- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Tips & Tricks: Packet Buffer Protection (PBP)
- LIVEcommunity
- Articles
- General Articles
- Tips & Tricks: Packet Buffer Protection (PBP)
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
on 10-11-2023 12:14 PM - edited on 10-18-2023 08:37 AM by jforsythe
To protect your firewall and network against single-source denial of service (DoS) attacks that can wreak havoc on your packet buffer and disrupt your legitimate traffic, Palo Alto Networks firewalls have a feature called Packet Buffer Protection (PBP).
This feature was introduced way back in PAN-OS 8.0 but was disabled by default at the time. Starting from PAN-OS 10.0, PBP is enabled by default, globally and on each zone. As a best practice make sure you've got PBP activated both globally and within each zone. It serves as an extra layer of protection against DoS attacks, aggressive sessions, and unruly sources that could otherwise wreak havoc on your firewall's buffers. It spots those troublesome sessions, and uses Random Early Drop (RED) as the first line of defense. And it doesn't stop there – if the abuse persists, it's quick to take action, either by booting out the problematic session or giving the unruly IP address a timeout. When your firewall notices a flurry of small sessions or rapid session creation, especially from a particular IP address, it knows when it's time to slam the gate shut on that address.
In short, it's not just a feature – it's your firewall's bodyguard. Keep PBP turned on, and you'll keep your network safe and sound.
PBP works with thresholds so it's recommended to start by establishing baseline measurements of the firewall's packet buffer usage. This will help you recognize any significant spikes in buffer usage, making it clear that the only time you should see such spikes is during an actual attack. You can also start with the default threshold values and adjust as necessary.
You can find this option on the Device tab > Setup > Session > Session Settings
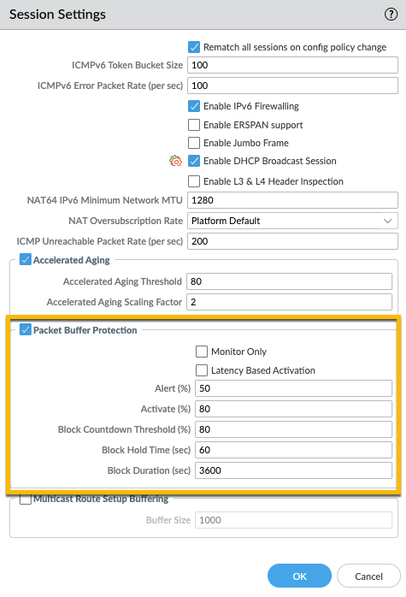
Alternatively, you have the option to activate Latency Based Activation, which responds to CPU processing latency, giving you a set of different thresholds to configure:
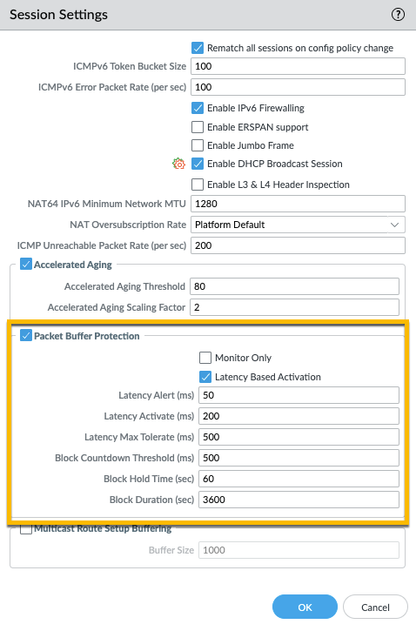
It's important to note that PBP isn't part of the Zone Protection profile or a DoS Protection profile or policy rule. Instead, it operates autonomously, pinpointing troublesome traffic by monitoring buffer utilization, the very resource it's designed to protect. You have the flexibility to manually set the threshold at which RED kicks in to start dropping packets for the offending session. In many cases, RED can do a fantastic job of keeping your buffers in good shape by only dropping specific problematic traffic. When active sessions threaten to deplete the buffer, the firewall's first response is typically to discard the session, rather than blocking the host. However, in the case of non-existing sessions, blocking becomes the sole option.
