- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Empowering and Securing Banking and Financial Organizations
- LIVEcommunity
- Articles
- General Articles
- Empowering and Securing Banking and Financial Organizations
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-08-2023 07:48 PM - edited 08-27-2023 08:22 PM
Introduction
Digitization has revolutionized banking, empowering fintech firms to offer innovative services. Banks collaborate with fintech companies to enhance offerings and reach more customers. This shift is driven by the need to adapt to scalability and resiliency requirements. Cloud infrastructure enables banks to handle large volumes of data, support increased user traffic, and provide uninterrupted services.
Palo Alto Networks Software Firewall solutions, including VM Series, CN Series, and Cloud NGFW (FWaaS), enable the banking sector to embrace innovation and migrate to the cloud by seamlessly integrating security services into their existing architectures. These solutions empower banks to deploy robust security controls across public cloud, private cloud, and hybrid environments, ensuring consistent protection whether in the cloud or on-premises. This approach offers resiliency and scalability, addressing the dynamic requirements of the banking sector.
These firewalls can be deployed in an autoscale manner to ensure resiliency as the infrastructure grows. Additionally, the VM Monitoring capability enables automated policy enforcement through the use of Dynamic Address Groups (DAGs), minimizing manual effort and streamlining security policy management.
Furthermore, with Panorama, customers can benefit from centralized monitoring capabilities across on-premises and multi-cloud environments, providing a unified view of security across their infrastructure.
Palo Alto Networks VM-Series firewall empowers banks to embrace innovation and leverage cloud migration advantages. It delivers integrated security services, simplifies deployment, enhances resiliency, automates policy management, and enables centralized monitoring across diverse environments. With Palo Alto Networks VM- Series firewall, banks can confidently adopt cloud technologies while ensuring robust and streamlined security measures.
In this document, We will take an example of a deployment in the AWS environment and understand various use cases specific to Banking and Financial sectors and how Palo Alto networks security solutions can safeguard the environment.
The deployment below provides an approach to centralize the Inbound, Outbound and east-West traffic in Separate VPCs. This also depicts the most commonly deployed architecture. That being said, there could be multiple ways to design the architecture. Similar architecture can be adopted in other public clouds as well. Please refer to Reference Architectures to know more.
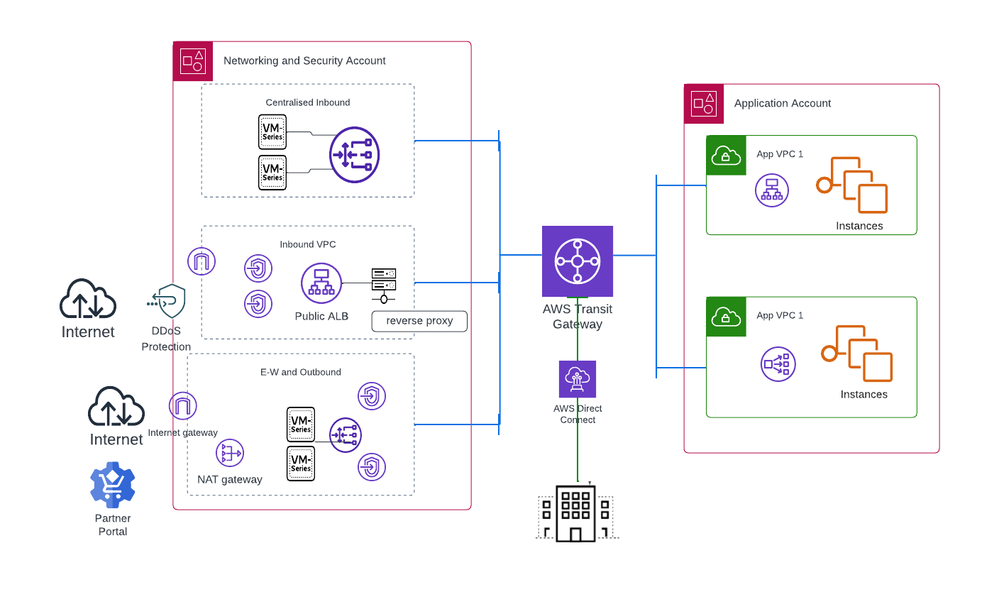
Banks, in their digitization journey, migrate their banking applications to cloud-based platforms, including payment applications, NetBanking applications, and loan management systems. These applications are accessed by end users through distinct domains and subdomains. Here are some of the common inbound use cases in Banks.
- Account Opening : During account opening and onboarding, banks utilize inbound traffic to collect and process customer information, identification documents, and other necessary details.
- Transactions: Inbound traffic for customer transactions includes online banking transfers, mobile banking transactions, and credit/debit card payments. Banks receive and process these transactions to update customer account balances and finalize financial transactions.
