- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
HIP Checks failing GP failing GP users called in ACL's when source device is Apple
- LIVEcommunity
- Discussions
- Network Security
- GlobalProtect Discussions
- HIP Checks failing GP failing GP users called in ACL's when source device is Apple
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
HIP Checks failing GP failing GP users called in ACL's when source device is Apple
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-18-2023 09:27 AM - edited 12-18-2023 09:32 AM
Hi All,
So I have Global Protect running with the HIP license. Our current conditions for HIP connectivity are; 1. Must be Windows 10 or 11, must have Crowdstrike installed and running, must have Zscaler Client Connector installed and running. I have no problems with any of these users.
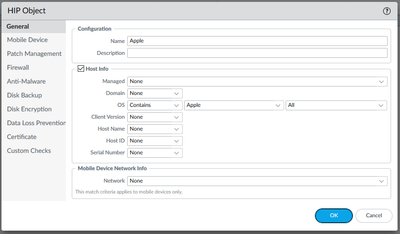
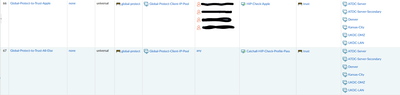
However, we have a very small subset of users on Macbooks, iphones and ipads that need to use Global Protect. So what I've done is created ACL's, calling the specific source usernames (pulled from Azure) who require those Apple devices, and gave them special ACL permissions above the "catchall" GP ACL line everyone hits (Windows, Crowdstrike, Zscaler) with their own special HIP check that only looks for "source device is Apple," so that the end result SHOULD be only these 2 or 3 users are allowed to use Apple devices, and that they rest of the users still have to use Windows, and hit the catchall GP ACL and HIP check below it.
What I'm seeing is the Apple users still fail the HIP check, even though I've created and applied a special HIP on their ACL that only looks for Apple devices as the condition, along with their specific source usernames/accounts. I can even set a line for those users and not have any HIP check enabled on said line, and it will still block them on the catchall. I've set it to "any" and "none," but neither work.
It's like the Palo is not recognizing the source user matches that special ACL line and moves right to the catchall GP line, which causes them to fail since the Catchall HIP looks for Windows. What makes it even stranger is when I check the HIP monitor, it's hitting the right HIP check for those users (the special Apple one I created), so that leads me to believe it IS in fact recognizing the source user, but it's still failing HIP for them.
Any ideas are greatly appreciated. Here are some screenshots attached. Right now my leading guess is that HIP just doesn't work very well if you start adding multiple ACL's based on the source user?
Edit: If I put the "Apple" HIP object as an OR condition on the catchall HIP check and ACL line, then it works fine, but that also allows ANYONE to use Apple devices OR Windows devices, and I don't want that. I only want this handful of users to be able to use Apple devices, and everyone else to ONLY be able to use Windows.
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-20-2023 07:46 AM
Hi @dromanelli
"I can even set a line for those users and not have any HIP check enabled on said line, and it will still block them on the catchall. I've set it to "any" and "none," but neither work. "
Above statement indicates that the problem is not with the HIP, but with user-id matching.
In order traffic to be allowed over the firewall it has to match all the critiria applied on that rule. This means that once the users connect to GP, they needs to match one of the usernames AND the HIP profile. If you remove the HIP profile from the rule, this means traffic is not match the username in your rule.
Palo Alto user identification works by creating ip-to-user mapping, basically mapping a source IP to username. When packet hit the firewall it will get the username from that mapping and will perform policy lookup to search for rule matching source network AND source username AND HIP profile.
- What authentication are you using for your GP? Local (creating users locally on the firewall)? or Remote (LDAP, RADIUS, SAML etc)?
- If you are using remote authentication, are you using group mapping? Group Mapping (paloaltonetworks.com)
- How did you define the username in the rule? Manually type them or select them from the dropdown?
I am almost certain that your problem is in the user identification and not in the HIP, but you can easily confirm this by looking at the HIP logs. Go to Monitor -> HIP Match. There you can filter by username or IP address and see what HIP object and HIP profiles that user has matched. Try to connecting with MacOS and check the HIP logs
- 293 Views
- 1 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Panorama - Failed to update content with following message: encfilesize is 91736928 in Panorama Discussions
- Failed to install licenses. Web proxy license is not supported for this platform. in Next-Generation Firewall Discussions
- Cloud Identity Engine - Failed to get client configuration in GlobalProtect Discussions
- Firewall fails to register to Wildfire appliance in Next-Generation Firewall Discussions
- GP Connection Failed - gateway could not verify the server certiticate of the gateway. in GlobalProtect Discussions