AWS Scripts and Templates
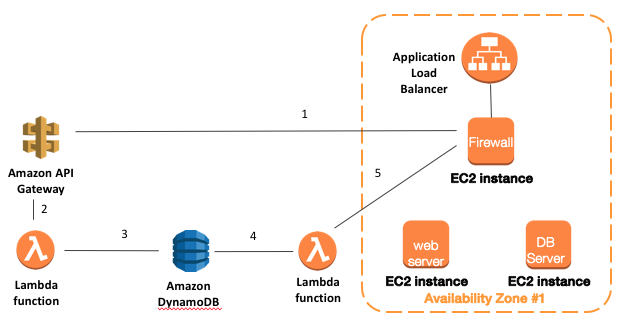
Amazon GuardDuty to VM-Series Integration
Uses an AWS Lambda function to feed Amazon GuardDuty threat intelligence to the VM-Series for security policy execution.
Palo Alto Networks Community Supported
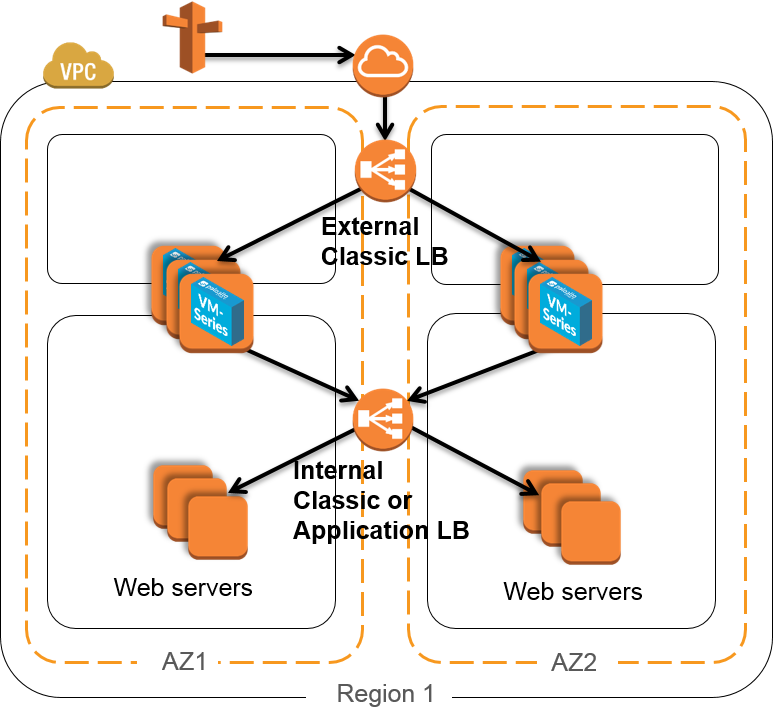
Auto Scaling the VM-Series on AWS
A set of templates and scripts that deploys an AWS Load Balancer sandwich and the VM-Series firewalls to deliver an Auto Scaling solution for securing internet facing applications.
Auto Scaling the VM-Series on AWS
A set of templates and scripts that deploys an AWS Load Balancer sandwich and the VM-Series firewalls to deliver an Auto Scaling solution for securing internet facing applications.
Auto Scaling the VM-Series on AWS
A set of templates and scripts that deploys an AWS Load Balancer sandwich and the VM-Series firewalls to deliver an Auto Scaling solution for securing internet facing applications.
Auto Scaling VM-Series firewalls on AWS Version 2.1
A set of templates and scripts that deploys AWS Load Balancers and the VM-Series firewalls to deliver an Auto Scaling solution for securing internet facing applications. New in this version is the ability to protect existing workloads as well as net new.
Auto Scaling GlobalProtect on AWS
A sample prototype for Auto Scaling GlobalProtect on AWS.
Palo Alto Networks Community Supported
https://github.com/PaloAltoNetworks/aws/tree/master/globalprotect-asg
Auto Scaling the VM-Series on AWS with Terraform
Terraform Template that deploys an AWS Load Balancer sandwich and the VM-Series firewalls to enable Auto Scaling.
