- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Automate Reported Phishing Email Attachments to CrowdStrike Falcon Sandbox w/ XSOAR
- LIVEcommunity
- Discussions
- Security Operations
- Cortex XSOAR Discussions
- Automate Reported Phishing Email Attachments to CrowdStrike Falcon Sandbox w/ XSOAR
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Automate Reported Phishing Email Attachments to CrowdStrike Falcon Sandbox w/ XSOAR
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-22-2024 06:00 AM
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-22-2024 07:14 AM
Hello,
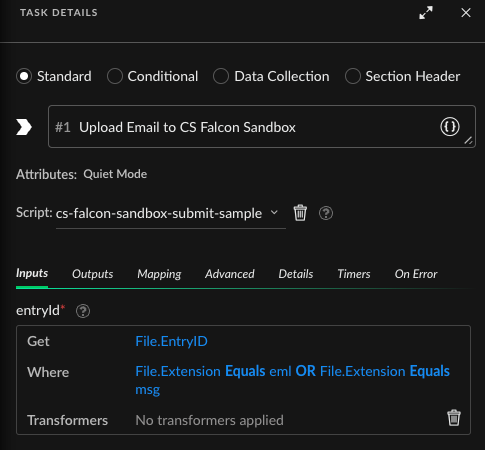
When an XSOAR integration which fetches emails returns back with an email, the resulting incident will be populated with not only the content of the email, but also an entry called "File" that relates to the email itself. The data in this path may include further files that were attached to the email. You can identify which file entry is the email by looking at the extensions path ${File.extension}. From here, you can create a playbook that will call the Crowdstrike Falcon Sandbox command "cs-falcon-sandbox-submit-sample",
This command will ask for a file to submit. The input may be called "entry-id" or similar. This is expecting the entry-id of the file. The entry ID is an id that references an entry within the war room starting from 1@<incidentid>. This value is also referenced within the File entry in Context Data.
So your call to cs-falcon-sandbox-submit-sample may look like this.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-22-2024 07:24 AM - edited 02-22-2024 07:30 AM
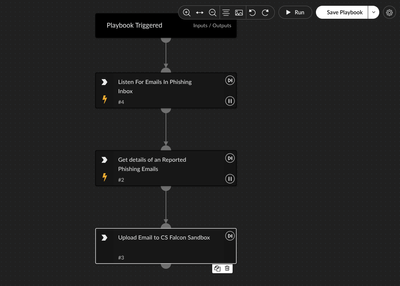
Hey! Thanks for getting back. So when I create a playbook do I need to create tasks such as listening for our phishing@company.com inbox, get details of the reported email (using the Abnormal Security Scripts)? Or would this be using the standard mail listener integration?then do the suggested Upload Email to CS Falcon Sandbox task?
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-22-2024 07:40 AM
Typically a Phishing XSOAR incident would have been created from the emails fetched by an integration where each email is its own investigation/incident. An integration such as O365 or any other email fetching integration would attach each incident with the email that it fetched in. This is the scenario that I approached this question from. If you are not approaching phishing in this way, you will need to run the appropriate commands to fetch the email you'd like to send off to CS Falcon Sandbox.
You will first need to identify which command will execute the query for the email, and ensure that it is working as expected. I suggest running the command within the Playground until you are confident in the inputs necessary for your desired query. The command you choose must return an email in a format that is accepted by CS Falcon.
Once you can see the correct file populated in the Context Data of the Playground, you can then manually calling the CS Falcon Sandbox command to submit said email. This will allow you to make changes to the command until you feel like you've understood the format of the inputs necessary.
Make sure to call !DeleteContext all=yes every so often to clear out Context Data of your Playground as pulling email files during testing will crowd the CD with data you may no longer need.
Once you've identified the order of operations for your commands, you can then transfer them to your playbook.
I cannot speak to how you would specifically fetch in email files, and I am not familiar with your environment, but it looks like you are already doing so from your screenshot. The output of that command should create a new entry within ${File} for you to use in the CS Falcon command.
- 559 Views
- 3 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!