- Data Feeds and Market Updates: Banks receive inbound traffic in the form of real-time data feeds from stock exchanges, financial data providers, and market data vendors. This data includes stock prices, market indices, currency exchange rates, and other market-related information
- Customer Support and Communication: Inbound traffic includes customer inquiries, requests, and communications via channels like phone calls, emails, chatbots, or social media.
In order to comply with regulatory requirements and ensure comprehensive protection for these application workloads, it becomes necessary to implement layered security measures.
Several essential security services are typically employed in this context:To ensure comprehensive security in the BFSI sector, key measures include encryption for data protection, intrusion detection and prevention systems (IDPS) for threat mitigation, network firewalls and segmentation for controlled traffic, vulnerability management for addressing weaknesses, real-time security monitoring and incident response, data loss prevention (DLP) measures, and robust logging and auditing for compliance.
It is important for banks to continuously evaluate and enhance their security measures to adapt to evolving threats and maintain the integrity, confidentiality, and availability of their cloud-based banking applications.
By integrating Palo Alto Networks software firewalls with native security solutions, organizations can adopt a layered security approach that encompasses various essential components like -
- DDoS Service: The combined solution includes robust protection against Distributed Denial of Service (DDoS) attacks. This helps safeguard networks and infrastructure from malicious attempts to disrupt services by overwhelming them with excessive traffic
- WAF (Web Application Firewall): The solution incorporates a Web Application Firewall (WAF) that enhances security for web-based applications. It analyzes and filters incoming web traffic, detecting and mitigating potential threats, such as SQL injection or cross-site scripting attacks
- VM-Series (Next-Generation Firewall): The integration leverages the capabilities of a Next-Generation Firewall (NGFW). This advanced firewall technology goes beyond traditional firewall functionalities, providing deep packet inspection, application-level visibility, and granular control over network traffic
- Proxy: The combined solution also includes a reverse proxy component, which acts as an intermediary between internal network resources and external connections. This can perform port and protocol switching for resources in a private network
With the layered security approach, organizations can establish a comprehensive and multi-layered defense strategy to safeguard their networks, applications, and data from a wide range of cyber threats.
Let's take an example of architecture in figure 1, Customers can consider deploying a separate Centralized Ingress VPC with VM-Series behind gateway load balancer. The sequence of steps are as follows:
- User tries to access a banking portal to upload a document. For example- www.bank.com/app1
- Traffic after being inspected by DDoS, enters the Ingress VPC via IGW
- Route Table routes the traffic to GWLBe in Ingress VPC and forwards to VM- Series for inspection.
- GWLBe sends the inspected traffic to the public ALB, with no source IP change. ALB Forwards the traffic to one of the L7 Load Balancer/Reverse Proxy instances.
- LB/RP reads the host header/path and sends the traffic to the correct VPC / Private ALB
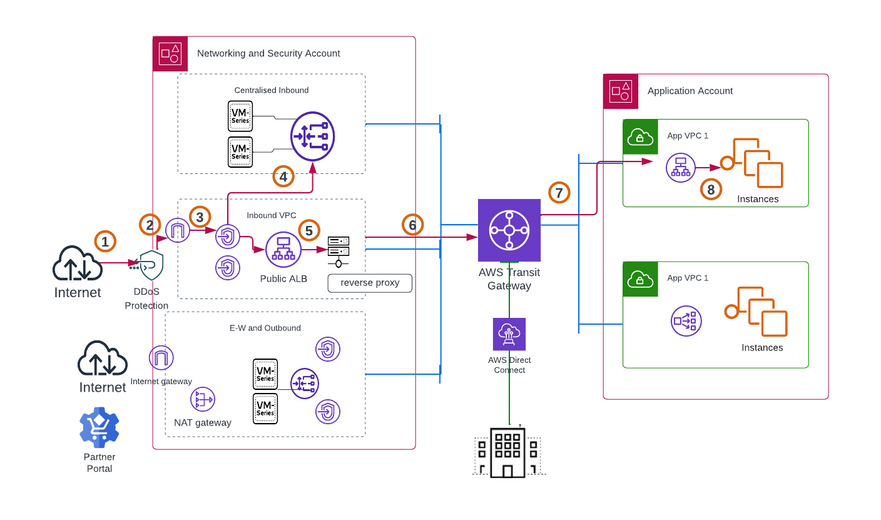
Figure 2
To safeguard inbound traffic, various security features can be enabled on the firewall. These include:
- Geo Location-Based Policy: This helps prevent unauthorized access and reduces the risk of potential threats from specific regions
- Application Control (App-ID) : NGFWs enable policy enforcement and control of inbound traffic based on specific applications. By identifying application characteristics, they can selectively allow or block traffic, ensuring that only authorized applications can access the network
- Decryption: Implementing decryption mechanisms allows for inspecting and analyzing encrypted inbound traffic. By decrypting the traffic, organizations can identify and mitigate potential threats or malicious activities hidden within encrypted communications
- Data Loss Prevention (DLP): Monitor inbound traffic for sensitive or confidential data entering the network. They can enforce policies to prevent the unauthorized transfer of sensitive information, such as credit card numbers, personal data, or intellectual property
- Advanced Threat Prevention: Utilizing advanced threat prevention measures enhances the security posture against sophisticated attacks. These measures employ various techniques, such as behavioral analysis, machine learning, and threat intelligence, to detect and prevent known and unknown threats
- External Dynamic Lists (EDLs): EDLs enable the use of external threat intelligence sources to block traffic from known malicious IP addresses or domains. This helps proactively protect the network by preventing communication with known malicious entities
- Advance WildFire: Wildfire subscription can detect and prevent advanced cyber threats, including malware, zero-day exploits, and other sophisticated attacks. This capabilities to scan inbound traffic for known malware signatures or behavior patterns. They can detect and block malicious files or attachments, protecting the network from potential malware infections
By enabling these security features, Banking and Financial organizations can strengthen their defense against potential inbound threats, enhance the security posture, and minimize the risk of unauthorized access or malicious activities targeting their networks and systems.
