- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Disable Protection Rule for Remote Initiated Behavioral Threat
- LIVEcommunity
- Discussions
- Security Operations
- Cortex XDR Discussions
- Disable Protection Rule for Remote Initiated Behavioral Threat
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Disable Protection Rule for Remote Initiated Behavioral Threat
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-22-2024 02:08 PM - edited 02-22-2024 02:12 PM
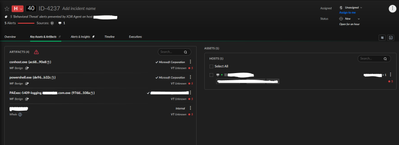
We are creating a custom service to handle automatically checking and updating programs (similar to PDQ Deploy, or an RMM tool).
We've signed the the created service and tried several ways to disable it from being blocked. The problem is, we are very limited in what we can target with the disable prevention rules.
Has anyone run into this and actually allowed it through. We could change the commands to not trigger the alerts as we can see what triggered them by getting the alert data.
The point is that if we signed what is running, we'd like to be able to build it out without worrying about coding around XDR's every changing (and hard to extract behavioral rules).
We've already attempted to:
- allow our signature in a disable prevention rule
- allow the ending powershell process with a wildcard cmd line argument
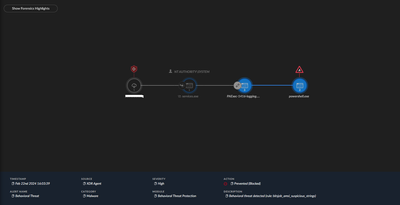
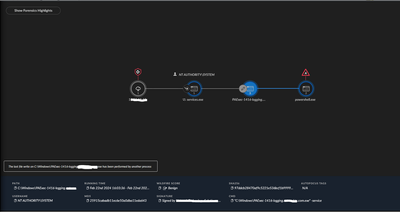
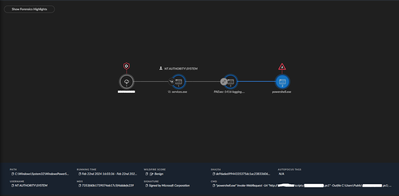
The problem seems to be that the point where the block is triggered happens before the signer is considered. The artifacts show our service as being signed.
Screenshot of causality chain nodes below.
Disable Prevention Rules does not give us any way to address this.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-23-2024 05:11 AM
Hi @CJNTS, thanks for reaching us using the Live Community.
Is the powershell script located in a specific folder?
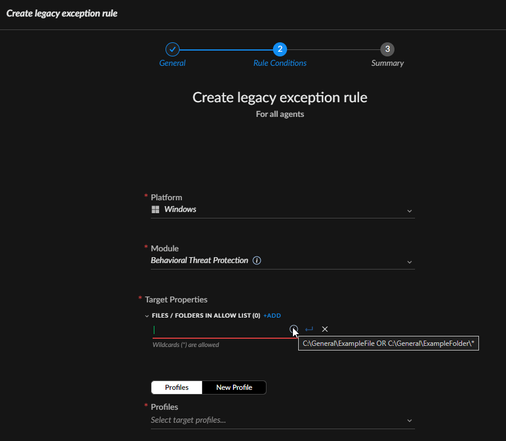
Have you tried with a Legacy Agent Exception for the Behavioral Threat Prevention module which is the one blocking here?
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-23-2024 05:38 AM - edited 02-23-2024 05:38 AM
We've looked into that, but don't want to take that route.
As we build things out, different scripts will run from the same folder structure. To create this rule, we'd have to make a bunch of exceptions for each file path, or wild card the last piece (script name).
From what I've looked at if we did it this way we wouldn't be able to also evaluate the signer. I think this may work, but it would be creating a bigger hole in protection than we're aiming for.
If I'm wrong on any of that, please let me know. We really want to evaluate based on the signer. If we could consider a wildcard file path AND the signer, this would be a consideration.
- 523 Views
- 2 replies
- 4 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Does Cortex XDR BIOC analytics alerts get blocked after setting Global Behavioral Threat Protection to block in Cortex XDR Discussions
- Documentation for Advanced API Monitoring in Cortex XDR Discussions
- XQL query to add a widget to know the Protection Paused more than 30 days. in Cortex XDR Discussions
- Global Exceptions in Cortex XDR Discussions