Palo Alto Networks Community Supported
https://github.com/PaloAltoNetworks/terraform-templates/tree/master/aws_elb_autoscale
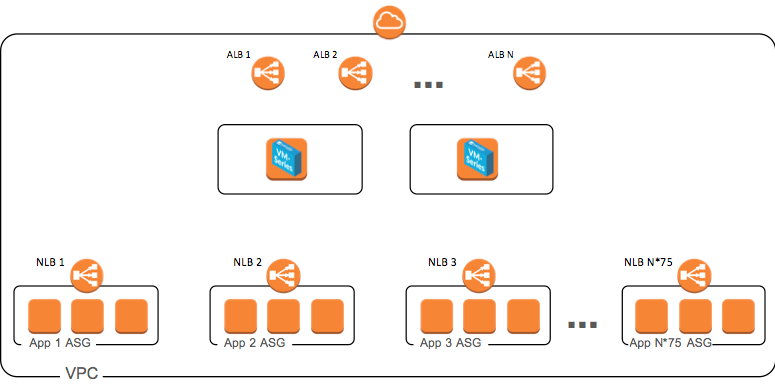
ALB/NLB Load Balancer sandwich for managed scale/high availability
Templates and scripts that deploy an AWS ALB/NLB Load Balancer sandwich and two VM-Series firewalls to deliver managed scale and high availability for inbound applications.
Palo Alto Networks Community Supported
Palo Alto Networks NAT Rule Updater
A process for keeping NAT rule destination IPs in sync with changing Elastic Load Balancer VIPs. A Lambda function is used to retrieve the latest ELB VIPs and updates the NAT destination IP if necessary. The process uses naming conventions and instance tagging for configuration.
Partner Community Supported
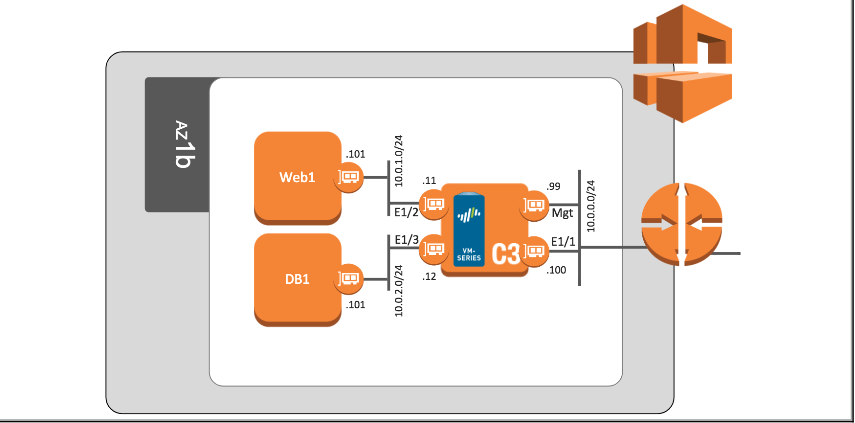
