- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
What is Threat ID 40033 "DNS ANY Queries Brute Force DOS Attack"
- LIVEcommunity
- Discussions
- Cloud Delivered Security Services
- Threat & Vulnerability
- What is Threat ID 40033 "DNS ANY Queries Brute Force DOS Attack"
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
What is Threat ID 40033 "DNS ANY Queries Brute Force DOS Attack"
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-23-2023 01:08 AM
Hi All
I need to know about Threat ID 40033 "DNS ANY Queries Brute Force DOS Attack". I found the firewall drop traffic and hit the threat id-40033, but we try to packet capture with this traffic for DNS query for same source and same destination is not reach 500 times per 60 seconds. Why Palo drop the query packet? and what's traffic that hit list the threat id-40033?
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-23-2023 09:37 AM - edited 03-23-2023 09:38 AM
DNS ANY request means if client asks DNS server "give me all the data".
Now assume you host DNS server and receive DNS ANY request with forged source IP.
Incoming packet to you is small but outgoing packet you send out is big.
This can be used in DDoS attack if attacker sends DNS ANY requests with spoofed source IP of the victim.
DNS servers reply to victim and effectively attacker has achieved amplification attack.
You can test how DNS ANY request looks like from your computer command line:
nslookup -type=any www.ee
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-26-2023 07:32 AM
Thanks, I want to known, what traffic can be the cause of hit the Threat-ID?
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-26-2023 09:53 AM - edited 03-26-2023 09:57 AM
DNS ANY request generates threat id 34842 (DNS ANY Request).
Multiple DNS ANY requests in a row generate 40033 (DNS ANY Queries Brute Force DOS Attack).
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-26-2023 11:12 PM
How can I check for this matter?
"Now assume you host DNS server and receive DNS ANY request with forged source IP."
"Incoming packet to you is small but outgoing packet you send out is big."
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-27-2023 05:20 AM
DNS ANY is logged under threat id 34842 so you can check firewall threat log using filter below..
( threatid eq 34842 )
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-27-2023 10:24 PM
According to the KB,
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClmpCAC
40033 is triggered if a session has same source and same destination but triggers our child signature, 34842, 250 times in 30 seconds. (not 500 times per 60 seconds).
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-27-2023 10:44 PM - edited 03-27-2023 10:45 PM
Every time computer tries to resolve DNS request it will send out request to every DNS suffix it has.
In addition depending on operating system it might send those requests to all its DNS servers simultaneously .
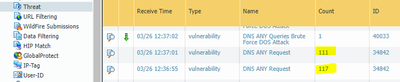
Add count column and you see that single line can actually be multiple events.
Below is small demo I ran through firewall.
Palo Alto Networks certified from 2011
- 7106 Views
- 7 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Cortex License Query in Endpoint (Traps) Discussions
- Difficulty Converting Dates to String Format in XQL Query in Endpoint (Traps) Discussions
- How to query historical logs in Enterprise Data Loss Prevention Discussions
- Query for CVE-2024-3400 in Threat & Vulnerability Discussions
- Query regarding CVE-2024-3400 in Threat & Vulnerability Discussions