The cherry on top is that configuring PBP is much simpler compared to setting up DoS policies as there are fewer threshold values to manage. Additionally, you can fine-tune the hold-down timer and specify the duration for which a host should be blocked, giving you added control and flexibility in managing your firewall's security.
For more information on how to Enable Packet Buffer Protection, please review the following article: Packet Buffer Protection
Feel free to share your questions, comments and ideas in the section below.
Thank you for taking time to read this blog.
Don't forget to hit the Like (thumbs up) button and to Subscribe to the LIVEcommunity Blog area.
Kiwi out!
Hi, thank you for this article.
I have two points I would like to clarify:
1. "Latency Based Activation, which responds to CPU processing latency"
2."in the case of non-existing sessions, blocking becomes the sole option"
We apply PBP but the malicious sessions are never blocked, only dropped(even with the block countdown lower than the activate threshold). Also the CPU is increasing before the PBP is triggered and reaches 100% when the activate is passed.
So why malicious sessions are not blocked? I think your point 2 is not correct, because it is the flood protection applied to the zone responsible to Block new sessions and not the PBP(which is working with existing sessions).
For point 1, does this mean that "Latency Based Activation" can help to detect an increase in the CPU and trigger PBP?
Thank you in advance.
Kind regards
- 5324 Views
- 1 comments
- 5 Likes
- 270 Subscriptions
-
"Address Objects"
1 -
10.0
2 -
10.1
2 -
10.2
3 -
8.1
1 -
9.0
1 -
9.1
1 -
Active-Passive
1 -
AD
1 -
address objects
1 -
admin roles
1 -
administration
6 -
Administrator Profile
1 -
Advanced URL Filtering
2 -
Advanced Wildfire
1 -
Alibaba
2 -
Alibaba Cloud
3 -
Ansible
1 -
antivirus
1 -
API
2 -
applications
1 -
Asset Management
1 -
Authentication
6 -
Authentication Profile
1 -
Authentication Sequence
1 -
automatically acquire commit lock
1 -
Automation
3 -
AWS
6 -
Azure
1 -
Basic Configuration
4 -
Beacon
2 -
Beacon2020
1 -
Best Practices
2 -
Block List
1 -
categories
1 -
certificates
1 -
Certification
1 -
Certifications
1 -
Certifications & Exams
1 -
CLI
4 -
CLI command
3 -
Cloud Automation
1 -
Cloud Identity Engine
1 -
Cloud NGFW
1 -
Cloud Security
1 -
Commit Process
1 -
Community News
1 -
Configuration
9 -
Configure Next Generation Firewall
1 -
console
1 -
Cortex
1 -
Cortex Data Lake
2 -
Cortex XDR
4 -
COVID-19
1 -
cyber elite
1 -
Cyberelite
11 -
dag
2 -
Debug
1 -
debugging
2 -
Default Policy
1 -
Deployment
1 -
discussions
1 -
EDL
3 -
Education
2 -
Education and Training
2 -
Education Services
2 -
Educational Services
1 -
Effective Routing
1 -
Endpoint
1 -
ESXi
1 -
events
1 -
expedition
1 -
export
1 -
failover
1 -
FAQ
1 -
Filtering
2 -
Firewall
2 -
Firewall VM-Series