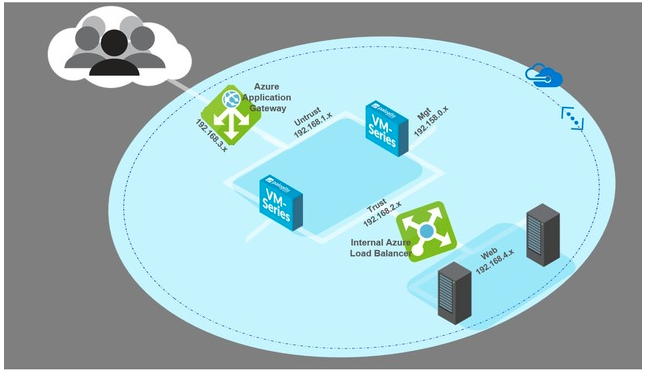
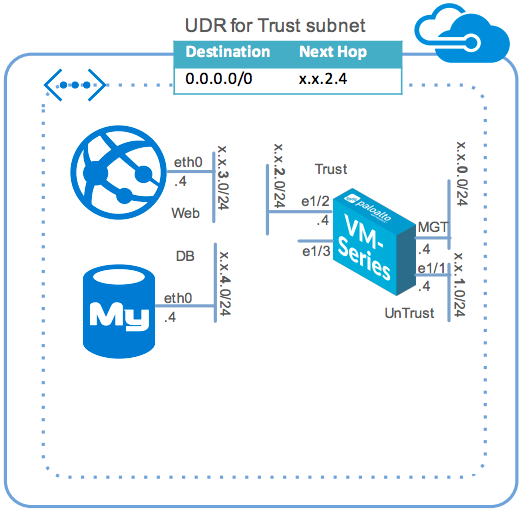
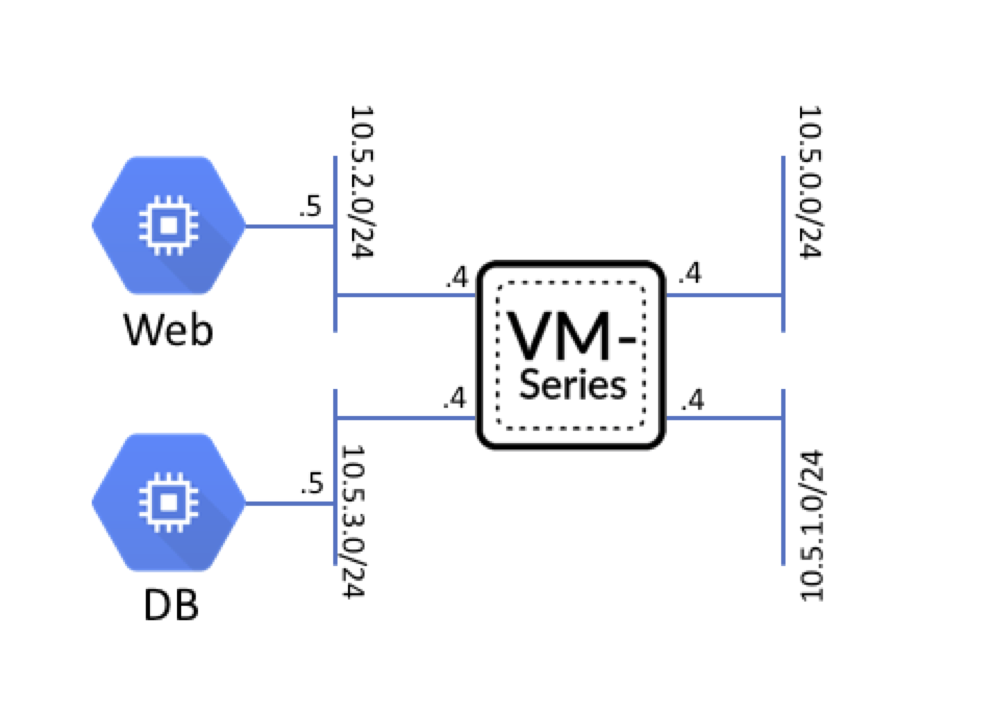
Hybrid arch/two tier application environment protected by VM-Series
Sample AWS CloudFormation Template that deploys a two-tiered web/DB application environment secured by a VM-Series firewall.
AWS two-tier sample deployed with Terraform
Terraform template that deploys a two-tier web/DB application on AWS secured by a bootstrapped VM-Series firewall.
Palo Alto Networks Community Supported
https://github.com/PaloAltoNetworks/terraform-templates/tree/master/aws_two_tier
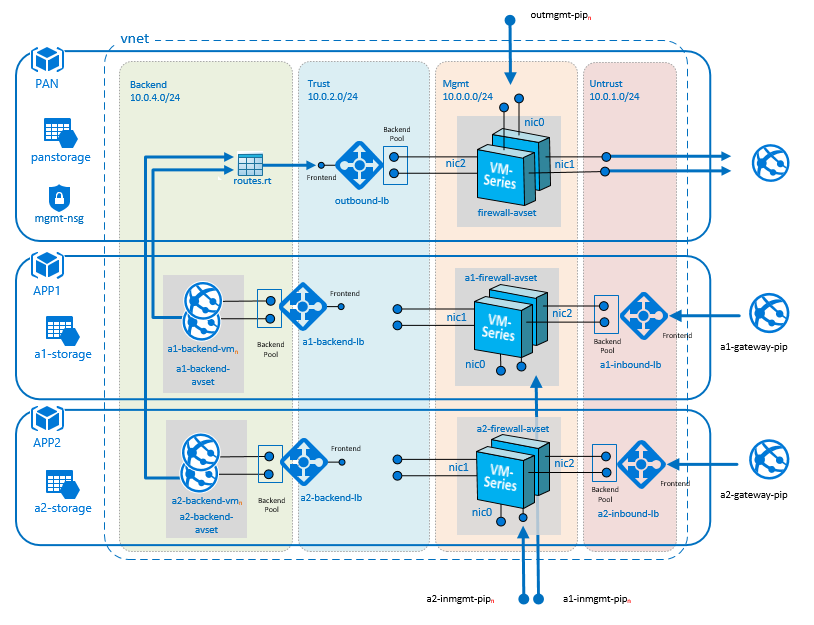
AWS two-tier sample deployed with Terraform & Ansible
Deploys a two-tiered web/DB and bootstrapped VM-Series firewall using a Terraform Template. The VM-Series is then configured using Ansible scripts.
