- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Enhanced Security Measures in Place: To ensure a safer experience, we’ve implemented additional, temporary security measures for all users.
Unlock your full community experience!
Port Forwarding Problem
- LIVEcommunity
- Discussions
- General Topics
- Port Forwarding Problem
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Port Forwarding Problem
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-31-2017 09:32 AM
This should be fairly simple but am at wits end.
I need to forward 2 ports from an external IP to an internal private ip (Ports 8088 and 22). I found this article and am following its example: https://nubisnovem.com/pinning-a-hole-in-palo-alto/
Public/Outside IP of PA-220 : 44.44.44.44
Internal IP: 192.168.0.222
IP I am trying to browse/connect from: 123.123.2.2
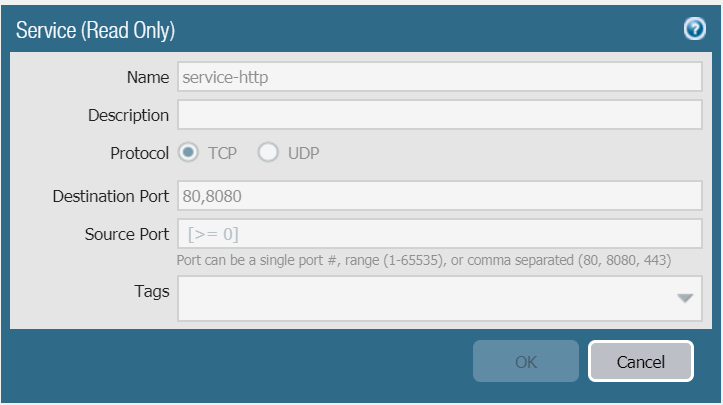
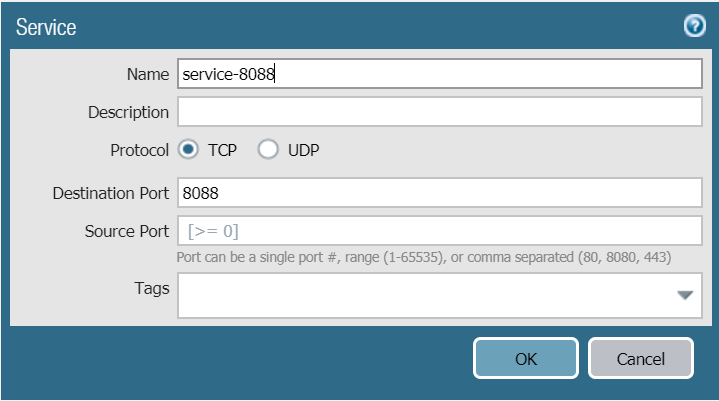
I created two Services
Name: 8088
Protocol: TCP
Destination Port: 8088
Source Port: 1-65535
Name: SSH
Protocol: TCP
Desitnation Port: 22
Source Port: 1-65535
I created two NAT statements
Name: 8088
Source Zone: Outside
Destination Zone: Outside
Destination Interface: Any
Source Address: Any
Destination Address: 44.44.44.44
Service: 8088
Source Translation: None
Destination Translation: 192.168.0.222
Name: 22
Source Zone: Outside
Destination Zone: Outside
Destination Interface: Any
Source Address: Any
Destination Address: 44.44.44.44
Service: 22
Source Translation: None
Destination Translation: 192.168.0.222
I also created 1 security policy
Name: PortForward
Source Zone: Outside
Source Address: Any
Destination Zone: Inside
Destination Address: 192.168.0.222
Application: Any
Service: 8088 and 22
Action: Allow
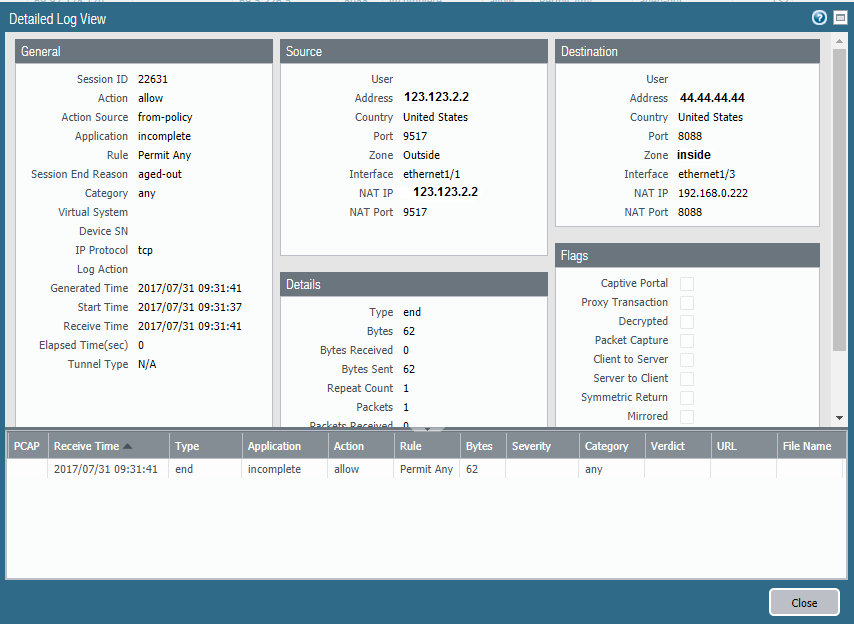
When I browse through a webpage to 44.44.44.44:8088 a web browser. PA Monitor shows incomplete under application
Log Detail:
Like I said I am basing everything on the article above so there may be a better way to do it.