Providing Outbound Control
Outbound traffic can vary in terms of its destinations and requirements. Banking and Financial organizations use outbound traffic to transfer data transmitted from a bank's internal network to external systems or services. Banks utilize outbound traffic for various use cases, including:
- Payment Processing: Banks transmit payment instructions and data to external processors and financial institutions via outbound traffic for secure transactions. For example- such as SWIFT messages for international transfers
- Market Data and Trading: For trading activities, banks access real-time market data feeds from stock exchanges and financial providers using outbound traffic
- Card Processing: Banks communicate with card networks and payment processors for transaction authorization, fraud checks, and payment settlement through outbound traffic
- External Services Integration: Banks integrate with third-party services such as CRM platforms, fraud detection systems, and identity verification providers. Outbound traffic is used to exchange data and interact with these external services
- Regulatory Reporting: Banks transmit regulatory reports, including financial statements and transaction information, to regulatory bodies through outbound traffic
- Interbank Communication: Banks securely exchange information with other financial institutions for interbank transfers, correspondent banking, and regulatory reporting using outbound traffic
In all these cases, banks need to ensure the security, integrity, and confidentiality of outbound traffic. Several security requirements should be considered to maintain a secure environment. Such as-
- Secure Connectivity: Establish secure connections between the bank's on-premises infrastructure and the public cloud through encrypted communication channels, such as using VPN (Virtual Private Network) or dedicated private connections
- Network Segmentation: Implement network segmentation in the public cloud to separate services, applications, and data, limiting the impact of security breaches and improving control over outbound traffic flows
- Intrusion Detection and Prevention: To safeguard against security threats, such as unauthorized access attempts or malicious activities, deploy intrusion detection and prevention systems (IDPS). These systems actively monitor outbound network traffic, enabling the detection and prevention of potential security incidents
- Data Loss Prevention (DLP): Implement data loss prevention mechanisms to monitor and control outbound data flows. DLP solutions help identify and prevent the transmission of sensitive data that violates security policies, ensuring that confidential information is not leaked or exposed
- Logging and Monitoring: Implement a centralized logging system and SIEM solution to collect and analyze detailed logs of outbound traffic. This enables proactive detection of security incidents, identification of patterns, and timely response to potential threats. Monitor outbound traffic for suspicious activities, policy violations, or unauthorized access attempts, promptly investigating any anomalies
- Compliance and Regulations: Ensure compliance with relevant security standards, industry regulations, and data protection requirements, such as PCI DSS (Payment Card Industry Data Security Standard) or GDPR (General Data Protection Regulation). Implement necessary controls to protect customer data and maintain regulatory
- Network Traffic Monitoring: Continuously monitor outbound network traffic for anomalies, unusual behavior, or signs of potential security breaches. Use network traffic monitoring tools to identify any suspicious outbound connections or abnormal data transfer patterns
- Secure DNS: Implement secure Domain Name System (DNS) services or DNS filtering solutions to protect against DNS-based attacks, such as DNS hijacking or domain spoofing. Secure DNS helps ensure that outbound traffic is directed to legitimate and trusted destinations
- Web Proxy: Deploying a web proxy server enables the implementation of web traffic filtering. Proxy servers serve as intermediaries between users and the internet, handling communications with websites on behalf of users, providing an additional layer of security and privacy
Considering the deployment example in this document, Let us consider an example of traffic flow in AWS environment
- Traffic originates from VPC to the Partner website towards the internet. For example, a notification to a partner portal about a successful payment. Based on the VPC route table entry, The traffic is forwarded to the TGW Attachment
- TGW attachment hands off traffic to GWLBe. GWLBe sends traffic for inspection by VM-Series in outbound VPC
