- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Enhanced Security Measures in Place: To ensure a safer experience, we’ve implemented additional, temporary security measures for all users.
Unlock your full community experience!
Huge data transfers between remote DC and PAN Agent
- LIVEcommunity
- Discussions
- General Topics
- Huge data transfers between remote DC and PAN Agent
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Huge data transfers between remote DC and PAN Agent
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-01-2011 11:18 PM
Hi Team,
We have had issue with huge data transfers between PAN agent and remote DC's
We have observed lot of data activity between the PAN Agent and other Domain Controller servers on the WAN.
For instance, in the last one hour our Router accounting, and WAN Graphs, has shown 830 Mb of file access from one of our
remote DC, which is connected via WAN MPLS to PAN agent at our HO.
Another of remote DC's over the WAN, for last 24 hours, shows 19 GB of data transfer !!
Could this mean some fine tuning has to be done on PAN agent or is this supposed to be normal.
What exactly is this huge ammount of data transfer, and why so many GB !!
Kindly advise at the earliest.
Rgds,
Tauseef
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-02-2011 08:10 AM
Generally speaking you will want to have a Pan Agent at the site with your remote domain controller(s) to cut down on the amount of traffic over your WAN links.
The default timer for reading the security log is one second. In your example timer configuration you have set this interval to 600 seconds (10 minutes). This means that there will be up to a ten minute delay between a user logon and the firewall receiving an update that includes the user-to-ip-mapping for this logon event. This will obviously have some impact on your end-users as they may have to wait up to 10 minutes before they match the correct security policy based upon their user ID and group membership.
-Benjamin
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-02-2011 03:23 PM
ta185020 wrote:
Hi Team,
We have had issue with huge data transfers between PAN agent and remote DC's
We have observed lot of data activity between the PAN Agent and other Domain Controller servers on the WAN.
For instance, in the last one hour our Router accounting, and WAN Graphs, has shown 830 Mb of file access from one of our
remote DC, which is connected via WAN MPLS to PAN agent at our HO.
Another of remote DC's over the WAN, for last 24 hours, shows 19 GB of data transfer !!
Could this mean some fine tuning has to be done on PAN agent or is this supposed to be normal.What exactly is this huge ammount of data transfer, and why so many GB !!
Kindly advise at the earliest.
Rgds,
Tauseef
Tauseef.
If you think about it, the PAN Agent reads *every* event in the security log - which means that if you're accessing a remote DC with your agent, you're going to get a lot of traffic in a busy network.
I believe best practise for this situation is to run at least one agent per SITE - so have one of the DC's at your remote site running an agent and reporting back to the PA firewall, rather than having an agent in your central site connecting to the DC at the remote site.
Careful configuration of the agent at the remote site (I.E. only have the agent for the site monitoring the DC's located in that site) would minimise traffic.
You can configure your firewall to listen for multiple agents - up to 5 per firewall, I believe - so having more than one running shouldn't be a real issue, unless you're worried about resources on your remote DC.
Cheers.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-02-2011 04:12 PM
We are seeing this as well -- in fact, over a three-week period we saw UIA-to-DC traffic volumes in the order of terabytes (!!!) on our network. Seems the busier the site, the bigger the traffic. So the approach we are taking is to put the agents as close to (or possibly even on) the DCs as possible.
In contrast, over the same three-week period the traffic between the agent and the firewall itself is only 130 MB. It's a good trade-off for having to run several agents. Each firewall should handle up to 100 UIAs and each UIA can handle 10 DCs, or a max 1,000 domain controllers per firewall.
Hope this helps.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-25-2011 07:04 PM
The User ID Agent software is quite chatty. In our environment the User ID Agent server has a consistent throughput of 2Mbps. To be fair, this server is also used for the Websense DC Agent server, but I'm pretty confident that the bulk of the traffic is from the PA side of things.
In our environment we have 6 different user ID agent servers and they are all collocated with the domain controllers. Someone mentioned that the firewalls can only talk to five user agent servers. We have six and the firewalls here see them just fine. So, I can at least say that at least six will work.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-26-2011 11:09 AM
The issue I'm seeing with having multiple PAN-Agent is only one PAN-agent is primary all the others are just backup. Also pan-Agent from what I've seen only look at the first 2 DC listed on the list.