Any advice is appreciated.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-31-2017 09:39 AM
Most likely, 192.168.0.222 doesn't have a route back to 123.123.2.2, or else it's using a different egress point.
A couple things you can do:
1. Make sure that 192.168.0.222 has a route to 123.123.2.2 and that it goes through the Palo Alto Networks firewall.
2. Use source NAT in addition, specifying the internal IP of the firewall.
Your traffic log detail shows it just barely, 0 bytes and packets received with 62 bytes sent, probably the TCP SYN packet.
Best regards,
Greg Wesson
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-31-2017 09:59 AM
Greg,
Appreciate your response.
1. I have an additional NAT from my internal zone to external its basically my NAT for internet access from my inside zone.
Name: Inside - Internet Access
Source Zone: Inside
Destination Zone: Outside
Source Address: 192.168.0.0/24
Source Translation: dynamic ip and port - 44.44.44.44
That should suffice from getting back to 123.123.2.2 shouldn't it?
2. Do I need the source NAT if I already have the above NAT?
Again, thank you.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-31-2017 10:20 AM
There is only one NAT rule that is applied for each session, so the separate Source NAT rule you provided won't get applied when the other one is.
Assuming L3 setup:
Run a traceroute from the internal server to the external client IP. Make sure that the MAC address of the firewall your server hits is the same one that is sourcing the traffic inbound from that external client. If not, you've got a routing issue.
If you're familiar with packet captures, you can take one on the firewall (grab transmit and receive stages) at the same time as one running on the internal server. You should be able to confirm if the SYN is making it to the server, if the server is responding with the expected SYN+ACK, and if that's making it back to the firewall.
-Greg
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-31-2017 01:21 PM
The following might help you a little bit more than what you found in the above article. I would look at live prior to following a random article; usually you'll find we include more information and pictures 😉
The entire article this was pulled from can be found HERE
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-31-2017 10:32 PM - edited 07-31-2017 10:56 PM
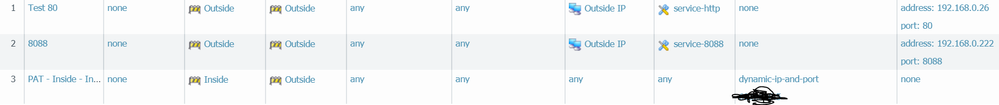
Ok. So I am still not having any luck. For troubleshooting purposes. I installed IIS on an inside PC on the same network and set up an additional NAT for http-web browsing that works fine but still can not get port 8088 to work at all. Below Rule 1 works fine Rule 2 does not.
At this point for testing purposes I just have a permit any security policy
What is interesting is in the monitor log the application shows as application web-browsing for when I go to port 80 and it works but it still shows as incomplete when trying 8088
So to sum up. I have a wide open security policy, 2 identical NAT statements in which the service set up is exactly the same, one for port 80 and one for port 8088. Port 80 works fine going to 192.168.0.45 but port 8088 going to 192.168.0.222 does not. If I get on an internal PC and browse to 192.168.0.222:8088 it works just fine so I am pretty certain there isn't an internal PC firewall blocking anything.
browsing to publiciip:80 works like it should but publicip:8088 does not.
Not sure how else to troubleshoot.
Thanks again for any suggestions.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-01-2017 08:31 AM
If you PCAP the traffic what exactly do you see. Your NAT appears to be working otherwise you wouldn't get the log, so you either don't have a return path properly setup for the traffic or the 192.168.0.222 is not setup properly so you never get a response.
- 5847 Views
- 6 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Not able to access panorama(m-200) through console port . in Panorama Discussions
- Boot PXE Fog in General Topics
- postfix server nat rule on panos -9.-0.4 in Next-Generation Firewall Discussions
- Global Protect connections fails after 20-30 seconds in General Topics
- XSOAR Engine Integration issue in Cortex XSOAR Discussions