Palo Alto Networks Community Supported
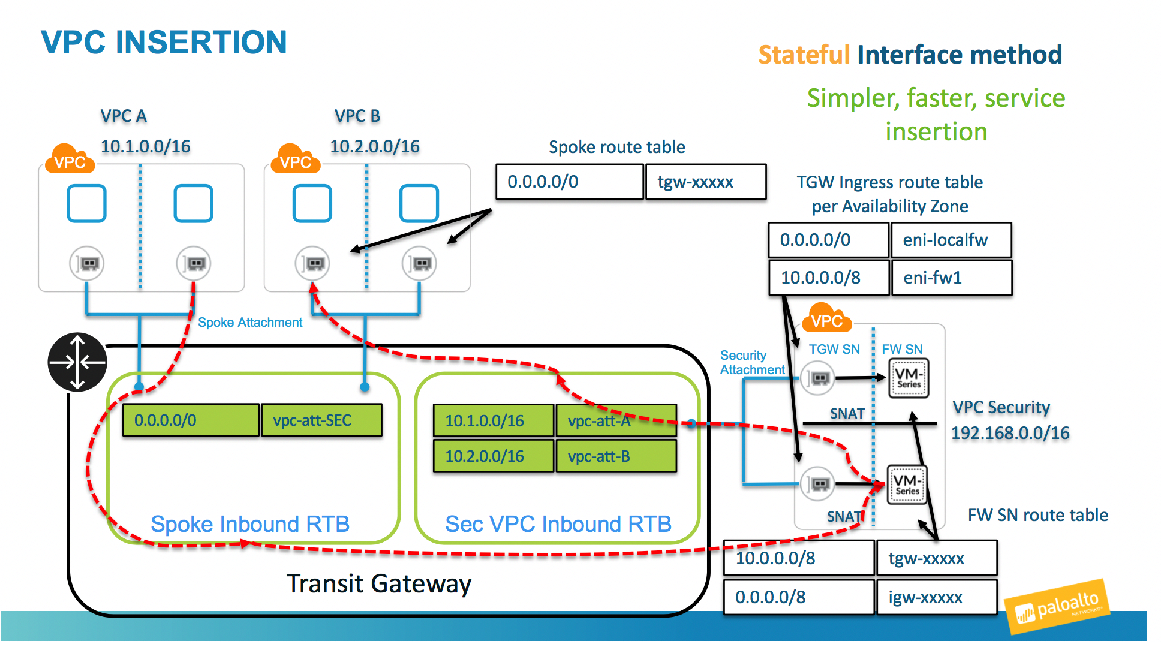
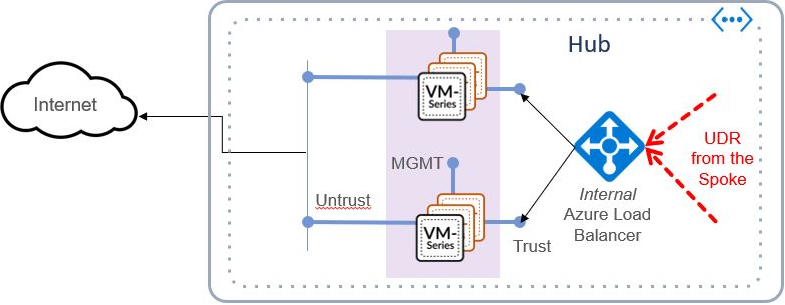
Transit VPC with the VM-Series on AWS
The AWS Transit VPC is a highly scalable architecture that provides centralized security and connectivity services. Our VM-Series integration with the Transit VPC allows for a fully automated method of securely attaching subscribing (spoke) VPCs to the transit VPC.