Please correct me if I have wrong impression.
thanks.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-26-2011 11:18 AM
Our 6 Pan Agents are used for six different domains. Each one is only configured to point to the two domain controllers at that location. The PA collect user data from all of the User Agents so in our environment every one of them is a primary.
I should clarify our setup. We only have one Pan Agent server for each domain. It sounds like you have a several backup PAN agent servers for a single domain.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-22-2013 01:04 PM
Here's method to reduce WAN usage between the UserID agent and remote DC's. You can instruct the DC's to forward the logon events to a log collector & have the agent read the login events from the centralized log collector. The DC's will transmit only logon events to the log collector & this will minimize WAN usage.
Information on how to set up a log collector - http://technet.microsoft.com/en-us/library/cc722010.aspx.
The DC's are configured as the log source and info can be found here - http://technet.microsoft.com/en-us/library/cc748890.aspx.
On the log collector, we need to change the Log Path of the Forwarded Events to point to file ...\Logs\Security.evtx and our UserID agent will read the events located there.
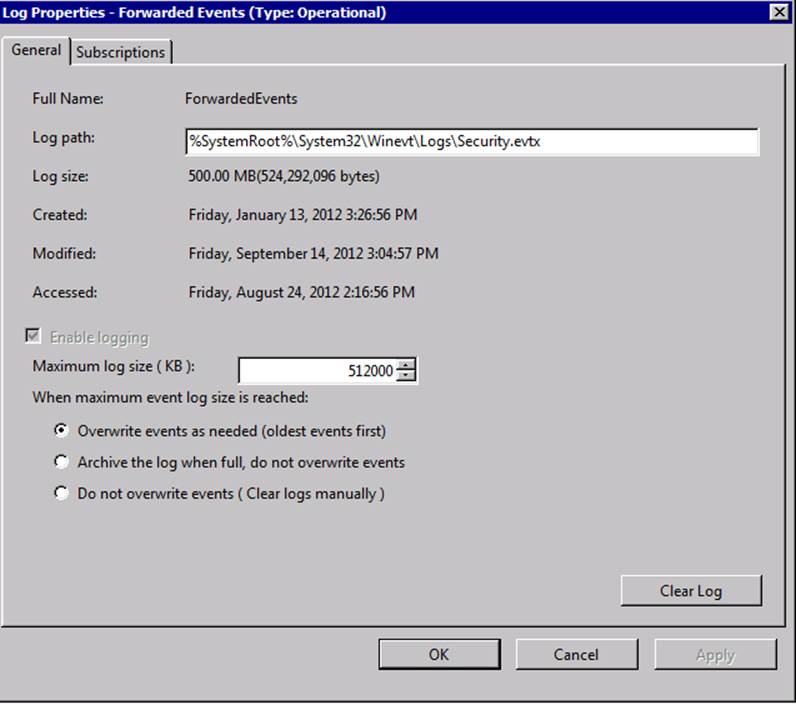
We also instruct the log collector to subscribe to these logon events.
2000 & 2003
AUTH_TICKET_GRANTED = 672,
SERVICE_TICKET_GRANTED = 673,
TICKET_GRANTED_RENEW = 674,
2008
LOGON_SUCCESS_W2008 = 4624,
AUTH_TICKET_GRANTED_W2008 = 4768,
SERVICE_TICKET_GRANTED_W2008 = 4769,
TICKET_GRANTED_RENEW_W2008 = 4770,
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-23-2013 01:18 PM
Great tip for those situations where one dont want to install the pan-agent straight on each DC (and lock it to only read the log from localhost).
- 6990 Views
- 9 replies
- 1 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Observing Internal error logs on Global Protect SAML Auth in Next-Generation Firewall Discussions
- New Surface Pro. Global Protect Ver. 6.2.3-270. Not working. in GlobalProtect Discussions
- ION CLoudGenix Devices Offline in General Topics
- Help Allowing VDI Connections in General Topics
- rustdesk for remote support in General Topics



