- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Info about the vulnerabilities and the possible remediations for them.
- LIVEcommunity
- Discussions
- Network Security
- Next-Generation Firewall Discussions
- Info about the vulnerabilities and the possible remediations for them.
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Info about the vulnerabilities and the possible remediations for them.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-27-2023 07:45 AM
Dear All,
I hope you could help me with the query I could not find answer.
The customer is asking for the remediation of the detected vulnerabilities, which I've already researched and found some info about that I've grouped below:
Client Side Testing - OTG-CLIENT-004 - Testing for Client Side URL Redirect
------------------------------------------------------------------------------------------------------------------------
[P3: Medium] OTG-CLIENT-004: External redirect via host header injection.
*I found the below conversations form the Live community about it:
Global Protect - Redirection via Arbitrary Host Header Manipulation
GlobalProtect Qualys: 150307 External Service interaction via Host Header Injection
------------------------------------------------------------------------------------------------------------------------
Cryptography - OTG-CRYPST-001 - Testing for Weak SSL/TSL Ciphers, Insufficient Transport Layer Protection
------------------------------------------------------------------------------------------------------------------------
[P4: Low] OTG-CRYPST-001: Secure renegotiation not supported.
*As per my checks there ware actually 2 FRs for this feature in the past:
FR ID: 8112 (support for secure renegotiation / inbound SSL decrypt and GlobalProtect )
FR ID: 18516 (Support for RFC 5746 )
*And to fix this it's required to remove weak ciphers from CLI, and use the newest PAN-OS (10.2.5) version that should now support renegotiation:
As per: PAN-OS 10.2.5 Addressed Issues
PAN-184630 - Fixed an issue where TLS clients, such as those using OpenSSL 3.0, enforced the TLS renegotiation extension (RFC 5746).
Or we can refer to the KB: How to disable medium strength SSL ciphers for SSL/TLS Service Profile on Firewall
[P4: Low] OTG-CRYPST-001: Elliptic curves offered with insufficient level of security.
*And this article provides information on how to harden the SSH service running on the management interface by disabling weak ciphers and weak key (key exchange) algorithms
How to fix Weak Ciphers and Keys on the Management Interface for SSH Access
[P4: Low] OTG-CRYPST-001: Server potentially vulnerable to LUCKY13 attack.
[P4: Low] OTG-CRYPST-001: Insecure digital certificates - chain of trust.
missing info about remediation for last two vulnerabilities
------------------------------------------------------------------------------------------------------------------------
Configuration and Deploy Management Testing - OTG-CONFIG-001 Test Network/Infrastructure Configuration
------------------------------------------------------------------------------------------------------------------------
[P4: Low] OTG-CONFIG-001: Missing X-Permitted-Cross-Domain-Policies security header.
[P4: Low] OTG-CONFIG-001: Insecure HTTP header - X-XSS-Protection.
[P4: Low] OTG-CONFIG-001: Missing Referrer-Policy security header.
[P4: Low] OTG-CONFIG-001: Unsafe Content-Security-Policy security header configuration.
missing info about remediation
------------------------------------------------------------------------------------------------------------------------
Session Management Testing - OTG-SESS-002 - Testing for Cookies attributes
------------------------------------------------------------------------------------------------------------------------
[P5: Informational] OTG-SESS-002: Duplicate cookies set.
missing info about remediation
------------------------------------------------------------------------------------------------------------------------
Could anyone please advise in regards to vulnerabilities I have no info about, and the possible remediation, or point to some documentation about the same.
I will appreciate your help and guidance in regards to the vulnerabilities I've listed above.
Thank you in advance!
Cheers!
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-13-2023 03:15 AM
To keep you posted.
Following the PAN-OS firmware update to version 10.2.5 and the completion of a "PENTEST," vulnerabilities with P3 and P5 priority have been successfully resolved.
Only vulnerabilities categorized as P4 remain. 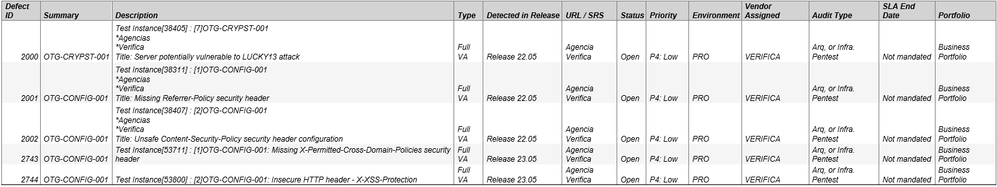
As the newer PAN-OS version is now recommended we will try to upgrade the software to version 10.2.6 and see if this will help.
We want also to verify that the newest content updates are installed on the firewall.
But could anyone maybe advise in regards to vulnerabilities, and the possible remediation, or point to some documentation about the same.
I will appreciate your help and guidance in regards to the vulnerabilities I've listed above.
Thank you in advance!
Cheers!
- 2547 Views
- 1 replies
- 1 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- PA850 last supported PANOS 11.1.x in Next-Generation Firewall Discussions
- Global Protect stable and non vulnerable version to upgrade in GlobalProtect Discussions
- Root Partition Full in Next-Generation Firewall Discussions
- CVE-2024-9474 PAN-OS: Privilege Escalation (PE) Vulnerability in the Web Management Interface in Next-Generation Firewall Discussions
- Palo Alto Vulnerability CVE-2024-8687 in GlobalProtect Discussions



