- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Solution for "SSL decryption bypass for Anydesk"
- LIVEcommunity
- Discussions
- General Topics
- Re: Solution for "SSL decryption bypass for Anydesk"
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Solution for "SSL decryption bypass for Anydesk"
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-11-2021 05:43 AM - edited 03-22-2021 01:45 AM
Hello,
I am being asked a lot about why is Anydesk getting a "decrypt-error" end reason when SSL Decryption is active.
Here is a simple explanation and how to overcome this.
What you usually going to do with this kind of errors is creating a Decryption bypass rule for Anydesk (in this example)
Since is it impossible to bypass based on application, you would probably use a Custom URL category with a wildcard (*.anydesk.com), and apply it in a bypass rule. Unfortunately, this doesn't work (I'm not sure why, I think Anydesk uses IP addresses and not URLs)
The other option I came across is using an FQND (relays.net.anydesk.com) published in one of the related articles, that also didn't work for me. It was not consistent.
Then I found that Anydesk is being bypassed by default in PANOS (Device --> Certificate management --> SSL Decryption Exclusion).
Then why isn't it being bypassed?!
Well, it is because of the certificate Anydesk uses. It is using a Self-Signed certificate, and your device does not trust it (yet).
This is the reason for the decrypt-error.
Basically, what you would like to do now is:
Start a packet capture and export the CA certificate.
Then, import the certificate to your device, and mark it as a trusted CA.
Commit, and now Anydesk should work.
I am sharing here the CA certificate currently being used by Anydesk.
Copy the text below to a text file and rename it to ".crt"
-----BEGIN CERTIFICATE-----
MIIFYzCCA0ugAwIBAgIJAIf7DQy3sYvoMA0GCSqGSIb3DQEBBQUAMEgxFzAVBgNV
BAMMDkFueU5ldCBSb290IENBMSAwHgYDVQQKDBdwaGlsYW5kcm8gU29mdHdhcmUg
R21iSDELMAkGA1UEBhMCREUwHhcNMTQwNDExMDIzNzU1WhcNMjQwNDA4MDIzNzU1
WjBIMRcwFQYDVQQDDA5BbnlOZXQgUm9vdCBDQTEgMB4GA1UECgwXcGhpbGFuZHJv
IFNvZnR3YXJlIEdtYkgxCzAJBgNVBAYTAkRFMIICIjANBgkqhkiG9w0BAQEFAAOC
Ag8AMIICCgKCAgEAtBVBDdoa01og/vnfvwqM8aSt79RUlufigrcNAOrxN+LXjKEW
O6BoCDiqbdsmvqZpkzaojh5w3KyBHuLdFoM0tRVw9YrNne5dgHxaeKIHpK7m+NYx
