- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Enabling SSO JIT with Microsoft Entra ID (formerly known as Azure Active Directory)
- LIVEcommunity
- Products
- Cloud Native Application Protection
- Prisma Cloud
- Prisma Cloud Articles
- Enabling SSO JIT with Microsoft Entra ID (formerly known as Azure Active Directory)
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Printer Friendly Page
By Irene Garcia, Senior Customer Success Engineer
and
Srikanth Makineni, Customer Success Engineer
Overview
This document provides guidance on how to configure Single Sign On (SSO) between Prisma Cloud Enterprise and Microsoft Entra ID (formally known as Azure Active Directory, or Azure AD) to use Just-in-Time (JIT) provisioning to automatically create users in Prisma Cloud based on their AD Groups assignment.
Steps
- Prisma Cloud Prerequisites (Enabling Direct User Authentication)
- Set up Microsoft Entra ID SSO on Prisma Cloud
- Set up Just-in-Time Provisioning on Microsoft Entra ID
1. Prisma Cloud Prerequisites (Enabling Direct User Authentication)
In Prisma Cloud, go to Settings > Access Control > SSO.
In the section “Direct User Authentication” and select at least one user, who will be able to log in with local credentials in case there is an issue with SSO.
Please Note: If you do not complete this step and SSO does not work, you will need to raise a support case to get SSO disabled in order to log back into the tenant.
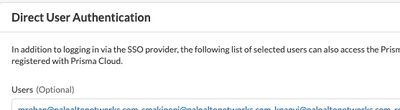
Figure 1: Direct User Authentication_palo-alto-networks
2. Set up Microsoft Entra ID SSO on Prisma Cloud
In Azure:
- Log in to Azure, search/browse to “Microsoft Entra ID”, and click “Enterprise applications”.
- Click “+ New application”.
- Once the application is created, go to the “Single sign-on” page and select “SAML”.
- Scroll down to Step 4 and copy the “Microsoft Entra identifier”.
In Prisma Cloud:
5. Go to “Settings > Access Control > SSO” and select “SAML” protocol and click on “Enabled”:
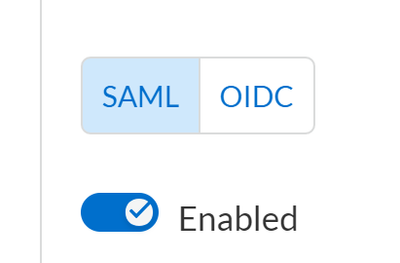
Figure 2: Enable SAML protocol_palo-alto-networks
6. Paste the previous copied URL into the “Identity Provider Issuer” field.
7. Copy the “Audience URI (SP Entity ID)”.
In Azure:
8. In Step 1 (“Basic SAML Configuration”), click “edit” and paste that value in the “Identifier (Entity ID)” field.
9. The “Reply URL (Assertion Consumer Service URL)” field will depend on the location of your tenant, which is displayed in the login URL. You will need to replace “app” with “api” and append “/saml” at the end. For example, for the following login URL:
https://app2.eu.prismacloud.io
The value for this field will be:
https://api2.eu.prismacloud.io/saml
10. In Step 3 (“SAML Signing Certificate”), click “Add a certificate” and then “New Certificate”. Enter an expiration date
and notification email address and click “Save”.
11. Go back to step 3 and download the “Certificate (Base64)”.
In Prisma Cloud:
12. Paste the certificate value (including the “BEGIN” and “END” lines) in the “Certificate” section:
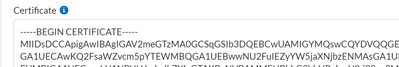
Figure 3: Certificate field_palo-alto-networks
13. Before clicking on “Save”, please validate the following prerequisites are in place:
- In Prisma Cloud, you have at least one user under the “Direct User Authentication” section (just in case the SSO integration does not work)
- The user used for the SSO test:
- Exists in Prisma Cloud under “Settings > Access Control > Users”
- Has an assigned role in Prisma Cloud
- Is assigned to the Microsoft Entra enterprise application in the “Users and Groups” section (either directly or by being a member of an assigned group)
- Click “Save” and test the SSO integration.
3. Set up Just-in-Time Provisioning on Microsoft Entra ID
Once the SSO integration is working, we can proceed to enable JIT. The idea is to automate the process of creating accounts for users. In other words, the user will not be required to be in the “Settings > Access Control > Users” list, instead, it will automatically be added to that list with a role automatically assigned.