2 -
gateway
1 -
Gateway Load Balancer
3 -
Gateway Loadbalancer
2 -
GCP
5 -
GCP Firewall
1 -
geolocation
1 -
Getting Started
1 -
Github
1 -
Global Protect
1 -
Global Protect Cookies
1 -
GlobalProtect
8 -
GlobalProtect App
1 -
globalprotect gateway
1 -
GlobalProtect Portal
2 -
google
2 -
Google Cloud
3 -
google cloud platform
4 -
GWLB
3 -
Hardware
2 -
hash
1 -
Header Insertion
1 -
High Availability
1 -
How to
1 -
HTTP
1 -
https
1 -
Hybrid Cloud
1 -
ike
3 -
import
1 -
Installation & Upgrade
1 -
IoT
2 -
IoT Security
1 -
IPSec
3 -
kerberos
1 -
Kubernetes
1 -
Layer 2
2 -
Layer 3
1 -
Learning
1 -
licenses
1 -
local user
3 -
log forwarding
1 -
Log4Shell
1 -
Logging
2 -
login
1 -
Logs
3 -
Malware
1 -
Management
8 -
Management & Administration
5 -
MFA
1 -
microsoft
2 -
Microsoft 365
1 -
minemeld
25 -
multi factor authentication
1 -
multi-factor authentication
1 -
multi-vsys
1 -
Network Security
37 -
network-security
1 -
Networking
1 -
New Apps
1 -
News
1 -
next-generation firewall
42 -
next-generation firewall. network security
1 -
Next-Generation Firewall. NGFW
4 -
NGFW
21 -
NGFW Configuration
10 -
Objects
2 -
Oracle Cloud
1 -
Oracle Cloud Infrastructure
1 -
OTP
1 -
PA-3200 Series
1 -
PA-400
1 -
pa-440
2 -
PA-5400 series
1 -
PA-800 Series
1 -
pa-820 firewall
1 -
Packet Buffer
1 -
packet debug
1 -
packet diag
1 -
PAN-OS
17 -
PAN-OS 10.2
1 -
PAN-OS 11.0
1 -
PAN-OS 9.1
1 -
Panorama
7 -
Panorama 8.1
1 -
Panorama 9.1
1 -
Panorama Configuration
2 -
Panorama HA
1 -
PBF
1 -
PCNSA
2 -
PCNSE
2 -
policies
2 -
policy
3 -
Policy Based Forwarding
1 -
Prisma
1 -
Prisma Access
5 -
Prisma SD-WAN
1 -
QRadar
1 -
Radius
1 -
Ransomware
1 -
region
1 -
Registration
1 -
Release Notes
1 -
reporting and logging
1 -
Routing
1 -
SAML
1 -
SASE
2 -
script
2 -
SD WAN
1 -
SD-WAN
1 -
SDWAN
1 -
Search
1 -
Security Advisory
1 -
Security automation
1 -
security policy
4 -
security profile
1 -
Security Profiles
2 -
Session Packet
1 -
Setup & Administration
7 -
Site-to-Site VPN
1 -
Split Tunneling
1 -
SSL
1 -
SSL Decryption
2 -
SSL Forward Proxy
1 -
SSO
1 -
Strata Logging Service
2 -
Support Guidance
1 -
syslog
1 -
Tag
2 -
Tags
2 -
Terraform
2 -
TGW
3 -
threat log
1 -
threat prevention
2 -
Threat Prevention License
1 -
Threat Prevention Services
1 -
Tips & Tricks
2 -
tls
1 -
traffic_log
1 -
Transit Gateway
1 -
Traps
1 -
Troubleshoot
2 -
Troubleshoot. logs
1 -
Troubleshooting
5 -
tunnel
1 -
Tutorial
2 -
Ubuntu 16.04
1 -
Unified Monitoring
1 -
upgrade
2 -
upgrade-downgrade
3 -
url categories
1 -
URL Filtering
2 -
URL-Filtering
1 -
User ID Probing
1 -
User-ID
1 -
User-ID & Authentication
1 -
User-ID mapping
1 -
userid
1 -
VM Series
1 -
VM-Series
15 -
VM-Series on AWS
6 -
VM-Series on GCP
2 -
VPC Flow logs
1 -
VPN
2 -
VPNs
4 -
Vulnerability Protection
1 -
Webinar
1 -
WildFire
3 -
Wildfire License
1 -
wmi
1 -
XDR
1 -
xml
2 -
XML API
2
- Previous
- Next