+lx7u+Ba61Evl7/2+zMnkLPY5ODNaDtqh2ymDefYvWHfVmsq4Rwr9Z+/hd2MWwYe
cX+6SqZAsHcX6iw/W5QUhS6tEWGriPYBu7NHa+KBGPGOOebYewxjhoOscIR1Jy01
PXt7qM6ySHkIOC2CJn6TSzJ2ZoWn/crxCi/HYg9qQP4aa1gcU+RjwXWDmqt4BEmD
H+cjcJ+jv2jRMy9M3l6GmH1hfQE09Zzpy0FrrlArZ9XZ8gL8X6NSNLncZ+/6c8WU
QOq1iveY7Oibu4ZsbzY3ioCMn4T2ykp2InKNUn2FdU1V762v8+UWIwBb6Lbtfp8u
gEvu1V/cZemJ3NumQwS7zv2pTC8ZM6rmcSCG/kWLl+bIHU9wusfAw/Om8trCpBvd
iU7sHNp7JI+qQvkUMoNoY8gmvOwTsw0L4rYIxsYGfqMWbxXSGxZSPB8ikSUXFcxC
gto7qDnHKlDK2UygjJUzdQNwuN+gybKyixs4g3kywxLaM5ZC9JERqsYmMbzqQ4ow
VGXFQ55QO/qRkw6dOyNKPUPBxiKbaK8v/AGAUhgFIg69auQuydbsxY/zE7MCAwEA
AaNQME4wHQYDVR0OBBYEFBlleQaAxt6yqliZV7I2XO0BYo1HMB8GA1UdIwQYMBaA
FBlleQaAxt6yqliZV7I2XO0BYo1HMAwGA1UdEwQFMAMBAf8wDQYJKoZIhvcNAQEF
BQADggIBALOqRxekr9JgNBWtJdWOKF7BqrGNMFabR3by4CBUBj3xI8Lvu6Hyn+Or
DAa/VF4MGjVWbeGTS8WZX5CGflKDlKCgRzby/PLCTXDJyW40XKcPBP3rFl6KvoY7
oAxzf6P1Xz0rxUEMZwrjSCvKYvapmh7J5ES8F/nbXEWYCWnsyGPvhSlOce35maxJ
IIqQvFmO8fOlmZkS46d75Wg0q1NarfFEyrp/wqZzkhDqjLHGydXkXisPHkqT+W1M
BoWQZVHTicwuomu15PDqNzWpfcDLhxIycpMhUYEdowzKlviB9JKgr/cZJPPmzeoR
KcnxKR2yKxgatKPAWMRwOXiniNd0MsKAYoNY47Q+JbhWLGB3UiWqYTLRl413JDQk
xdvy3WHI7WNXDsJw5R9S3WxvOLLa7Z2nL4f6s3DlZE35wwLVRtofy/BYIPxElvDK
tps55s8n0CyZdNTK3keI7d/3nDusimLSdZDZAIHT+MJHjpq9h23O5Zp/KHakd8Y/
ub9N8cvfDyxz/rRg4yZeg/KuNlaU6aedoT3KXW49Xahv8qWP855ohSfs6WeFNBYN
RTQUjgcMeyVRVPM/oSrvmheeUd4WZPvd4ciUCYw5u3dz1Ga7SStc+itXi2at96hw
O4+eCXHeEi7tAhBM1Wcecv86PjRtkmA9RF70IWDubC46cxrDJmr0
-----END CERTIFICATE-----
Hope this is helpful.
Cheers!
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-09-2024 10:58 AM
Hi Guys,
It works without certificate. Solution by @CosminM with a twist:
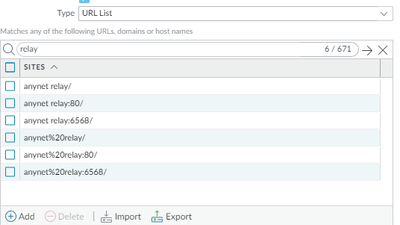
So, create URL list with those:
- anynet%20relay/
- anynet%20relay:80/
- anynet%20relay:6568/
- anynet relay:6568/
- anynet relay:80/
- anynet relay/
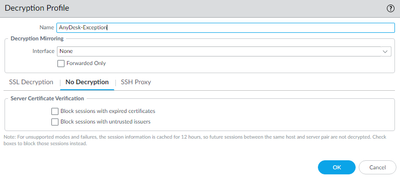
Decryption profile like that:
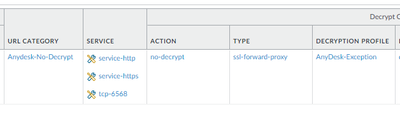
And Decryption rule like that:
And this is how it looks in logs:
I hope this helps 🙂
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-09-2024 08:47 PM
Hi @S.Support212931 ,
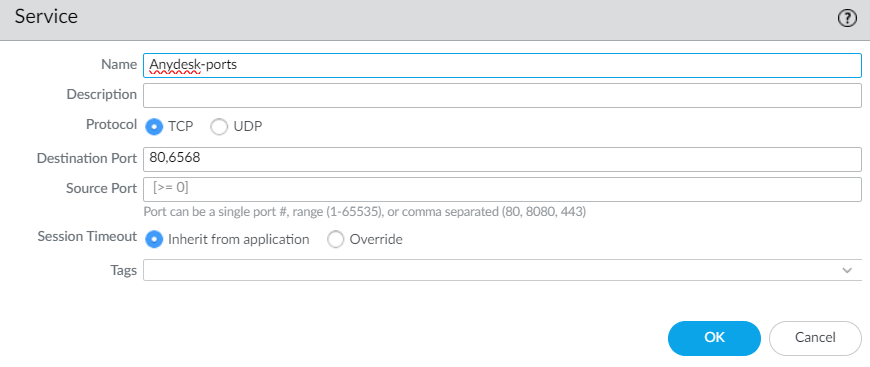
One of the steps it's to create a service for TCP destination port 6568. The source port it's dynamic and in your service should be empty.
