed and developed by MITRE, and contributed to by the community, facilitates this approach.
What is MITRE ATT&CK?
The MITRE ATT&CK framework serves as a knowledge base of adversary tactics and techniques observed in the real world. It provides a common language for consumers to communicate with and understand threats, and lays the foundation for the development of specific threat models and prioritize defenses based on real-world, actionable intelligence. The ATT&CK framework has four primary use cases - Detection and Analysis, Threat Intelligence, Assessment and Engineering, and Adversary Emulation. For the sake of maintaining brevity, we are going to be focusing solely on how MITRE ATT&CK fits into the SOAR/TIM (Threat Intelligence Management) ecosystem.
A structured model such as ATT&CK offers a level of abstraction that is appropriate to bridge offensive action with possible defensive countermeasures. The framework can be used to cluster adversary activity across different intrusions, and to formulate patterns in adversary behavior, recording various threat groups, campaigns and intrusion sets. Analysts and defenders can better understand common behaviors across many groups and more effectively map defenses to them and ask questions such as “what is my defensive posture against adversary group APT3?” Understanding how multiple groups use the same technique behavior allows analysts to focus on impactful defenses that span many types of threats. The structured format of ATT&CK can add value to threat reporting by categorizing behavior beyond standard indicators.
Mapping to ATT&CK
For a defender beginning to work with MITRE, the most common yet non-trivial question that needs to be addressed is “How can I map my alerts to ATT&CK?”. As someone applies unstructured data to a structured framework such as ATT&CK, there are two key approaches - manual and automated, and normally, a combination of these approaches is required to effectively map threats.
Mapping to ATT&CK generally means the process of taking defensive artifacts like behavioral analytics or intel on adversary behaviors and assigning them to the applicable ATT&CK technique(s). The team at MITRE has illustrated these two approaches through their work on the Cyber Analytics Repository and Threat Report ATT&CK Mapper (TRAM).
Manual and automated approaches each have their pros and cons. While we can and should automate where we can, sometimes human judgment is needed to support machine generated results, or perform intricate analysis on threats. On the contrary, human analysis is prone to cognitive biases. To create the strongest analysis when mapping to ATT&CK, a hybrid approach combining efforts from humans and machines would be most effective. For example, with a technique like Rundll32 (T1085), it may be simple for a machine to map the executable rundll32.exe to that technique. However, for broader techniques like Masquerading, human analysis may be needed to determine if a malicious process is masquerading as a legitimate one like svchost.exe.
This discussion begets a question that automation engineers and analysts working on Cortex XSOAR pose very often - “How can XSOAR assist in mapping alerts to the ATT&CK framework?”. Although mapping exercises can be conducted using techniques described above, automating the mapping process can prove to be cumbersome on Cortex XSOAR. Custom mapping techniques using scripts can quickly become convoluted due to the sheer number of techniques and analytics that would have to be incorporated into the process. In addition, mapping exercises on XSOAR must be trivial and expedited so that much of the time is devoted towards executing workflows and investigating alerts. Often times, the malleable nature of Cortex XSOAR can be misunderstood for an all-encompassing solution, however, there are functions that are better suited to be handled upstream than to be dealt with on an orchestration platform such as Cortex XSOAR. If MITRE mappings are preemptively established, XSOAR can leverage these to develop correlations between alerts based on TTPs and remediate them using pre-built playbooks(refer to MITRE ATT&CK Courses of Action pack). This is where the power of the tool really comes through. The idea of leveraging Cortex XSOAR for correlation and visualization organically becomes attractive.
Threat Intelligence using XSOAR and MITRE ATT&CK
Why taking the time to carefully choose your feeds is critical,
When it comes to threat intelligence, security teams are often inclined to look at external sources that provide threat information, but a great place to start is by using your own incident reports and transcribing them to ATT&CK. Internal information on what adversaries have performed in relation to your environment can be extremely valuable to not only tune defenses but also chart trends on how much your defenses have strengthened over time, or how adversary behavior has evolved over time. Other sources of threat data such as IPs, Domains, Malware Samples, External Threat Feeds, TLS Certificates and open source code repositories are equally valuable, provided they are applicable to the type of threats your organization cares about, and whether this data can pivot to a higher order context. An IP or a Domain in itself provides less value, unless there is enough contextual information to validate the efficacy of the data. This applies more strongly to Cortex XSOAR, with it’s Threat Intel Aggregation and Correlation capabilities. Before you begin to configure an intel feed, it is imperative to evaluate it’s value proposition and compatibility with the data that your current tools are producing. Always ask questions such as - “Is this feed relevant to the threats that my company has to deal with? How reliable is this feed? Will this feed create a net positive effect towards our detection capabilities?”. Laying out all the key data points that a particular intel source monitors in a collection management framework can help you assess the extent of coverage your intelligence is currently offering. This exercise obviates the need to clean up your intelligence in the future resulting from inadequate planning.