The most important part of JIT settings are the values sent as a part of the SAML assertion. Prisma Cloud requires the following fields:
- Email Address
- Role
- First Name
- Last Name
By default, the Microsoft Entra enterprise application previously created will already have three fields: email address, first name, and last name. On the other hand, we will create a new attribute for the “role” field. In that case, the value sent from Azure has to map to an existing role in Prisma Cloud. If any of the required attributes don’t exist, the JIT SSO login will fail.
In Azure:
- Go to the SSO Enterprise Application that you configured in the previous section. Click on “Single sign-on” and on “Edit” in the section 2: “User Attributes & Claims”
- Click on “Add a group claim”:
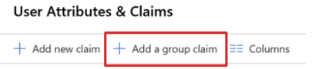
Figure 4: Add a group claim_palo-alto-networks
- Select “Groups assigned to the application”, “sAMAccountName” as “Source attribute”
and customize the name of the group claim:
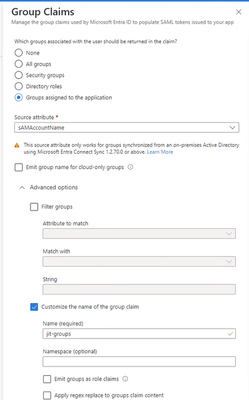
Figure 5: Group claim configuration_palo-alto-networks
After that, the “Attributes & claims” view should look like this:
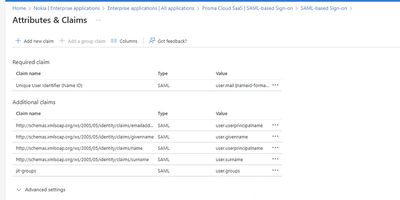
Figure 6: Attributes & Claims configuration_palo-alto-networks
In Prisma Cloud:
- Go to “Settings > Access Control > SSO” and click on “Enabled” in the “Just in Time (JIT) Provisioning” section.
- Update the fields with the corresponding Microsoft Entra ID claim names. With the previous Microsoft Entra ID “Attributes & Claims” view, the Prisma Cloud configuration should look like this:
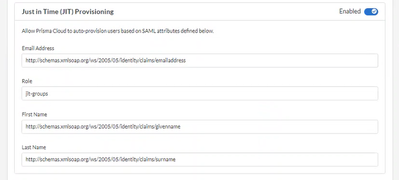
Figure 7: Prisma Cloud JIT configuration_palo-alto-networks
- Click on “Save”.
- Go to “Settings > Access Control > Roles” and create as many roles as desired. The role names should exactly match the Microsoft Entra ID group names assigned to the Microsoft Entra enterprise application.
- Before testing the JIT integration, please validate the following prerequisites are in place:
- The user used for the SSO JIT test:
- Does not exist in Prisma Cloud under “Settings > Access Control > Users” (just to confirm that it is automatically added to the list after a successful JIT test).
- Is a member of at least one of the Microsoft Entra ID groups assigned to the Microsoft Entra enterprise application.
- The same groups you have in Microsoft Entra ID also exist with the exact same name in Prisma Cloud as roles. This configuration relies on assigning a role called exactly the same way as the attribute coming in the SAML response. For example, the roles could have these names in Prisma Cloud:
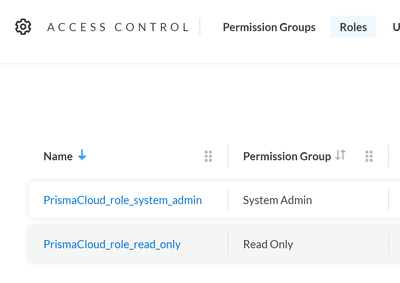
Figure 8: Prisma Cloud Roles_palo-alto-networks
And in that case, the Groups assigned to the Microsoft Entra enterprise application must have the same names:
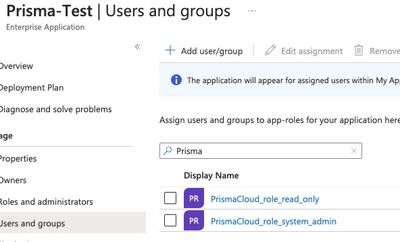
Figure 9: Microsoft Entra enterprise application Users and Groups_palo-alto-networks
With this configuration, whenever a user is a member of one or multiple Microsoft Entra ID groups whose name is a Prisma Cloud role, the user will have that role(s) assigned.
