- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Multi Factor Authentcation (Privacy Idea) just for some Users
- LIVEcommunity
- Discussions
- Network Security
- GlobalProtect Discussions
- Multi Factor Authentcation (Privacy Idea) just for some Users
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-15-2024 12:20 AM
Good Morning,
we are using Palo Alto 3020 (installed sw 9.1).
We recently tried to implement multi factor authentication with privacy idea. We followed this guide and everything works.
https://www.youtube.com/watch?v=2mIuqmWP-j0&t=1200s
The main problem is that we would like to be able to decide which users should use mfa and which should simply use username and password. we haven't found any way to achieve the goal, the only thing that can be done is to differentiate by operating system. If I moved to the new versions (11) there would be a possibility
Thanks for your help
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-16-2024 06:05 AM
While multiple gateways used to be a licensed feature, that's no longer the case and is included with the product. You really could do this with either multiple portals or you could just leverage multiple gateways and client configurations to direct the user to the proper gateway with the additional MFA authentication or not.
The advantage of using multiple gateways instead of multiple portals is that you can give out the same portal address regardless of the user and never have to go through a portal migration. The downside is that authentication is ever so slightly more annoying when you're enforcing MFA on the gateway, but not massively so. Multiple portals is the "cleanest" way of doing things in my mind, you just have to be mindful that you won't have a single portal address to communicate to all of your users.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-15-2024 04:08 AM - edited 02-15-2024 04:10 AM
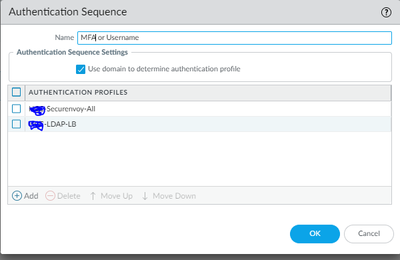
Have you tried using an "authentication sequence".
This way you could put MFA profile at the top of the list and username/password below it. (or the other way around)
If the users are not configured for MFA then the 3020 will try username/password.
If it's the other way round then if your users are not configured for username/password then the 3020 will try MFA.
That's my understanding but never had to use it...
From Palo....
In some environments, user accounts reside in multiple directories (such as LDAP and RADIUS). An authentication sequence is a set of authentication profiles that the firewall tries to use for authenticating users when they log in. The firewall tries the profiles sequentially from the top of the list to the bottom—applying the authentication, Kerberos single sign-on, allow list, and account lockout values for each—until one profile successfully authenticates the user. The firewall only denies access if all profiles in the sequence fail to authenticate. For details on authentication profiles
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-15-2024 04:28 AM
Thank you for your answer. I tried to use it but not solved my problem. We don't have multiple direcorories, users are in AD/ldap and our problem is to understand if there is a way to differentiate users based on ldap group or in another way. For example, if I belong to group x I proceed with username and password, if instead I belong to y I will authenticate with mfa.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-15-2024 05:09 AM
Group membership is not available at this point as user has not actually authenticated.
do your users know which method they should be using?
I would have thought if you logged in with MFA and ldap was top of the list, the ldap auth will fail, it will then automatically try MFA which I assume would pass...
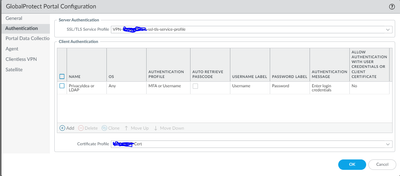
The only other option I can think of is to have a different portal for both sets of users... both portals point to the same gateways but use cookies for authentication override for that gateway.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-15-2024 05:27 AM
do your users know which method they should be using?
yes,
Different portal could be a good Idea. Do you have any reference guide to implement?
thank you
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-15-2024 07:49 AM
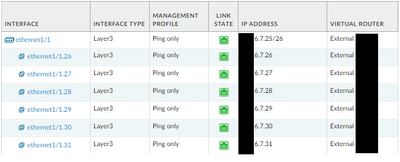
Could I assign a multiple address (/32) on external interface in order having multiple gateways?
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-15-2024 10:24 AM - edited 02-16-2024 01:30 AM
Do you mean multiple portals, multiple gateways may require additional GP license…
yes you can…. Select the network interface for you current portal and select add sub interface at bottom of page..
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-16-2024 06:05 AM
While multiple gateways used to be a licensed feature, that's no longer the case and is included with the product. You really could do this with either multiple portals or you could just leverage multiple gateways and client configurations to direct the user to the proper gateway with the additional MFA authentication or not.
The advantage of using multiple gateways instead of multiple portals is that you can give out the same portal address regardless of the user and never have to go through a portal migration. The downside is that authentication is ever so slightly more annoying when you're enforcing MFA on the gateway, but not massively so. Multiple portals is the "cleanest" way of doing things in my mind, you just have to be mindful that you won't have a single portal address to communicate to all of your users.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-16-2024 01:44 PM - edited 02-16-2024 01:47 PM
Thank you everybody for your answer. I will test multiple portal. I think this is right solution for my environment
- 1 accepted solution
- 793 Views
- 9 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!