- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
GlobalProtect | External Gateway | SAML | Reconnect Issue
- LIVEcommunity
- Discussions
- Network Security
- GlobalProtect Discussions
- GlobalProtect | External Gateway | SAML | Reconnect Issue
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
GlobalProtect | External Gateway | SAML | Reconnect Issue
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-17-2024 06:44 AM - edited 02-17-2024 07:04 AM
Hello,
I implementing GlobalProtect as our main VPN Solution and got it working so far.
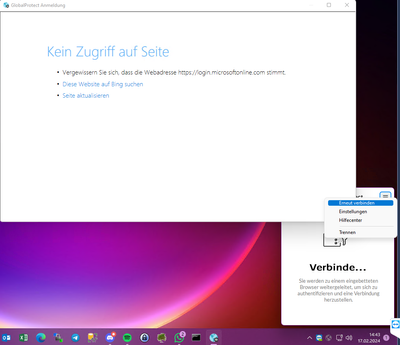
When I stress-test the GlobalProtect Client (imitating a stressed busy user who clicks on reconnect / "erneut verbinden in a short time frame) I get "no acces to site / kein zugriff auf seite" error in the integrated browser.
I have to close the "kein zugriff auf seite" window because global protect awaits the window to be closed to continue working.
If I now close the "kein zugriff auf seite" window
When I press "connect / verbinden" the windows with "kein zugriff auf seite" appears by a 50:50 chance. But mostly the connection works than...
If I press "disconnect / trennen" and than on "connect / verbinden" instead of "reconnect / erneut verbinden" the same page with "kein zugriff auf seite" opens sometimes but not as often as when I try a reconnect....
--> the connection itself can be established if I retry closing the windows and pressing connect once or twice thats not the big deal...
--> the big problem at all is, that global protect stops working until the Window "kein zugriff auf seite" is closed...
It would be perfect to display a custom error message: please close this window and try reconnect again ... because with the "kein zugriff auf seite" error page we will get a huge and never ending load of tickets and support calls I guess
PS: I already changed the setting in the gateway "app ribbon" already to the "default browser" and testet it -> the auth site opens at least, but sometimes (in case the browser is in the background the user does not even see the auth page)
Side-Notes:
1. For successfull connected users the whole microsoft IP ranges are split tunneled (I can confirm this when I inspect the routes on the windows clients)
2. in case the integrated browser of global protect runs over our infrastructure I created some policys to the FQDN login.microsoftonline.com with no IDS, URL filtering etc) and application / service any -> the result stays the same "no access to site / kein zugriff auf seite) when the integrated browser appears.
3. I stopped the PanGPS Service on a test client and deleted the folder (C:\Users\%USERNAME%\AppData\Local\Palo Alto Networks\GlobalProtect) -> error appears again if I reconnect shortly after connecting
4. I tested with different global protect clients (5.x, 6.2.0, but mostly i am testing with 6.2.2) -> same effects.
Any other ideas I can optimize the user experience ?
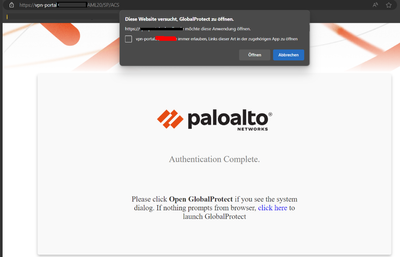
and: Is there a way to edit the Design of Global Protect with company branding or the response page for the global protect saml auth ? (see the last screenshot)
thank you very much
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-19-2024 04:01 AM
If you need to account for very nervous users, you could consider enabling authentication cookies on the gateway
The minimum value you can set these to is 5 minutes which should allow for nervousness but not interfere with SAML conditional access
the SAML login page can be branded, but this needs to be done on the SAML IdP side as this page is served by the IdP instead of the palo
that last page you display can't be changed I think, only the welcome, help and portal login/home pages
PANgurus - Strata specialist; config reviews, policy optimization
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-20-2024 03:58 PM
Hi, try set the TCP handshake to 60, it helped me. (PAN-227368 bug)
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-11-2024 07:53 AM
Im running into the same issue but we are still on PanOS 10.1.x and GlobalProtect 5.2.13.
I first want to upgrade PanOS to 10.2.8 and GP to 6.0.8 or 6.1.4 before i start troubleshooting this issue.
Which PanOS are you running on Portal/Gateway Firewalls?
10.2.6: Did you maybe tried already to increase the TCP Handshake to 60 like mentioned in PAN-227368 ?
thanks,
- 449 Views
- 3 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Global Protect for IPad auto-connect option partially works in GlobalProtect Discussions
- Problem Using New Digitally Signed Certificate in GlobalProtect Discussions
- Way to dual-boot MacOS without violating encryption requirements for GlobalProtect? in GlobalProtect Discussions
- Global protect Android version 13 mobile users not connecting portal issue. The network connection is unreachable, or the portal is unresponsive issue in GlobalProtect Discussions