- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Using XFF Headers with VM-Series on GCP
- LIVEcommunity
- Articles
- General Articles
- Using XFF Headers with VM-Series on GCP
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Printer Friendly Page
Organizations often use Google Cloud’s Application Load Balancer to distribute HTTP/HTTPS traffic to VM-Series firewalls deployed within Google Cloud.
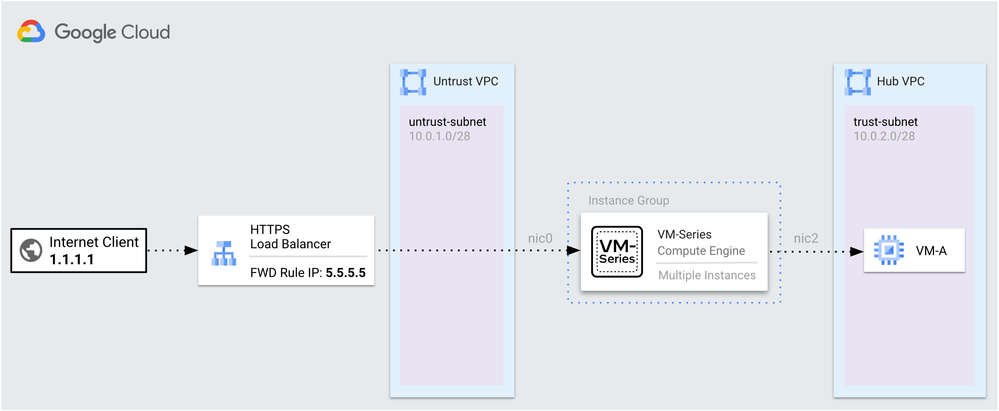
In this setup, the Application Load Balancer functions as a proxy, altering the client's source address before forwarding the request to the VM-Series for security inspection. This may present challenges for organizations defining security policies based on the client's address or requiring IP preservation for backend applications protected by the VM-Series.
Using XFF Headers with PAN-OS
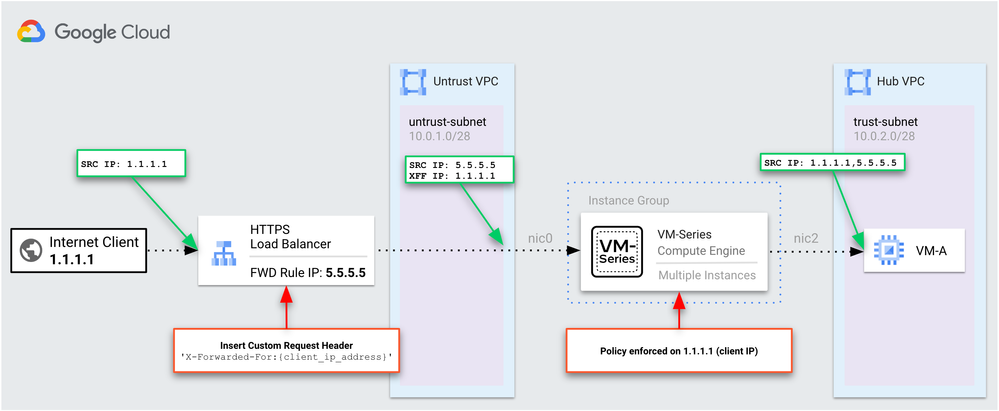
Within PAN-OS, the firewalls can be configured to use the source address of an X-Forwarded-For (XFF) header to enforce security policy. When configured, the firewall applies policy based on the address that was most-recently added to the XFF field.
However, when using the Application Load Balancer, this approach alone will not work. This is because the load balancer appends two addresses to the XFF header, where the <load-balancer-ip> is the most-recent address within the header and the <client-ip> is the next-to-last address.
X-Forwarded-For: <client-ip>, <load-balancer-ip>
Solution
Within the backend service configuration of the Application Load Balancer, you can define custom headers to make the client address the most-recently added address to the XFF field. When used, the load balancer preserves the supplied value of the custom header before the <client-ip>, <load-balancer-ip> addresses.
X-Forwarded-For: <supplied-value>, <client-ip>, <load-balancer-ip>
To insert the client’s address as the supplied value, you can use the client_ip_address header variable. This variable contains the client’s IP address, and has the same value as the <client-ip> address. Once configured, the VM-Series can then use the client’s address to enforce policy.
Steps to Implement
The steps below outline how to add the client_ip_address value as a custom header to an existing Application Load Balancer that uses the VM-Series as its backend service.