Cosmin
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-09-2024 11:20 PM
I see 2 issues with this
1. This solution doesn't just allow anydesk to bypass the decryption - it basically allows everything to bypass the decryption for destination port 80 and 6568. How to you make sure only anydesk is allowed in this case ?
2. Even if we find a way to make it only for anydesk - it then bypass the decryption which is not something we want.
What is someone transfers a malicious file through anydesk during the session - How will the firewall be able to see it if decryption is off.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-09-2024 11:46 PM
This is reply what I've got from AnyDesk support:
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-10-2024 01:50 AM
Hi,
that URL list is there to make this work for Anydesk only and yes, it disables decryption totatly.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-10-2024 02:51 AM
Thank Tomaz - noted
Can you please share a screenshot from the URL list you made.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-10-2024 04:47 AM
Here it is:
That's all I can show without compromizing company setup 🙂
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-10-2024 05:18 AM
I was able to find the new private certificate from some captures (but unlike in the past the new certificate is encrypted thus it does not work any more
I guess bypass it is for now..!!!
But people can pass malicious files through anydesk-app now and firewall will not be able to detect them
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-10-2024 08:03 AM - edited 04-10-2024 08:33 AM
Even in the past, importing the Anydesk Root CA into the firewall did not mean that we were decrypting the traffic.
Then we just mark that issuer as reliable.
So, the risk of transferring malicious files is the same, that's why it's good to have security solutions on the end-points as well.
I just updated my older post (https://live.paloaltonetworks.com/t5/general-topics/anydesk-issue/td-p/198761/page/2) to match the new Apryl 2024 changes.
Cosmin
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-11-2024 03:59 AM
-----BEGIN CERTIFICATE-----
MIIFbDCCA1SgAwIBAgIJAOcOOMSgQkRlMA0GCSqGSIb3DQEBDQUAMEoxGTAXBgNV
BAMMEEFueU5ldCBSb290IENBIDIxIDAeBgNVBAoMF3BoaWxhbmRybyBTb2Z0d2Fy
ZSBHbWJIMQswCQYDVQQGEwJERTAgFw0xOTAyMjcyMDEyNDJaGA8yMTE5MDIwMzIw
MTI0MlowSjEZMBcGA1UEAwwQQW55TmV0IFJvb3QgQ0EgMjEgMB4GA1UECgwXcGhp
bGFuZHJvIFNvZnR3YXJlIEdtYkgxCzAJBgNVBAYTAkRFMIICIjANBgkqhkiG9w0B
AQEFAAOCAg8AMIICCgKCAgEAqUhRKwaqr1CtntCMZuAUNG5XbII8il8yXSScuhcU