Once the configuration is working, you will need to do the following in case you would like to have more roles assigned to users. Let's say you would like user "XX" to have the role "YY":
- In Azure, validate the user "XX" is a member of the group "YY"
- In Azure, in the Prisma Cloud Enterprise Application, assign the group "YY" in the section "Users and groups"
- In Prisma Cloud, create a role with the name "YY"
Conclusion
Enabling and controlling access to IT resources and applications is an important aspect of securing an organization. An identity provider such as Microsoft Entra ID is used by many organizations, and this article has given you the required information to connect Prisma Cloud with users and roles defined in Microsoft Entra ID by the following three steps:
- Enable Direct User Authentication in Prisma Cloud
- Setup Microsoft Entra SSO on Prisma Cloud
- Microsoft Entra SSO Group Claims Setup Just-in-time Provisioning on Microsoft Entra ID
This then allows users to be automatically created in Prisma Cloud when the user gets access to Prisma Cloud using Microsoft Entra SSO. The user’s role and permissions will be based on the Microsoft Entra Groups assignment. No manual creation of users will be required for your organization’s users to log into Prisma Cloud. As long as the Microsoft Entra ID provides the user with the permissions to access Prisma Cloud, the user will be able to log in with the appropriate credentials with access levels as configured in Microsoft Entra ID.
Reference
Set up Azure AD SSO on Prisma Cloud
About the Authors
- 1834 Views
- 0 comments
- 0 Likes
-
Access Control
1 -
Active Directory Groups
1 -
Agentless
1 -
Agentless VM Scanning
2 -
Approach
1 -
Asset inventory
1 -
Assets
1 -
Authentication
1 -
Authorization
1 -
Auto Map
2 -
auto-remediation
2 -
AWS
1 -
AWS Account Onboarding
1 -
AWS Secrets Manager
1 -
Azure
1 -
Azure Cloud Accounts
2 -
Azure RBAC
1 -
Azure Single Sign On (SSO)
1 -
Beginner to Intermediate Level
5 -
CLI command
2 -
Cloud Security
12 -
Cloud Security Posture Management
1 -
Cloud Security Posture Management (CSPM)
7 -
Cloud Workload Protection
1 -
Cloud Workload Protection Platform (CWPP)
2 -
Collection Scoping
1 -
compliance scanning
1 -
Compute
1 -
Compute Edition
5 -
Compute SaaS
2 -
Configuration
2 -
Containers
1 -
CSPM
2 -
CVE
1 -
CWP Token
1 -
CWPP
2 -
DaemonSet
1 -
Defender Deployment
2 -
docker swarm
1 -
GCP Organization Onboarding
2 -
General Articles
3 -
GitOps
1 -
host vulnerabilities
1 -
Hosts
1 -
IAC
1 -
IAM
1 -
Identity federation.
1 -
Ingress
1 -
Intermediate Skill Level
1 -
JIT
1 -
JWT Token
1 -
Kubernetes
3 -
Kubernetes Clusters
1 -
Least Privilege
1 -
Least privilege Principle
1 -
Log4j
1 -
MFA (Multi-Factor Authentication)
1 -
Microsoft Azure subscriptions
1 -
Microsoft Entra.
1 -
Nested Account Groups
1 -
Nested Account Groups.
1 -
NGINX
1 -
onboarding
1 -
Organizing Cloud Resources
1 -
PAM (Privileged Access Management)
1 -
PCEE
2 -
playbooks
2 -
prioritize risk
4 -
Prisma "cloud code security" (CCS) module
1 -
Prisma Cloud
6 -
Prisma Cloud Code Security
1 -
Prisma Cloud Compute
3 -
Prisma Cloud Compute Edition
6 -
Prisma Cloud Compute Edition Administrator’s Guide
1 -
Prisma Cloud Enterprise Edition
3 -
Prisma Cloud Intelligence Stream(IS)
2 -
Prisma Cloud Intelligence Stream(IS) feed
2 -
Prisma Cloud Presentations
1 -
Prisma Cloud SaaS API
1 -
Prisma Cloud Terraform Provider
1 -
Radar
1 -
RBAC (Role-Based Access Control)
1 -
Recursive Hierarchy
2 -
reference “Prisma Cloud Administrator’s Guide”
1 -
reference “Prisma Cloud Compute Edition Administrator’s Guide”
2 -
RQL
1 -
Runtime Security
2 -
Secrets
1 -
Security Posture
1 -
Serverless
1 -
Service Account
1 -
SSO (Single Sign-On)
1 -
Terraform
1 -
thread feed
4 -
threat intelligence
4 -
Visibility
1 -
VM Scanning
1 -
vulnerability detection
6 -
Vulnerability management
5 -
WAAS
1 -
XSOAR
2
- Previous
- Next




