- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
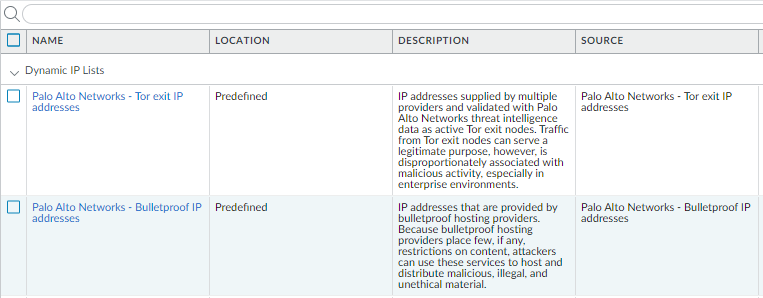
PaloAlto Predefined IP Lists not appearing
- LIVEcommunity
- Discussions
- General Topics
- PaloAlto Predefined IP Lists not appearing
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-08-2024 04:11 PM
After rechecking licenses, rebooting, checking multiple things, I am unable to get the EDL Predefined IP List dropdown to populate with PA lists (Bulletproof IPs, High risk IPs,. etc.). The Predefined URL List populates with the Authentication Portal Exclusion list, but the list has no entries.
- Threat Prevention license is installed and active
- Application and Threats dynamic updates are downloading and installing normally
- "request system external-list show type predefined-ip name <>" does not complete for any name
- "request system external-list show type predefined-url name <>" completes for panw-auth-portal-exclude-list but the list is not populated
Is this a wider effect of the KB/Support being down (unable to query license status correctly)? There seem to be a couple KB articles but nothing will load for me.
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-09-2024 02:20 PM
Hello @Adrian_Jensen
could you confirm that Antivirus package is installed? Build-in EDL objects will appear on the Firewall only when Dynamic Updates like "Applications and Threats" and "Antivirus" are installed on the firewall.
Kind Regards
Pavel
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-09-2024 02:20 PM
Hello @Adrian_Jensen
could you confirm that Antivirus package is installed? Build-in EDL objects will appear on the Firewall only when Dynamic Updates like "Applications and Threats" and "Antivirus" are installed on the firewall.
Kind Regards
Pavel
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-09-2024 04:07 PM
I am getting "Applications and Threats" updates, but I am not getting "Antivirus" updates (on either the active or passive unit in this HA pair). The default Antivirus Security Profile is present. Both the "Threat Prevention" and "Advanced Threat Prevention" licenses are installed and active. The docs just say that the Threat Prevention license is required:
With an active Threat Prevention license, Palo Alto Networks provides built-in IP address EDLs that you can use to protect against malicious hosts.
I can now get to the KB articles which does say in fact say that the AntiVirus dynamic update package is required. I would have guessed it was in the "Applications and Threats" package:
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000PM0pCAG
Resolution
- Install Antivirus from GUI: Device > Dynamic Updates, before the predefined External Dynamic Lists populate under GUI: Objects > External Dynamic Lists.
- A valid Threat Prevention license is required to be loaded on the Palo Alto Networks Firewall for installing Antivirus.
- Applications and Threats needs to be installed on the Firewall before installing Antivirus.
I just did yet another "Check Now" from the Dynamic Updates page and suddenly the Antivirus packages are showing up and I was able to add the predefined IP lists and the URL list is now populated. I've had this firewall up, licensed, software updated, rebooted for a few weeks (just prepping to insert into live traffic) and never been able to get the AV packages (the entire category never appeared). This firewall has been a problem child since receiving, bought it new from PA with several others and out of the box it was registered to a different company with an expired full trial license package assigned.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-11-2024 11:12 AM
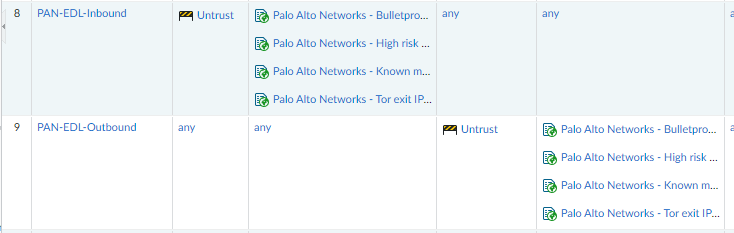
Any idea on how to fix up the predefined EDL list names? All my other PaloAltos show the full EDL name as an object. The problem PA is showing the internal/short name as the object in policy rules and I can't seem to change it:
Normal PAs:
Problem PA:
Both are running 10.2.7-h3 with current AV and Apps&Threats updates.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-12-2024 05:13 PM
Hello @Adrian_Jensen
thanks for reply and sorry for late response.
