- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Force user credentials at every login Azure AD SAML SSO
- LIVEcommunity
- Discussions
- Network Security
- GlobalProtect Discussions
- Force user credentials at every login Azure AD SAML SSO
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Force user credentials at every login Azure AD SAML SSO
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-04-2024 01:26 PM - edited 04-04-2024 01:30 PM
I have had GlobalProtect working for years with RADIUS based authentication and MFA. We are now moving to SAML based SSO with Azure AD. I have everything working, but, our environment requires that we provide login credentials every time we login to the VPN. So instead of using the credentials of the user that is logged into the machine by default, I want to force the user to enter their credentials, and supply MFA response, EVERY time they login to GP (even though the credentials in the end are the same as the user's Windows credentials)
I've changed all kinds of settings in the Portal - Agent - App settings, but nothing accomplishes what I need. When we use Azure AD SAML auth programatically, we send the "ForceAuthn=true" attribute, but I've not found anywhere to add custom attributes, or set something like this, in GP settings.
Anyone have suggestions?
Tavoca, Inc
Director of IT
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-04-2024 02:53 PM
Hello,
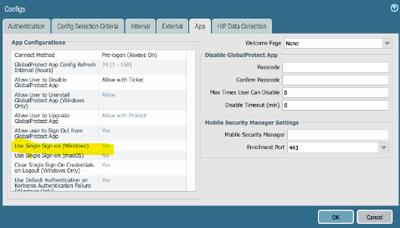
Do you have the configuration set to "No"?
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClFbCAK
Setting to yes will try and use the windows creds.
Regards,
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-05-2024 06:51 AM - edited 04-05-2024 07:09 AM
As Otakar said.. also in my case this is set to yes.
also a good thing i found is to set 'IPv6 preferred' to 'no' in the app settings on the portal.
re forcing MFA..
I had a similar issue some time back.. in the end, the change (if i recall correctly) needed was on the Azure end.. if i recall the Azure engineers had to set a time limit on the MFA request.. by creating a new azure access policy that will request mfa authentication every 1 hour think the minimum was 1 hour it can be set to for the gp vpn user groups.
the thing with Azure MFA is, if a user is connected and they simply disconnect, then reconnect, the GP app will simply use the Azure's Realtime Refresh Tokens' (RFT) (look it up.. a good read) to auto validate the MFA.. so the user won't get MFA response again if reconnecting within a certain amount of time. however if they go to the GP app settings, and sign out, then reconnect, then they will be prompted for MFA.
Just to clarify also, there are 2 options, disconnect and sign out (pending on how gp app is setup on palo side). if a user disconnects it preserves the user credentials, whereas if they 'sign out' it will clear the user credentials locally in the cache store. there is no way to force it to clear the credentials when user selects 'disconnect' that i am aware off.
i will try and find out from the Azure team what they did but might also have included some conditional access policies on the Azure end to be created.
unfortunately as I write this it is a Friday afternoon.. so the guys have long gone home and sipping on the good stuff by now. so will try and find out next week for more info and post an update.
have a great weekend!
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-05-2024 07:12 AM
Thank you. I've experimented with that setting. Neither setting accomplishes what I need unfortunately.
Tavoca, Inc
Director of IT
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-05-2024 07:15 AM
Thank you. I wondered if it was something I would have to do on the Azure side, but have hit dead ends going that route as well. The RFT reference may be helpful, so I'll start reading :).
I will also review the sign out vs disconnect. Right now my GP is set to just offer disconnect, so I'll switch that to sign out and see if that accomplishes what I need.
Tavoca, Inc
Director of IT
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-09-2024 06:22 AM
PA_nts - you got me going in the right direction. I ended up moving our org from the Azure Security Defaults to managing authentication with Conditional Access policies. I created a policy that forced authentication every time for my VPN users, and tied it to the Palo Alto GP Enterprise application. It now works beautifully. Asks for credentials every time, AND uses our company's MFA options. Bonus is that I now have more granular control over authentication policies in my organization.
Thanks for the help!
Tavoca, Inc
Director of IT
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-09-2024 06:27 AM
awesome glad to you hear you got it working.. happy days!
- 595 Views
- 6 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- After Endpoint Traffic Policy Enforcement, client can not be access microsoft login portal for smal auth. in GlobalProtect Discussions
- GP Portal logs showing local password guessing attempts even though I'm using Azure IdP. Should I be concerned? in GlobalProtect Discussions
- LDAP User based policy not working in Next-Generation Firewall Discussions
- Palo Alto with Azure SAML issue in GlobalProtect Discussions