Adding Custom Request Header to Backend Service
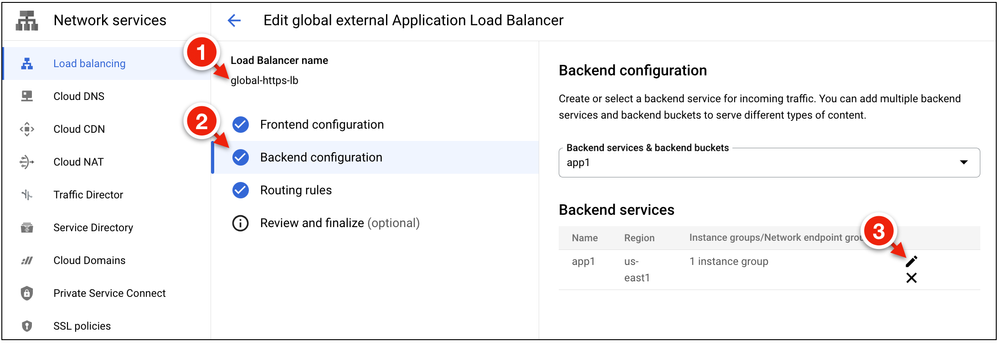
1. In Google Cloud, go to Network Services → Load Balancing. Select your Application Load Balancer and click Edit.
2. Select Backend Configuration and click the edit icon next to the backend service.
3. Under Advance Configurations → Custom Request Headers, click Add Header.
4. Set the header name to X-Forwarded-For and the header value to {client_ip_address}.
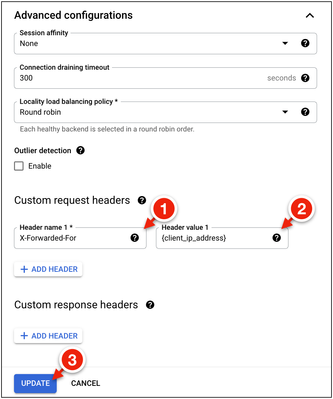
5. Click Update to apply the changes.
Configure VM-Series for XFF Headers
1. On the VM-Series, go to Device → Setup → Content-ID → X-Forwarded-For Headers.
2. Set Use X-Forwarded-For Header to Enabled for Security Policy.
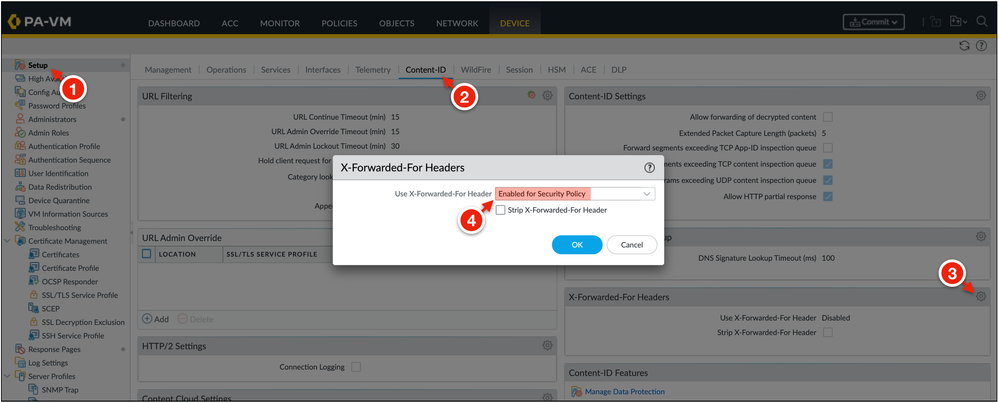
3. Commit the changes.
View Traffic Logs
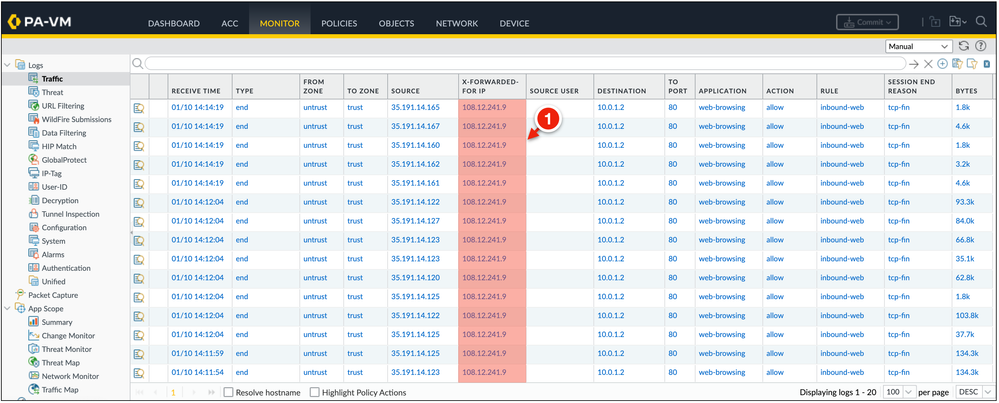
Once the changes have been applied, you can view the value of the client_ip_address header within the firewall's traffic logs.