MITRE ATT&CK Feeds
The MITRE ATT&CK feed in the MITRE ATT&CK pack and the Unit 42 ATOMS feed are particularly relevant here as the former generates Attack Patterns, Campaigns, Intrusion Sets and Malware names among others as indicators and the latter generates relationships with campaign indicator objects, ATT&CK patterns, IOCS related to campaigns and more importantly, mitigations for attack patterns.
Relationships are connections that enable investigators and threat intel analysts to expand the scope of the investigation with information about indicators and how they might be related to other incidents or indicator objects. Mitigations as relationship objects can enable you to take appropriate courses of action to remediate potential damage from corresponding threats (refer to MITRE ATT&CK Courses of Action pack).
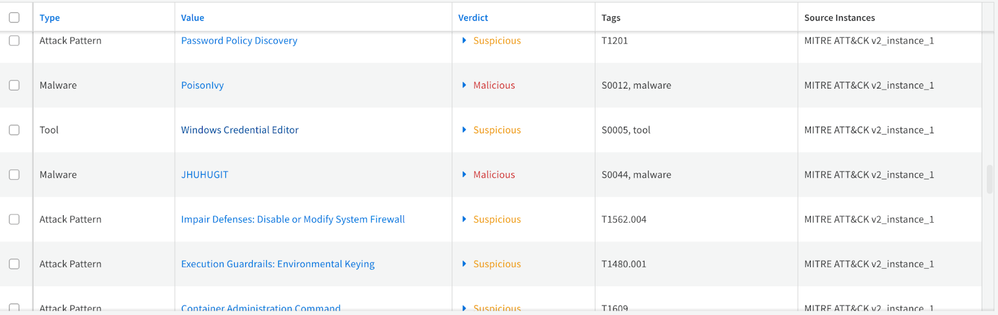 Indicators from MITRE ATT&CK feed
Indicators from MITRE ATT&CK feed
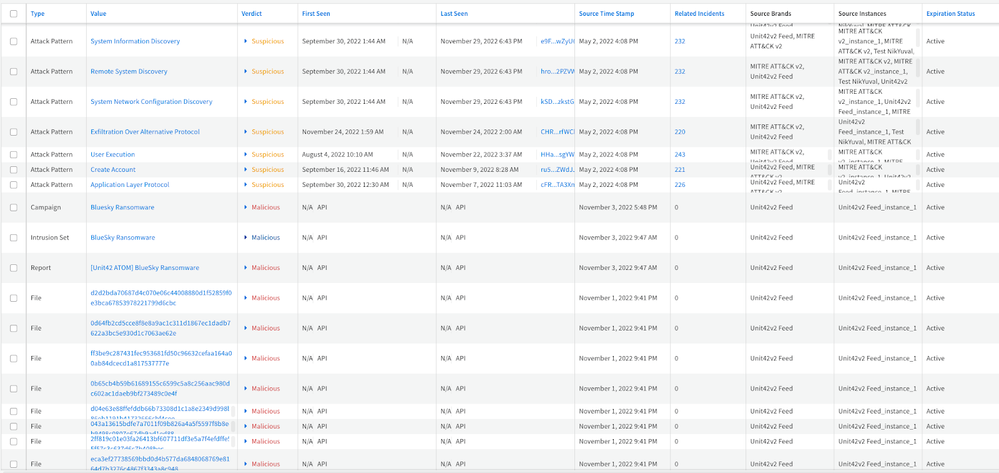 Indicators from Unit 42 ATOMS feed
Indicators from Unit 42 ATOMS feed
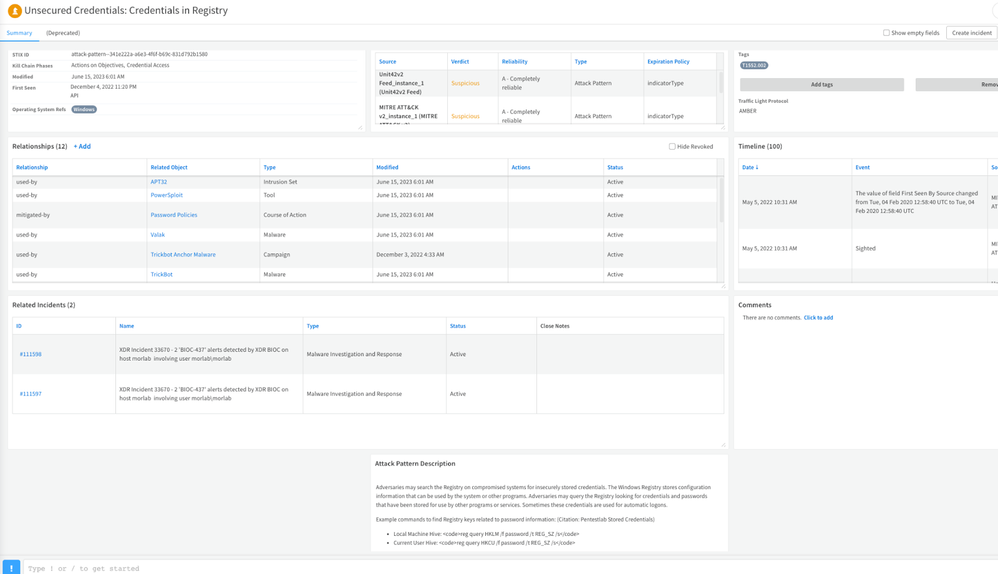 Attack Pattern indicator with relationships from Unit 42 ATOMS feed and related incidents (1)
Attack Pattern indicator with relationships from Unit 42 ATOMS feed and related incidents (1)
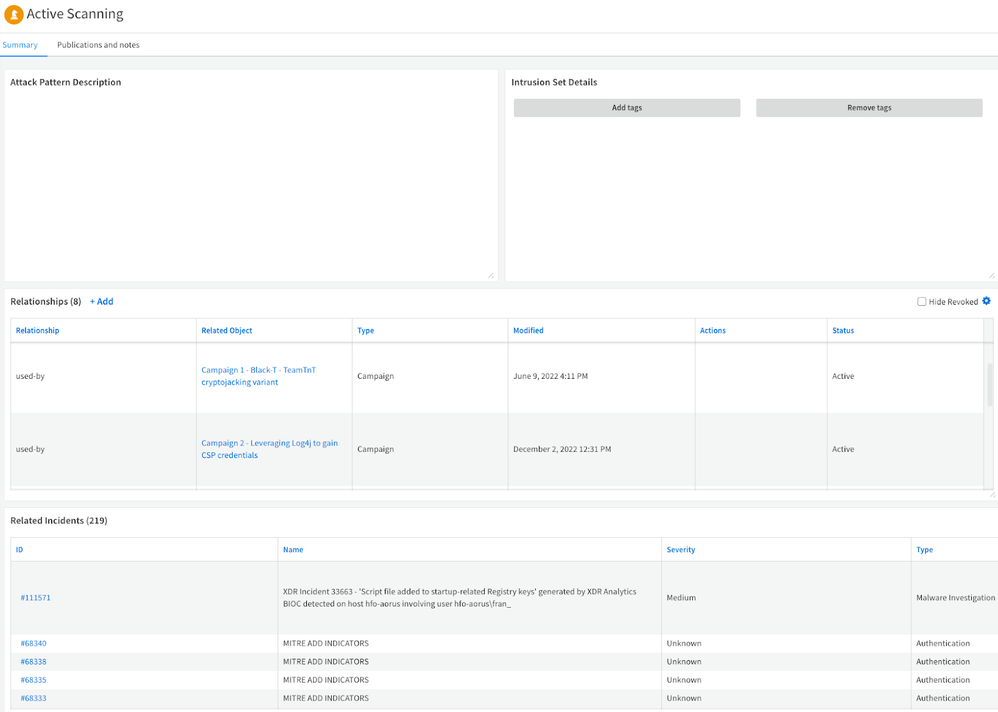 Attack Pattern indicator with relationships from Unit 42 ATOMS feed and related incidents (2)
Attack Pattern indicator with relationships from Unit 42 ATOMS feed and related incidents (2)
These feeds combined with mappings from alerting tools can prove to be really powerful to analyze behavioral patterns across alerts and generate visual components on dashboards for tracking these behaviors.
