- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Leveraging Prisma Cloud to Enforce Least Privilege
- LIVEcommunity
- Products
- Cloud Native Application Protection
- Prisma Cloud
- Prisma Cloud Articles
- Leveraging Prisma Cloud to Enforce Least Privilege
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
on 02-29-2024 11:23 AM
By Bishvesh Pachauli, Customer Success Engineer
and
Paul Burega, CSE Team Lead
Introduction
Identity and Access Management (IAM) refers to the processes and tools for managing user access to resources and enforcing security policies. IAM is crucial for securing the modern enterprise as it enables organizations to control who can access what resources. By enforcing strong IAM policies, companies can enforce the principle of least privilege, meaning users and resources are only granted minimum permissions necessary to perform their jobs. This minimizes the horizontal scaling of security attacks in the event of compromised credentials.
Prisma Cloud offers capabilities to embed IAM into the software delivery lifecycle. It can scan infrastructure-as-code for misconfigurations and enforce least privilege during deployment. Additionally, Prisma Cloud can monitor permissions at runtime and alert on anomalies that indicate privilege creep or excessive permissions. By leveraging the CIEM module within Prisma Cloud, organizations can confidently monitor access while minimizing risk.
This article will provide RQLs to create sample policies based on IAM requirements, as well as demonstrate how a simple IAM RQL can be continually extended to add additional IAM functionality.
Cloud Infrastructure Entitlement Management (CIEM)
Entitlement Management is managing identities and privileges. Security teams want to enforce the principle of least-privileged access to cloud infrastructure and resources. Reducing the attack surface and mitigating access risks posed by excessive permissions help to secure the user’s cloud environment.
The Three Pillars of Prisma Cloud’s CIEM Module
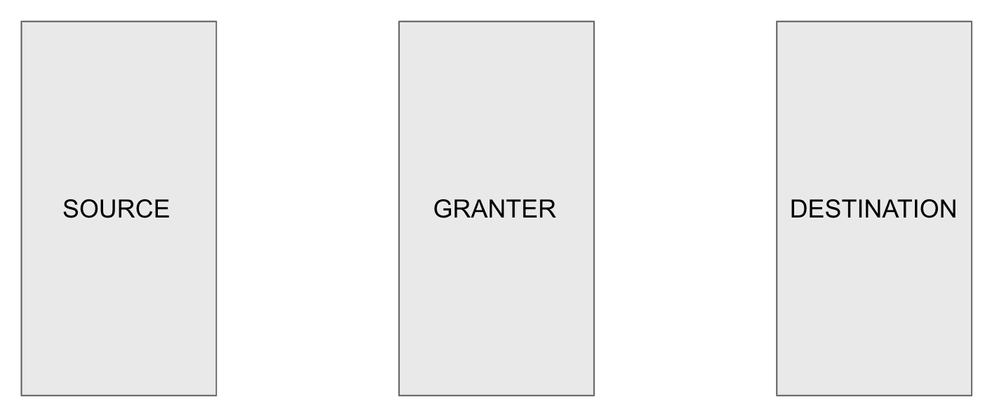
Figure 1: Three Pillars of CIEM Module_palo-alto-networks
- Source is an Identity with permissions to interact with various cloud resources, which can encompass entities like IAM users, Azure Active Directory users, EC2 instances, Lambda functions, and Azure virtual machines.
- Destination is any cloud resource on which an action has occurred or is the target of the action.
- Granter is the group, role, or policy that grants permissions to the source to interact with the destination.