- Post Security inspection, PANW sends traffic back to GWLBe. GWLBe routes traffic to NAT Gateway. NAT Gateway Sends traffic out towards the destination
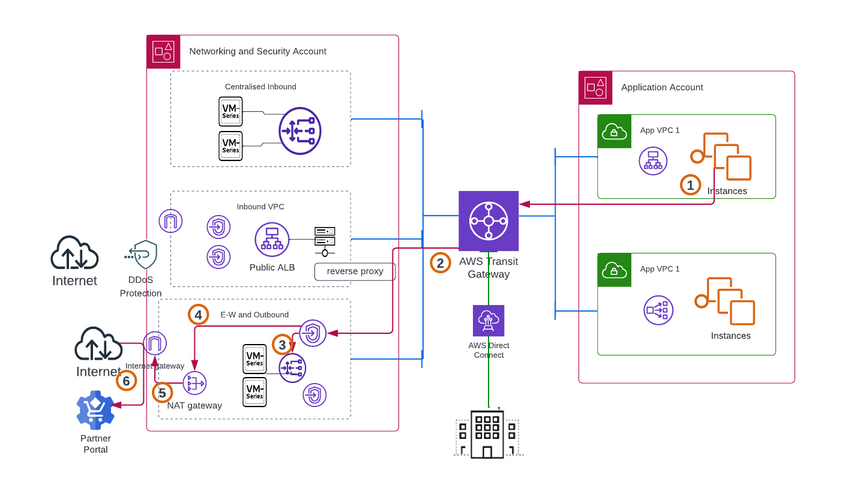
Figure 3
The VM-Series firewall offers several security capabilities that can be enabled for outbound protection:
- Advanced Wildfire: By enabling Advanced Wildfire, the firewall can analyze suspicious files and identify potential malware or unknown threats. This proactive approach helps in detecting and preventing outbound communications associated with malicious activities. It can block outbound connections to malicious domains, detect and quarantine infected files, and prevent the spread of malware within the network
- App-ID: The firewall's App-ID feature allows for the identification and control of applications used in outbound traffic. It provides granular visibility and control over application usage, helping to enforce policies and prevent unauthorized or risky applications from accessing the network
- Advanced URL Filtering: Enabling Advanced URL Filtering enhances outbound security by controlling and monitoring web traffic. The firewall can enforce policies based on URL categories, ensuring that users access only authorized websites and protecting against malicious or inappropriate content
- DNS Security: By enabling DNS security capabilities, the firewall can protect against DNS-based attacks and enforce policies for outbound DNS traffic. It helps prevent communication with malicious domains, detects and blocks DNS tunneling attempts, and ensures the integrity and availability of DNS services
- SSL/TLS Inspection: SWFW can decrypt and inspect encrypted outbound traffic to detect potential threats hidden within encrypted communications. This allows for the detection of malicious content or activities that may otherwise go unnoticed
- Advanced Threat Prevention: SWFW can identify and block outbound traffic associated with known and unknown malicious traffic. It can inspect outbound traffic for known attack signatures and anomalous behavior. They can detect and prevent outbound network attacks, providing an additional layer of protection against threats targeting the network perimeter
- Data Loss Prevention (DLP): SWFWs can monitor outbound traffic for sensitive or confidential data leaving the network. And enforce policies to prevent the unauthorized transmission of sensitive information, such as credit card numbers, personal data, or intellectual property
- Performance and Scalability: In addition to the aforementioned security controls, SWFWs can be implemented in both public and private cloud environments to accommodate infrastructure expansion in a scalable manner, ensuring optimal performance
By leveraging these security capabilities on the Software Firewalls, organizations can establish robust outbound protection, effectively monitor and control application usage, safeguard against web-based threats, and enhance the security posture of their networks.
Protect East-West and On-Prem Traffic
In banks, east-west communication refers to the exchange of data and communication between different systems and services within the organization's network. Here are some common use cases for east-west communication in banks:
- Internal Service Integration: Banks often have multiple internal systems and services that need to communicate with each other. For example, the integration of customer relationship management (CRM) systems with core banking systems or loan origination systems
- Interdepartmental Communication: Different departments within a bank, such as retail banking, wealth management, or risk management, may need to share data and collaborate on various initiatives
- Workflow Orchestration: Banks often have complex business processes that involve multiple systems and services working together. This ensures efficient and coordinated execution of critical processes such as loan approval, payment processing, or account opening
- Security and Compliance: In a public cloud environment, east-west communication plays a crucial role in ensuring security and compliance. Banks can implement security controls, such as network segmentation and traffic monitoring, to protect sensitive data and prevent unauthorized access between different services and components
To ensure secure communication between workloads deployed in the cloud and on-premises deployments, Palo Alto Networks Software Firewall solution can be deployed in scalable and resilient architecture. For example, consider the figure 4 below, where we have deployed VM-Series firewalls in AWS in a centralized architecture.. This setup utilizes a Transit Gateway to facilitate connectivity and routing capabilities for traffic movement.
