- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Nominated Discussion - Automatically blocking IP's after a certain number of Global Protect pre-login failures?
- LIVEcommunity
- Articles
- General Articles
- Nominated Discussion - Automatically blocking IP's after a certain number of Global Protect pre-login failures?
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Printer Friendly Page
This Nominated Discussion Article is based on the post "Automatically blocking IP's after a certain number of Global Protect pre-login failures? " by @RSteffens and answered by Cyber Elite @BPry and @usanitary. Read on if you are curious about how protecting your GP from brute force attacks!
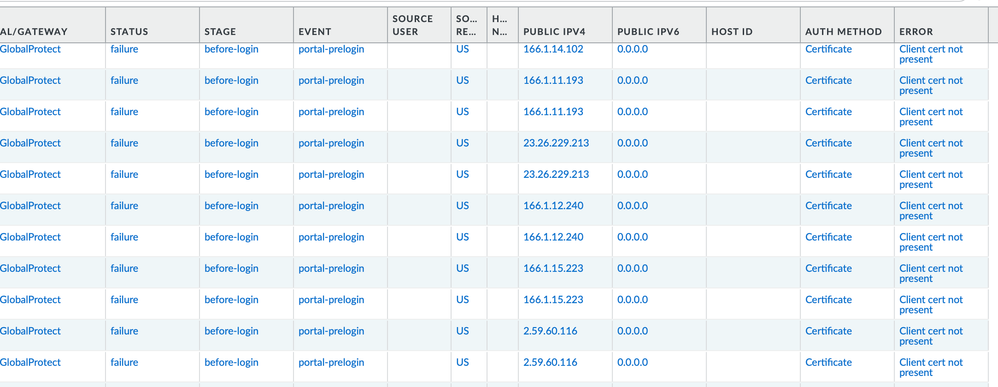
I've just recently started getting blasted with Global Protect portal pre-login failures, coming from a bunch of illegitimate IP's. They all fail because I use certificate authentication and the client cert is not present on the attacker's device. I have have the NGF set up to email me every time this happens and I'm getting just blasted with emails. I only use Global Protect for remote management.
See screenshot of some of the IP's attempting to gain access. I keep blocking IP's but then the attacker uses new ones.
My question is, is there a way to automatically block IP's after a certain number of Global Protect pre-login failures?
Automatic remediation of failed logins is something that I always script through the API. The easiest way to do that is creating a custom report on the firewall and using the API to collect the report on a scheduled basis. Have the script parse the IPs that are failing to login and add it to an EDL that you have configured to on the firewall and create a security rulebase entry to drop all traffic from any IP address located within the EDL.
I am new to scripting and the API. Where do you go on the firewall for this? I have found this type of traffic and would sure like to get it blocked a different way then manually blocking them one at a time.
Here's an article that describes the steps to configure a security policy to block brute force attacks (excessive number of login attempts in a sort period) on the GlobalProtect Portal page without having to know any scripting:
Detecting Brute Force Attack on GlobalProtect Portal Page - Knowledge Base - Palo Alto Networks
- 831 Views
- 0 comments
- 0 Likes
-
"Address Objects"
1 -
10.0
2 -
10.1
2 -
10.2
3 -
8.1
1 -
9.0
1 -
9.1
1 -
Active-Passive
1 -
AD
1 -
address objects
1 -
admin roles
1 -
administration
6 -
Administrator Profile
1 -
Advanced URL Filtering
2 -
Alibaba
2 -
Alibaba Cloud
3 -
Ansible
1 -
antivirus
1 -
API
2 -
applications
1 -
Asset Management
1 -
Authentication
6 -
Authentication Profile
1 -
Authentication Sequence
1 -
automatically acquire commit lock
1 -
Automation
3 -
AWS
6 -
Azure
1 -
Basic Configuration
4 -
Beacon
2 -
Beacon2020
1 -
Best Practices
2 -
Block List
1 -
categories
1 -
certificates
1 -
Certification
1 -
Certifications
1 -
Certifications & Exams
1 -
Chrome Search Extension
1 -
CLI
4 -
CLI command
3 -
Cloud Automation
1 -
Cloud Identity Engine
1 -
Cloud NGFW
1 -
Cloud Security
1 -
Commit Process
1 -
Community News
1 -
Configuration
9 -