Palo Alto Networks Community Supported
Transit VPC Manual Build Step-by-Step Guide
Guides user through the process of building a Transit VPC with the VM-Series. Once completed, the user will have built a Hub, and 3 subscribing VPC spokes.
Palo Alto Networks Community Supported
AWS Transit Gateway – Manual Build
Step by step guide to deploying a Transit Gateway within a Transit VPC with the VM-Series.
Palo Alto Networks Community Supported
Transit VPC CloudFormation Template
CloudFormation Template that a automates the deployment of a Transit Gateway within a Transit VPC with the VM-Series.
Palo Alto Networks Community Supported
https://github.com/PaloAltoNetworks/TransitGatewayDeployment
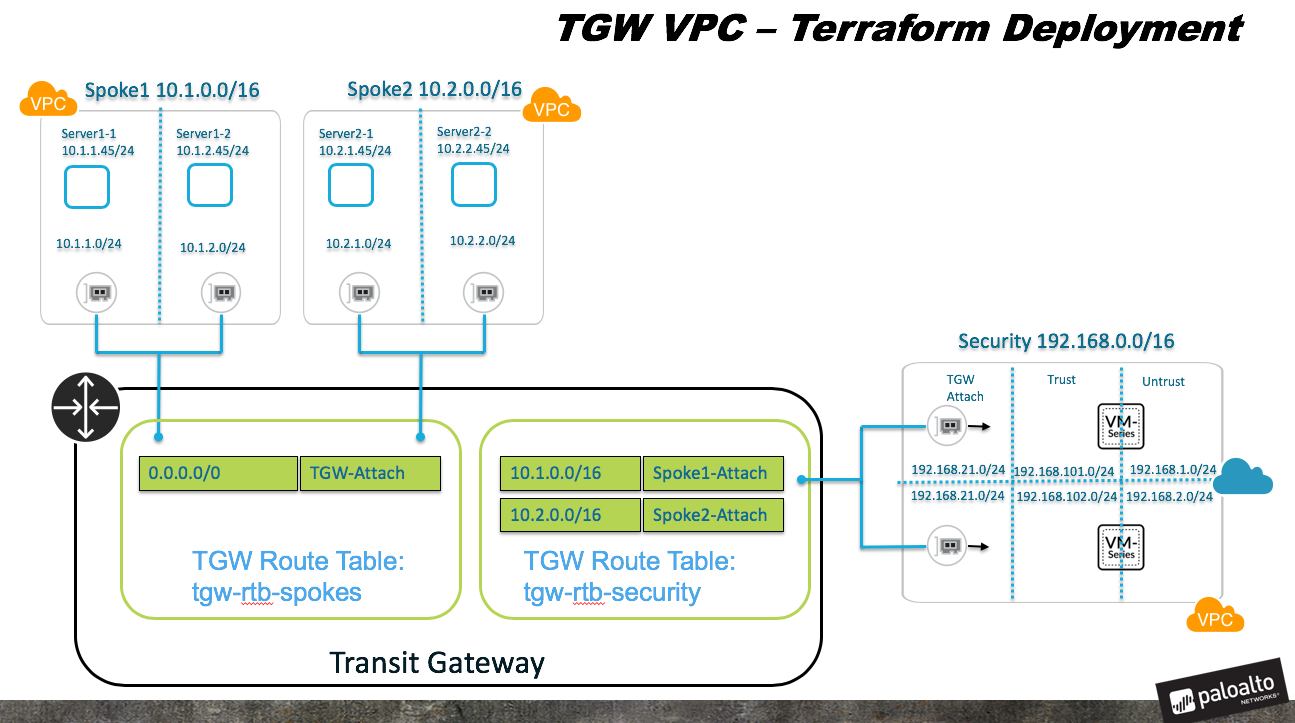
Transit Gateway Deployment for North/South and East/West Inspection
Terraform Template that a automates the deployment of a Transit Gateway within a Transit VPC with the VM-Series.
Palo Alto Networks Community Supported
Using User-ID to block malicious source IPs
Enables the VM-Series to block malicious source IP addresses when deployed behind a Source NAT device like an AWS ALB by feeding X-Forward-For header to User-ID.
Palo Alto Networks Community Supported