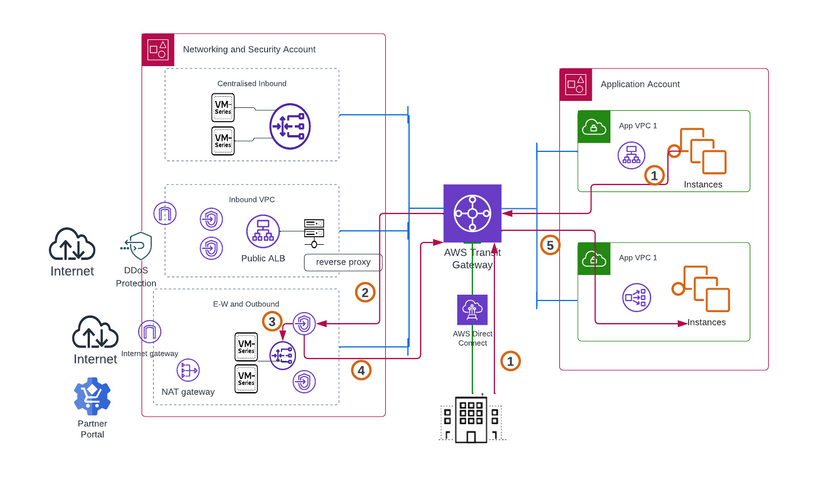
Figure 4
In the architecture diagram in figure 4, when an application in the on-premises environment or within a specific VPC needs to communicate with an application in another VPC, the traffic is directed towards the Transit Gateway from the source. The Transit Gateway then forwards the traffic to the inspection VPC, where security checks are performed.
After the security checks are completed, the traffic is routed back to the Transit Gateway, which then forwards it to the destination based on the defined route table. This process ensures that the traffic undergoes necessary security measures before reaching its intended destination. The security controls which can be enabled are -
- Application Security: Application-level visibility and control, allowing banks to enforce security policies based on specific applications. They can identify and block unauthorized applications or suspicious behavior within east-west traffic, ensuring that only legitimate and authorized applications communicate with each other
- Traffic Inspection: Inspect east-west traffic to detect and block malicious content, malware, or unauthorized communications. They can analyze traffic patterns, apply security rules, and filter out potentially harmful or non-compliant traffic, preventing the spread of threats within the network
- Threat Protection: NGFWs can detect and prevent intrusion attempts within the bank's network. By analyzing east-west traffic for known attack patterns, suspicious activities, or malicious behavior, NGFWs can identify and block unauthorized access attempts or prevent lateral movement of threats
These measures help safeguard critical systems, data, and applications from unauthorized access, malicious activities, and emerging threats.
Protecting Cloud Native Workload
Banks can embrace a microservices architecture in the public cloud, decoupling various services and enabling flexible, scalable, and agile deployment and management of banking services. Kubernetes serves as a suitable platform for hosting DevOps and CI/CD tools, empowering banks to automate software development, testing, and deployment processes.
To ensure network security within the Kubernetes cluster for the containerized applications, Palo Alto Networks CN-Series firewalls can be deployed. CN-Series provides full Layer-7 visibility and comprehensive security for containerized apps providing visibility and control to safeguard banking systems and data.
Deploying PaloAlto's container firewalls allows banks to eliminate blind spots in their environment that cannot be ensured by deploying a network firewall outside the cluster. These can dynamically scale without compromising DevOps speed and agility.
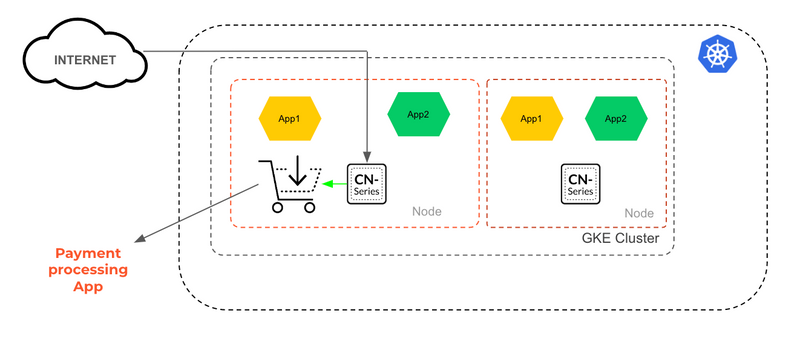
Figure 5
As shown in the figure 5, Banks can secure specific applications/namespaces only with stricker policy and not all the applications on the cluster. It also enables them to achieve PCI compliance by enforcing strict policy only for Payment Processing applications.