Configure Next Generation Firewall
1 -
console
1 -
Cortex
1 -
Cortex Data Lake
2 -
Cortex XDR
4 -
COVID-19
1 -
cyber elite
1 -
Cyberelite
11 -
dag
2 -
Debug
1 -
debugging
1 -
Default Policy
1 -
Deployment
1 -
discussions
1 -
EDL
3 -
Education
2 -
Education and Training
2 -
Education Services
2 -
Educational Services
1 -
Effective Routing
1 -
Endpoint
1 -
ESXi
1 -
events
1 -
expedition
1 -
export
1 -
failover
1 -
FAQ
1 -
Filtering
2 -
Firewall
2 -
Firewall VM-Series
2 -
gateway
1 -
Gateway Load Balancer
3 -
Gateway Loadbalancer
2 -
GCP
5 -
GCP Firewall
1 -
geolocation
1 -
Getting Started
1 -
Github
1 -
Global Protect
1 -
Global Protect Cookies
1 -
GlobalProtect
8 -
GlobalProtect App
1 -
globalprotect gateway
1 -
GlobalProtect Portal
2 -
google
2 -
Google Cloud
3 -
google cloud platform
4 -
GWLB
3 -
Hardware
2 -
hash
1 -
Header Insertion
1 -
High Availability
1 -
How to
1 -
HTTP
1 -
https
1 -
Hybrid Cloud
1 -
ike
3 -
import
1 -
Installation & Upgrade
1 -
IoT
2 -
IoT Security
1 -
IPSec
3 -
kerberos
1 -
Kubernetes
1 -
Layer 2
2 -
Layer 3
1 -
Learning
1 -
licenses
1 -
local user
3 -
log forwarding
1 -
Log4Shell
1 -
Logging
1 -
login
1 -
Logs
2 -
Malware
1 -
Management
8 -
Management & Administration
5 -
MFA
1 -
microsoft
2 -
Microsoft 365
1 -
minemeld
25 -
multi factor authentication
1 -
multi-factor authentication
1 -
multi-vsys
1 -
Network Security
37 -
network-security
1 -
Networking
1 -
New Apps
1 -
News
1 -
next-generation firewall
42 -
next-generation firewall. network security
1 -
Next-Generation Firewall. NGFW
4 -
NGFW
21 -
NGFW Configuration
10 -
Objects
2 -
Oracle Cloud
1 -
Oracle Cloud Infrastructure
1 -
OTP
1 -
PA-3200 Series
1 -
PA-400
1 -
pa-440
2 -
PA-5400 series
1 -
PA-800 Series
1 -
pa-820 firewall
1 -
Packet Buffer
1 -
packet debug
1 -
packet diag
1 -
PAN-OS
17 -
PAN-OS 10.2
1 -
PAN-OS 11.0
1 -
PAN-OS 9.1
1 -
Panorama
7 -
Panorama 8.1
1 -
Panorama 9.1
1 -
Panorama Configuration
2 -
Panorama HA
1 -
PBF
1 -
PCNSA
2 -
PCNSE
2 -
policies
2 -
policy
3 -
Policy Based Forwarding
1 -
Prisma
1 -
Prisma Access
5 -
Prisma SD-WAN
1 -
QRadar
1 -
Radius
1 -
Ransomware
1 -
region
1 -
Registration
1 -
Release Notes
1 -
reporting and logging
1 -
Routing
1 -
SAML
1 -
SASE
2 -
script
2 -
SD WAN
1 -
SD-WAN
1 -
SDWAN
1 -
Search
2 -
Security Advisory
1 -
Security automation
1 -
security policy
4 -
security profile
1 -
Security Profiles
2 -
Session Packet
1 -
Setup & Administration
7 -
Site-to-Site VPN
1 -
Split Tunneling
1 -
SSL
1 -
SSL Decryption
2 -
SSL Forward Proxy
1 -
SSO
1 -
Strata Logging Service
2 -
Support Guidance
1 -
syslog
1 -
Tag
2 -
Tags
2 -
Terraform
2 -
TGW
3 -
threat log
1 -
threat prevention
2 -
Threat Prevention License
1 -
Threat Prevention Services
1 -
Tips & Tricks
2 -
tls
1 -
traffic_log
1 -
Transit Gateway
1 -
Traps
1 -
Troubleshoot
2 -
Troubleshooting
4 -
tunnel
1 -
Tutorial
2 -
Ubuntu 16.04
1 -
Unified Monitoring
1 -
upgrade
2 -
upgrade-downgrade
3 -
url categories
1 -
URL Filtering
2 -
URL-Filtering
1 -
User ID Probing
1 -
User-ID
1 -
User-ID & Authentication
1 -
User-ID mapping
1 -
userid
1 -
VM Series
1 -
VM-Series
15 -
VM-Series on AWS
6 -
VM-Series on GCP
2 -
VPC Flow logs
1 -
VPN
2 -
VPNs
4 -
Webinar
1 -
WildFire
2 -
wmi
1 -
XDR
1 -
xml
2 -
XML API
2
- Previous
- Next