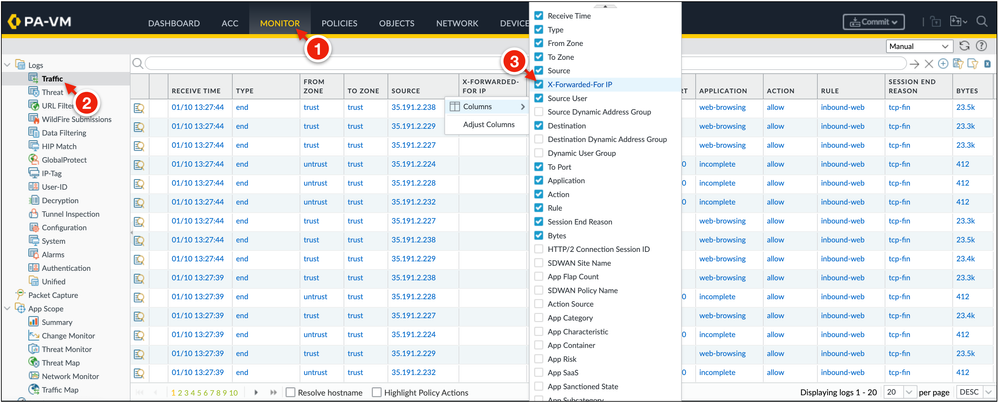
1. Simulate traffic flows through the Application Load Balancer to your application.
2. Go to Monitor → Traffic and add the X-Forwarded-For IP field to the log view.
The traffic logs should now contain the client's IP address under the X-Forwarded-For IP column. This address can then be used as the source address within the VM-Series security policies.
Hi mmclimans,
We have applied the setting which you have mentioned in the article, still we are unable to see the X-Forwarded-For IP entry in traffic logs.
In our environment we have applied SSL certificate on External & Internal Application Load Balancers or in PA we are performing Inbound SSL Inspection.
How we can resolve the issue ?
- 3083 Views
- 1 comments
- 2 Likes
- Identify and Deploy Specific PAN-OS Versions of VM-Series on Google Cloud in General Articles
- Get Started with VM-Series with AWS Gateway Load Balancer - A PoC Playbook Guide in General Articles
- Prisma Access SASE Extra Security Tips and Features in General Articles
- How Do I Know if Traffic Is Hitting a Decryption Policy? in General Articles
-
"Address Objects"
1 -
10.0
2 -
10.1
2 -
10.2
3 -
8.1
1 -
9.0
1 -
9.1
1 -
ACC
1 -
Active-Passive
1 -
AD
1 -
address objects
1 -
admin roles
1 -
Administration
6 -
Administrator Profile
1 -
Advanced URL Filtering
2 -
Advanced WildFire
1 -
Alibaba
2 -
Alibaba Cloud
3 -
Ansible
1 -
antivirus
1 -
API
2 -
applications
2 -
APS
1 -
Asset Management
1 -
Authentication
6 -
Authentication Profile
1 -
Authentication Sequence
1 -
automatically acquire commit lock
1 -
Automation
3 -
AWS
6 -
Azure
1 -
Basic Configuration
4 -
Beacon
2 -
Beacon2020
1 -
Best Practices
2 -
Block List
1 -
categories
1 -
certificates
1 -
Certification
1 -
Certifications
1 -
Certifications & Exams
1 -
CLI
4 -
CLI command
3 -
Cloud Automation
1 -
Cloud Identity Engine
1 -
Cloud NGFW
1 -
cloud security
1 -
Collector Group
1 -
Commit Process
1 -
community news
1 -
Configuration
9 -
Configure Next Generation Firewall
1 -
console
1 -
Cortex
1 -
Cortex Data Lake
2 -
Cortex XDR
5 -
COVID-19
1 -
CPSP
1 -
cyber elite
1 -
Cyberelite
11 -
dag
2 -
Debug
1 -
debugging
2 -
Default Policy
1 -
Deployment
1 -
discussions
1 -
EDL
3 -
education
2 -
Education and Training
2 -
Education Services
2 -
Educational Services
1 -
Effective Routing
1 -
Endpoint
1 -
ESXi
1 -
Events
1 -
expedition
1 -
export
1 -
failover
1 -
FAQ
1 -
Filtering
2 -
Firewall
2 -
Firewall VM-Series
2 -
Focused Services
2 -
Focused Services Proactive Insights
1 -
gateway
1 -
Gateway Load Balancer
3 -
Gateway Loadbalancer
2 -
GCP
5 -
GCP Firewall
1 -
geolocation
1 -
Getting Started
1 -
GitHub
1 -
Global Protect
1 -
Global Protect Cookies
1 -
GlobalProtect
8 -
GlobalProtect App
1 -
globalprotect gateway
1 -
GlobalProtect Portal
2 -
google
2 -