Network security teams can prevent threats riding in the container environment with our Threat Prevention and Wildfire malware analysis services.
MultiCloud and Hybrid Deployment
Banks often adopt the practice of using multiple cloud service providers to host different applications, services, or components of the bank's infrastructure. By adopting a multi-cloud strategy, banks can leverage the unique features and capabilities offered by different cloud providers. Also, it enables banks to implement robust disaster recovery and business continuity strategies
At the same time, deploying banking services across multiple cloud providers ensures high availability and resilience. In the event of an outage or disruption, banks can swiftly switch to another provider, minimizing customer impact and ensuring uninterrupted operations.
It is essential to design a robust and secure network architecture while connecting a multicloud environment in banks. Banks should consider their specific requirements, performance needs, security considerations, and compliance obligations when selecting and implementing connectivity solutions for their multi cloud environment.
There can be multiple ways of connecting-
- Connection via VPN
- Connecting with private link
- Connecting via a 3rd party edge solution
Below is one of the examples for connecting an AWS and Azure environment along with on-prem connectivity. direct connect services establish private and high-bandwidth connections between the bank's on-premises infrastructure and multiple cloud providers. This provides a reliable and low-latency connection for data transfer and application access. Multicloud networking services provide networking capabilities, such as load balancing and traffic routing to ensure efficient and secure connectivity between clouds.

Unified Management with Panorama:
Palo Alto Networks Panorama offers unified management for banks operating in a multicloud environment. With Panorama, banks can centrally manage and control security policies, configurations, and monitoring across multiple cloud environments. This provides a streamlined and consistent approach to security management, allowing banks to efficiently deploy and enforce security measures, monitor network activity, detect and respond to threats, and ensure compliance across their multicloud infrastructure. With Panorama, a single management console can be used to oversee and control the configuration, policies, and monitoring of Palo Alto Networks Firewalls, regardless of their deployment location.
Telemetry Insights with AI/ML Powered AIOps
Banking and Financial customers can use AIOps solution, which is a cloud based module for their fleet of Hardware Firewalls , VM-Series and Panorama deployments. AIOps for NGFWs enhance firewall operational experience with comprehensive insights to proactively strengthen security posture and maintain deployment health.
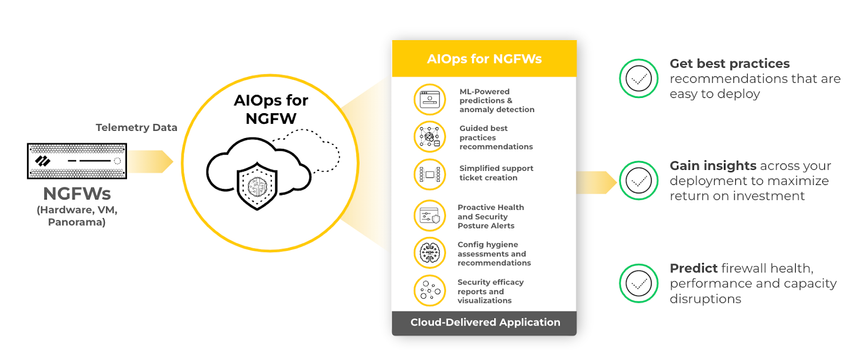
Few use cases for this solution are-
- Continuously improve security posture by optimizing configuration to the dynamic environment, based on best practices and policy recommendations. Based on the policies you have turned ON, example, if you are not using Decryption or one of the security services, AIOps will tell you that you are not using those capabilities OR if you are not using the right profile, e.g., antispyware profile, we will tell you what is the best practice you should be using. Because the telemetry data is going back to us, we can tell what the customer is using and not using, where they are in terms of the best practice usage. This we believe will help improve the security posture of all the customers as they will get in-console best practice recommendations which will be easy to incorporate into their panorama devices
- Empower network security operations teams to become proactive with ML-powered anomaly detection, and actionable insights into the health and performance of the entire deployment. Customers will be able to predict any failures before they happen. If a firewall is going to reach capability, it will be able to predict that before it happens and customers will be able to take predictive action
Automation
For enhanced deployment flexibility, Palo Alto Networks offers infrastructure as code capabilities. This empowers our customers with the freedom to utilize terraform samples conveniently accessible through our official GitHub repository.- Palo Alto Networks VM-Series -GitHub Location
Policy as code: Banks are increasingly seeking to minimize the manual operational tasks involved in policy and infrastructure changes. Manual operations not only result in higher costs but also carry a higher risk of human error and non-standardized implementations. In order to mitigate security risks and establish standardized operations, banks can embrace the implementation of policy as code for firewalls deployed across their various environments.