3esJbXdiDWXqKd8HS4h3hTTiKsrPa7vx8SZXG+rlAigmfpgYe6CLK1DvW5AIjrUe
kOmyt9h6eMQ1aYl+YWVAaiFZuU6HHdVVkAvJLABRNs1Mg6PU05gMVrugEbRq/8nl
urQLjfPAszqu2hNE9Vhupf0agw2hbSJ6WzeQnaubOZPs1bQ3uD8bJKVMg/ttgJ9c
wkyqDLVP4zs3Wz8L1g2+EdwuQxJnN9rLdlunb+Hop86+ZaJXPWqJzqOZCa3EA9As
RxQVhL9h35fktdu5u0CL5ZBS9B2jumydmRWGTfwFxbMThd/tn/e9BzorTCKEcvJr
DoqxaCxE8iOGbjTN2zIC0PTIv6g0sj28nbPF5FBelpF5D5k+o1SZ9xjDG4xmcovU
u3W1nrKf60CLoHTqQ2XeUYu7NkKOr9Fn72hSqDACRBJQIGxZnresFSRY2IS6FTy4
8zyfnz0Qrlj/A5vzAOqKA7S3XNCT1DcjlA6V4a5AWe1bdsW/MB9fsFuPPmknLa8n
GOW2Y57eXgQ9SShz/Mn9+5nzOTSWpFbP7r5kZt6lDyMvrA2TN4PS2teuKy/ndna8
XV/ad8yD4Uf4slVPU0g9r2ZEb8PyxS3z1E1DbZ4nJBQTCI2dgBpeseP7rWGAGHKY
zMkCAwEAAaNTMFEwHQYDVR0OBBYEFFnC16nf4dqWO76ICbRqUvhBCPUbMB8GA1Ud
IwQYMBaAFFnC16nf4dqWO76ICbRqUvhBCPUbMA8GA1UdEwEB/wQFMAMBAf8wDQYJ
KoZIhvcNAQENBQADggIBADsJ7G/zeZhpGAzLbhzYo/bnvrpFV9F77JybAKpG+Oit
ByYvH8jLdQjoBNRPGv8Cd5U6kehaS2wXF3NbGLVF5MpHZL6QFQnEplfwpIz1jLxn
LFL2zzD/Yxtb5Noef5CIklb2JSejDMwz3AoVMru5OzQZn0O+eQHHY/PT/4hc7KWQ
e3IkJKjwf7drAVgKKzpaUsXD6mrzFdYPYThWUtrse+al37pyJWZYaYddqUMvBiLh
MrG/E9su5p/nRVSWv7W5h+03dciN+F70RcJD/yD22NSa02swMKLqWAbdrDbScYER
eraUizYRrtPCttch4pLAZUDUNmgftGR52lJ679945EoLLEDvOyKrLz+dPZ+dHZS9
qvfvyHGV/zCnDNI3oDZM3M/l8WINapU8oWlfWpTdC1w6aNPnxoS1QuIGFVVdzBbG
SV7ngG9YLqgIPw1EpxPyu4T7o8XLoD5z0U/u9wR32W3W5Bekzq7DmgL/uSTrP5WH
qsqx23y7fziLCiJE1k7dJwt2IEhQJrdhpcy8UrUEf9F/HyB0RJw0i6/5aswg/6gw
EVR+qbECD/osvRsZQTLCK+66z2jleK/Ooh0Wj4mrhiTsDdNgGK5W/TGVoeeKxGnm
CBnBW2cvz0o4RUw3jGY1AGSYvIYxy7qGsa6XAn0C1NkIc9dUoV8XhhH1Wo3uQbHO
-----END CERTIFICATE-----
AnyNet_Root_CA_2
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-11-2024 05:20 AM
Thank you @S-Battermann for the new certificate. I tested and it's working.
I even update the full procedure from my older post.
Cosmin
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-11-2024 05:21 AM
Any chance you can share method how you got this certificate?
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-11-2024 05:34 AM
Found the same certificate - Was given to me directly from Anydesk support
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-11-2024 06:07 AM
Was given to me directly from Anydesk support
- 16909 Views
- 30 replies
- 7 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Access to XSOAR Community edition in Cortex XSOAR Discussions
- Extending VLAN through IPSEC + GRE in General Topics
- Upgrade to GlobalProtect 6.2.3 client for Windows Does Not Complete in GlobalProtect Discussions
- Detect and Restrict Powershell cmdlets in Cortex XDR Discussions
- Automation rule to add IP address to EDL in Cortex XDR Discussions