Google Cloud
3 -
google cloud platform
4 -
GWLB
3 -
Hardware
2 -
hash
1 -
Header Insertion
1 -
High Availability
1 -
How to
1 -
HTTP
1 -
https
1 -
Hybrid Cloud
1 -
ike
3 -
import
1 -
Installation & Upgrade
1 -
IoT
2 -
IoT Security
1 -
IPSec
4 -
IPSec VPN Administration
1 -
kerberos
1 -
Kubernetes
1 -
Layer 2
2 -
Layer 3
1 -
Learning
1 -
licenses
1 -
local user
3 -
Log Cluster Design
1 -
Log Collection
1 -
Log Collector Design
1 -
Log Forwarding
1 -
Log4Shell
1 -
Logging
2 -
login
1 -
Logs
3 -
Malware
1 -
Management
8 -
Management & Administration
5 -
MFA
1 -
microsoft
2 -
Microsoft 365
1 -
minemeld
24 -
multi factor authentication
1 -
multi-factor authentication
1 -
multi-vsys
1 -
NetSec
1 -
NetSec Newsletter
1 -
Network Security
37 -
network-security
1 -
Networking
1 -
New Apps
1 -
News
1 -
newsletter
2 -
Next Generation Firewall
4 -
Next-Generation Firewall
42 -
next-generation firewall. network security
1 -
Next-Generation Firewall. NGFW
4 -
ngfw
27 -
NGFW Configuration
10 -
NGFW Newsletter
1 -
Objects
2 -
Oracle Cloud
1 -
Oracle Cloud Infrastructure
1 -
OTP
1 -
PA-3200 Series
1 -
PA-400
1 -
pa-440
2 -
PA-5400 series
1 -
PA-800 Series
1 -
pa-820 firewall
1 -
Packet Buffer
1 -
packet debug
1 -
packet diag
1 -
PAN-OS
17 -
PAN-OS 10.2
1 -
PAN-OS 11.0
1 -
PAN-OS 9.1
1 -
Panorama
8 -
Panorama 8.1
1 -
Panorama 9.1
1 -
Panorama Configuration
2 -
Panorama HA
1 -
PBF
1 -
PCNSA
2 -
PCNSE
2 -
policies
2 -
policy
3 -
Policy Based Forwarding
1 -
Prisma
1 -
prisma access
5 -
Prisma SD-WAN
1 -
proactive insights
2 -
QRadar
1 -
Radius
1 -
Ransomware
1 -
region
1 -
Registration
1 -
Release Notes
1 -
reporting and logging
1 -
Risk Management
1 -
Routing
1 -
SAML
1 -
SASE
2 -
script
2 -
SD WAN
1 -
SD-WAN
1 -
SDWAN
1 -
Search
1 -
Security Advisory
1 -
Security automation
1 -
security policy
4 -
security profile
1 -
Security Profiles
2 -
Session Packet
1 -
Setup & Administration
7 -
Site-to-Site VPN
1 -
Split Tunneling
1 -
SSL
1 -
SSL Decryption
2 -
SSL Forward Proxy
1 -
SSO
1 -
Strata Logging Service
2 -
Support Guidance
1 -
syslog
1 -
Tag
2 -
Tags
2 -
Terraform
2 -
TGW
3 -
threat log
1 -
Threat Prevention
2 -
Threat Prevention License
1 -
Threat Prevention Services
1 -
Tips & Tricks
2 -
tls
1 -
traffic_log
1 -
Transit Gateway
1 -
Traps
1 -
Troubleshoot
2 -
Troubleshoot. logs
1 -
troubleshooting
5 -
tunnel
2 -
Tutorial
2 -
Ubuntu 16.04
1 -
Unified Monitoring
1 -
Upgrade
2 -
upgrade-downgrade
3 -
url categories
1 -
URL Filtering
2 -
URL-Filtering
1 -
User ID Probing
1 -
User-ID
1 -
User-ID & Authentication
1 -
User-ID mapping
1 -
userid
1 -
VM Series
1 -
VM-Series
15 -
VM-Series on AWS
6 -
VM-Series on GCP
2 -
VPC Flow logs
1 -
VPN
2 -
VPNs
4 -
Vulnerability Protection
1 -
Webinar
1 -
WildFire
3 -
Wildfire License
1 -
wmi
1 -
XDR
1 -
xml
2 -
XML API
2
- Previous
- Next




