- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
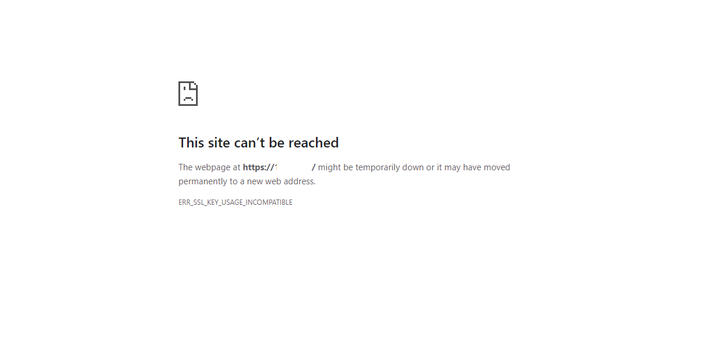
Palo Alto Login issue though GUI " ERR_SSL_KEY_USAGE_INCOMPATIBLE " (Solved)
- LIVEcommunity
- Discussions
- Network Security
- Next-Generation Firewall Discussions
- Palo Alto Login issue though GUI " ERR_SSL_KEY_USAGE_INCOMPATIBLE " (Solved)
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Palo Alto Login issue though GUI " ERR_SSL_KEY_USAGE_INCOMPATIBLE " (Solved)
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-10-2023 12:29 AM
For the last few days, we have been experiencing an issue with logging in to the Palo Alto Firewall through the GUI. We are getting the below error from the browser during login.
# delete deviceconfig system ssl-tls-service-profile
# commit
# exit
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-10-2023 11:22 AM
It is the issue with chrome not an issue of the firewall you will be able use Microsoft Edge and Mozilla Firefox and it will work.
There is a workaround you do for chrome:
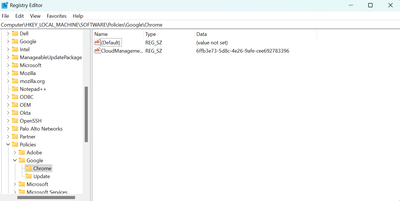
Open registry editor and go to the following path:
>HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Google\Chrome
> Right-click and > Add a new DWORD (32-bit) Value ,Changed the Name to RSAKeyUsageForLocalAnchorsEnabled and set the value as the default (00000000).
Close chrome and open again. You can reach out to to google through google support form for editing the key usage field and also check with your Certificate authority.
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-13-2023 03:14 AM
This is not only for Chrome we also experienced issues with the Mozilla browser. Only MS-EDGE is working
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-14-2023 03:00 AM
oh ok, but yeah as I said the issue from these browsers for key usage field in certificates you can check on their support forms to check if there any fix version or you can follow the same work around
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-01-2024 05:19 AM
my colleague found this article in the PA knowledgebase that seems to explain and resolve the issue:
welcome,
Please mark helpful responses, so others know as well
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-01-2024 06:48 AM
This one does not apply to another browser instead of Chrome.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-01-2024 09:26 AM
For at least one of our clients, we get this with Edge as well as Chrome. PAN-OS is at 10.1.10-h1 rather than 11 like Palo's KB says would be affected.
It is only with Palos that I've come across this. What gives?
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-27-2024 11:55 PM
Abdul & Dan - that's because you missed an important fact - it's a change in chrome behavior but Edge uses Chromium technology (which is what - surprise ! - Chrom is based on as well, therefore they both exhibit the same issue, but as Dan later replied, doesn't happen with Firefox because they use their own engine/tech whatever,
and the solution is - configure the Captive portal certificate with key usage specified (or disable the usage of "RSAkey" in chrome/Edge
Please mark helpful responses, so others know as well
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-06-2024 11:00 AM - edited 05-06-2024 11:20 AM
We are having this issue with both Chrome and Edge.
"configure the Captive portal certificate with key usage specified"
So, is it possible to do this with a self-signed certificate on the Palo Alto, or is it now required to issue said Certificate from a Certificate Authority? I don't see that option in the Palo Alto Certificate generation articles.
Deleting the ssl/tls service profile isn't an option for us, since we need that to enforce a minimum TLS version, which is required for PCI compliance.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-07-2024 02:47 PM - edited 05-07-2024 02:47 PM
Palo Alto confirmed in our support case that there is no available method to add the Key Usage extension to a self-signed certificate generated on the Palo Alto. The Certificate must be issued from a CA to add the Key Usage Extension.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-09-2024 07:43 AM - edited 05-09-2024 07:44 AM
Thank you! This worked perfectly for me. My connection to Panorama still wasn't working even after creating the registry edit suggested below. I console'd into the Panorama VM and deleted the ssl-tls-service-profile and now my connection works without issue.
- 6727 Views
- 11 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Issues with Captive Portal / Continue URL Filtering Response page on 10.1.12 in Next-Generation Firewall Discussions
- Warnings in certificate. in Next-Generation Firewall Discussions
- Known issue (Issue ID: PAN-227368) with version 11.0.2. Will it be solved by 11.1.0-h2 to upgrade? in Next-Generation Firewall Discussions
- Globalprotect Self Signed certificate with Chrome in GlobalProtect Discussions
- How to solve the Administrator Certificate-Based Authentication with issue of Redirection to prompt the username and password in Next-Generation Firewall Discussions