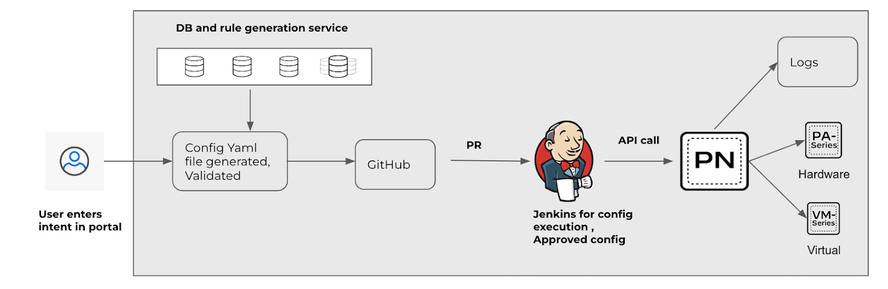
Figure 7
This solution creates an automated framework and uses CI/CD pipeline for any change in the environment. The recommendation is to leverage Device Group and Object Group Hierarchy
This solution involves -
- Playbook - NW Engineers /Support Engineers create playbooks based on Policies , objects, upgrades Which resides in a DB and is used for rule generation.
- Config Validation - Validation of config for new rules/ existing rules/ object creation/ syntax error/ update etc are in place. Pre checks and post checks are part of the config file generation. Bad configurations are avoided.
- Test and Push to Production Panorama - config can be pushed to lab panorama to check for any issues. The PR is then approved before sending to Production panorama.
- Notification- Automated response and email alerts can be configured for changes.
Summary
By deploying Software Firewalls in a banking environment, organizations can establish a secure communication framework, enabling traffic between cloud-based workloads and on-premises deployments while ensuring that security checks are enforced. This architecture enhances the overall security posture and facilitates controlled and protected data exchange within the hybrid environment.
Palo Alto Networks firewalls provide deployment flexibility and support infrastructure expansion with native autoscaling services. VM monitoring can be used for automated policy enforcement. Panorama provides centralized monitoring across on-premises and multi-cloud environments. The CDSS subscriptions ensure zero trust by providing protection against known and unknown threats in the network. Overall, these features empower banks to enhance security, simplify management, and embrace the benefits of cloud migration.
- centralized monitoring
- Cloud NGFW
- CN Series
- Configuration
- Configure
- Firewall
- next generation
- NGFW
- Software Firewall
- vm series
- 8284 Views
- 0 comments
- 1 Likes
-
"Address Objects"
1 -
10.0
2 -
10.1
2 -
10.2
3 -
8.1
1 -
9.0
1 -
9.1
1 -
ACC
1 -
Active-Passive
1 -
AD
1 -
address objects
1 -
admin roles
1 -
Administration
6 -
Administrator Profile
1 -
Advanced URL Filtering
2 -
Advanced WildFire
1 -
Alibaba
2 -
Alibaba Cloud
3 -
Ansible
1 -
antivirus
1 -
API
2 -
applications
2 -
APS
1 -
Asset Management
1 -
Authentication
6 -
Authentication Profile
1 -
Authentication Sequence
1 -
automatically acquire commit lock
1 -
Automation
3 -
AWS
6 -
Azure
1 -
Basic Configuration
4 -
Beacon
2 -
Beacon2020
1 -
Best Practices
5 -
Block List
1 -
categories
1 -
certificates
1 -
Certification
1 -
Certifications
1 -
Certifications & Exams
1 -
CLI
4 -
CLI command
3 -
Cloud Automation
1 -
Cloud Identity Engine
1 -
Cloud NGFW
1 -
Cloud Security
1 -
Collector Group
1 -
Commit Process
1 -
community news
1 -
Configuration
9 -
Configuration and Management
2 -
Configure Next Generation Firewall
1 -
console
1 -
Cortex
1 -
Cortex Data Lake
2 -
Cortex XDR
5 -
COVID-19
1 -
CPSP
1 -
Custom Signatures
1 -
cyber elite
1 -
Cyberelite
11 -
dag
2 -
Debug
1 -
debugging
2 -
Default Policy
1 -
Deployment
1 -
discussions
1 -
EDL
3 -
education
2 -
Education and Training
2 -
Education Services
2 -
Educational Services
1 -
Effective Routing
1 -
Endpoint
1 -
ESXi
1 -
events
1 -
Expedition
1 -
export
1 -
failover
1 -