I hope this article provided some useful information on the application of MITRE ATT&CK within the context of Cortex XSOAR. Please feel free to contact your customer success team for more information or guidance on how to take advantage of the content mentioned in this article.
- 2129 Views
- 0 comments
- 3 Likes
- New Version of Cortex XSOAR 8 (8.6) Cloud is now GA in Cortex XSOAR Release Announcements
- Cortex XSOAR CS Newsletter April 2024 in Cortex XSOAR Articles
- Cortex XSOAR 8 On-prem is now GA in Cortex XSOAR Release Announcements
- Cortex XSOAR New Content Pack Release - March 24' in Cortex XSOAR Articles
- Cortex XSOAR CS Newsletter March 2024 in Cortex XSOAR Articles
-
Best Practice
1 -
ci cd
1 -
Configuration Guide
1 -
Content
3 -
Content Development
3 -
Content pack release
15 -
Content Updates
7 -
Coretx XSOAR
4 -
Cortex XDR
1 -
Cortex Xpanse
1 -
cortex xsaor
1 -
Cortex XSIAM
1 -
Cortex XSOAR
55 -
Cortex XSOAR Features
3 -
CS Newsletter
1 -
CVE-2021-32648
1 -
cybersecurity
1 -
Deployment Best Practices
1 -
Deployment Checklists
1 -
Deployment Monitoring
1 -
Integration
6 -
Investigation and Response
1 -
Marketplace
5 -
Marketplace XSOAR
3 -
microsoft
1 -
Migration
1 -
onboarding
1 -
Phishing
2 -
playbook
2 -
Playbook Creation
2 -
playbooks
3 -
Rapid Breach Response Program
1 -
Release Notes
2 -
Symphony
1 -
template
1 -
threat prevention
1 -
TIM 3.0
1 -
Tutorial
1 -
unit 42
1 -
use case
3 -
vulnerability
1 -
Vulnerability Protection
1 -
XSOAR
16 -
XSOAR 6.5
1 -
XSOAR 8
1
- Previous
- Next