Unfortunately, I was not able to find a Firewall with this issue in my environment to reproduce it.
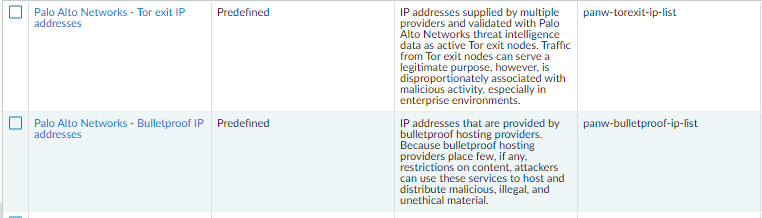
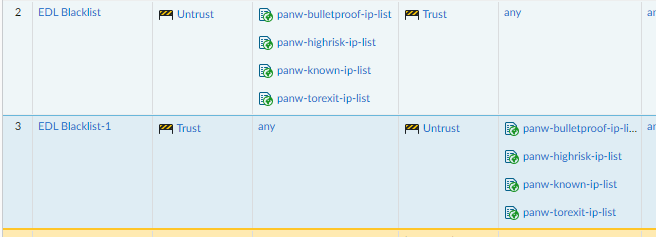
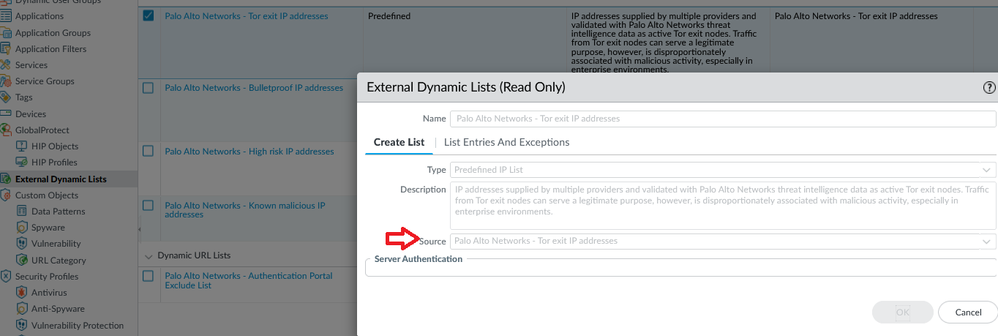
From the screen shot with problematic PA you shared, the EDL name: "panw-torexit-ip-list" is displayed in source, so this makes me think the issue is related to EDL itself rather than how it is displayed in policy. Likely if source is displayed as "Palo Alto Networks - Tor exit IP addresses" instead of "panw-torexit-ip-list" this would resolve it how it is displayed in policy as well.
What I noticed is when I open "Palo Alto Networks - Tor exit IP addresses" from: Objects > External Dynamic List, for approximately one second source is displayed as "panw-torexit-ip-list" before it changes to "Palo Alto Networks - Tor exit IP addresses" (I observed the same for all other built-in EDLs):
This makes me think that in case of your problematic PA something is preventing the refresh/update. Could you check Firewall's DNS configuration? Can you see anything in ms.log? Could you try to restart management process?
Kind Regards
Pavel
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-13-2024 10:39 AM - edited 03-13-2024 11:45 AM
Yes, panw-torexit-ip-list is the internal configuration name, "Palo Alto Networks - Tor exit IP addresses" is the display name. Sometime between yesterday afternoon and today it seems like the PA suddenly started working and resolving the EDL names correctly (in the EDL configuration and Security Policies). I was running panup-all-antivirus-4753-5271 (3/10 release) at the original problem time. The PA has since downloaded/upgraded the -5272, -5273, and -5274 releases without issue (-5273 last night and -5274 this morning have been installed since I last looked).
I have DNS servers setup and it seems to be resolving updates.paloaltonetworks.com/etc. just fine. URL-Cloud is connected and updated. I have multiple FQDN Address Objects setup and the resolve button shows all getting an address, but when I do a "show dns-proxy fqdn all" on the CLI nothing appears except the built-in sinkhole.paloaltonetworks.com object (which doesn't exist anywhere in my config).
- 1 accepted solution
- 779 Views
- 5 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!