FAQ
1 -
Filtering
2 -
Firewall
3 -
Firewall VM-Series
2 -
Focused Services
3 -
Focused Services Proactive Insights
2 -
gateway
1 -
Gateway Load Balancer
3 -
Gateway Loadbalancer
2 -
GCP
5 -
GCP Firewall
1 -
geolocation
1 -
Getting Started
1 -
GitHub
1 -
Global Protect
1 -
Global Protect Cookies
1 -
GlobalProtect
8 -
GlobalProtect App
1 -
globalprotect gateway
1 -
GlobalProtect Portal
2 -
google
2 -
Google Cloud
3 -
google cloud platform
4 -
GWLB
3 -
Hardware
2 -
hash
1 -
Header Insertion
1 -
High Availability
1 -
How to
1 -
HTTP
1 -
https
1 -
Hybrid Cloud
1 -
ike
3 -
import
1 -
Installation & Upgrade
1 -
IoT
2 -
IoT Security
1 -
IPSec
4 -
IPSec VPN Administration
1 -
kerberos
1 -
Kubernetes
1 -
Layer 2
2 -
Layer 3
1 -
Learning
1 -
licenses
1 -
local user
3 -
Log Cluster Design
1 -
Log Collection
2 -
Log Collector Design
2 -
Log Forwarding
1 -
Log4Shell
1 -
Logging
2 -
login
1 -
Logs
3 -
Malware
1 -
Management
8 -
Management & Administration
5 -
MFA
1 -
Microsoft
2 -
Microsoft 365
1 -
Migration
1 -
minemeld
24 -
multi factor authentication
1 -
multi-factor authentication
1 -
multi-vsys
1 -
NAT
1 -
NetSec
1 -
NetSec Newsletter
1 -
network security
37 -
network-security
1 -
Networking
1 -
New Apps
1 -
News
1 -
newsletter
2 -
Next Generation Firewall
4 -
Next-Generation Firewall
43 -
next-generation firewall. network security
1 -
Next-Generation Firewall. NGFW
5 -
NGFW
28 -
NGFW Configuration
11 -
NGFW Newsletter
1 -
Nominated Discussion
1 -
Objects
2 -
Oracle Cloud
1 -
Oracle Cloud Infrastructure
1 -
OTP
1 -
PA-3200 Series
1 -
PA-400
1 -
pa-440
2 -
PA-5400 series
1 -
PA-800 Series
1 -
pa-820 firewall
1 -
Packet Buffer
1 -
packet debug
1 -
packet diag
1 -
PAN-OS
19 -
PAN-OS 10.2
1 -
PAN-OS 11.0
1 -
PAN-OS 9.1
1 -
PAN-OS Prisma Access
1 -
Panorama
11 -
Panorama 8.1
1 -
Panorama 9.1
1 -
Panorama Configuration
2 -
Panorama HA
1 -
PBF
1 -
PCNSA
2 -
PCNSE
2 -
performance
2 -
policies
2 -
policy
3 -
Policy Based Forwarding
1 -
Prisma
1 -
prisma access
5 -
Prisma SD-WAN
1 -
proactive insights
2 -
QRadar
1 -
Radius
1 -
Ransomware
1 -
region
1 -
Registration
1 -
Release Notes
1 -
reporting and logging
1 -
RestAPI
1 -
Risk Management
1 -
Routing
1 -
SAML
1 -
SASE
2 -
script
2 -
SD WAN
1 -
SD-WAN
1 -
SDWAN
1 -
Search
1 -
Security Advisory
1 -
Security automation
1 -
security policy
4 -
security profile
1 -
Security Profiles
2 -
Session Packet
1 -
Setup & Administration
8 -
Site-to-Site VPN
1 -
Split Tunneling
1 -
SSL
1 -
SSL Decryption
2 -
SSL Forward Proxy
1 -
SSO
1 -
Strata Logging Service
2 -
Support Guidance
1 -
syslog
1 -
Tag
2 -
tags
2 -
Terraform
2 -
TGW
3 -
Threat
1 -
threat log
1 -
Threat Prevention
2 -
Threat Prevention License
1 -
Threat Prevention Services
1 -
Tips & Tricks
2 -
tls
1 -
traffic_log
1 -
Transit Gateway
1 -
Traps
1 -
Troubleshoot
2 -
Troubleshoot. logs
1 -
troubleshooting
5 -
tunnel
2 -
Tutorial
2 -
Ubuntu 16.04
1 -
Unified Monitoring
1 -
Upgrade
2 -
upgrade-downgrade
3 -
url categories
1 -
URL Filtering
2 -
URL-Filtering
1 -
User ID Probing
1 -
User-ID
1 -
User-ID & Authentication
1 -
User-ID mapping
1 -
userid
1 -
VM Series
1 -
VM-Series
15 -
VM-Series on AWS
7 -
VM-Series on GCP
2 -
VPC Flow logs
1 -
VPN
2 -
VPNs
4 -
Vulnerability
2 -
Vulnerability Protection
1 -
Webinar
1 -
WildFire
3 -
Wildfire License
1 -
wmi
1 -
XDR
1 -
xml
2 -
XML API
2