IAM Policy Attributes
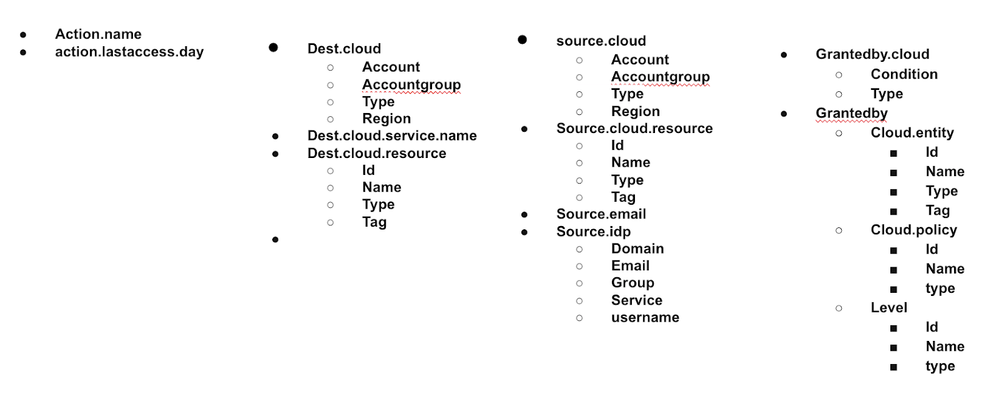
Figure 2: IAM Policy attributes as defined in reference [1]_palo-alto-networks
Approach for Writing IAM Policies
Let's begin by writing an RQL to find permissions of all IAM users:
config from iam where source.cloud.service.name = 'iam' and source.cloud.resource.type = 'user'
Let’s modify the use case to find a list of users who are inactive for more than 90 days:
config from iam where source.cloud.service.name = 'iam' and source.cloud.resource.type = 'user' AND action.lastaccess.days > 90
To find users that can take action on a particular service such as EC2:
config from iam where source.cloud.service.name = 'iam' and source.cloud.resource.type = 'user' AND dest.cloud.type = 'AWS' AND dest.cloud.service.name = 'ec2'
By adding the requirements to find all users that can terminate instances and create NACL groups, we add that to the end of the previous RQL to get:
config from iam where source.cloud.service.name = 'iam' and source.cloud.resource.type = 'user' AND dest.cloud.type = 'AWS' AND dest.cloud.service.name = 'ec2' AND action.name IN ( 'ec2:CreateNetworkAcl', 'ec2:TerminateInstances' )
And to see if this user has unrestricted access to all resources in a particular cloud account, we again add to the end of the previous RQL:
config from iam where source.cloud.service.name = 'iam' and source.cloud.resource.type = 'user' AND dest.cloud.type = 'AWS' AND dest.cloud.service.name = 'ec2' AND action.name IN ( 'ec2:CreateNetworkAcl', 'ec2:TerminateInstances' ) AND dest.cloud.wildcardscope = true and dest.cloud.account = ‘ABC-123’
As we can see from the above example, we started off with a very basic query and built a complex query around it. Further in this article, we will share some common use cases to build your IAM policies around.
Common Use Cases
- Find overly permissive roles that are tied to any IAM resource:
config from iam where source.cloud.service.name = 'iam' AND grantedby.cloud.entity.type = 'role' AND dest.cloud.wildcardscope = true AND dest.cloud.service.name = 'ec2'
This query finds all roles tied to IAM resources that provide access to all ec2 resources. - Find overly permissive users:
config from iam where source.cloud.service.name = 'iam' AND grantedby.cloud.entity.type = 'user' AND dest.cloud.wildcardscope = true - Find users that have inline policy attached to them that are overly permissive:
config from iam where source.cloud.resource.type = 'user' AND grantedby.cloud.policy.type = 'Inline Policy' AND dest.cloud.wildcardscope = true - Find users that have inline policy which allows them to assume roles:
config from iam where source.cloud.resource.type = 'user' AND action.name in( 'sts:AssumeRole', 'sts:AssumeRoleWithSAML', 'sts:AssumeRoleWithWebIdentity' ) AND dest.cloud.resource.type = 'role' AND dest.cloud.wildcardscope = true - Find all IAM identities that can terminate ec2 instances as well as delete s3 buckets that has sensitive data and have done so in the last 7 days:
config from iam where source.cloud.service.name = 'iam' AND action.name in ( 'ec2:TerminateInstances', 's3:DeleteBucket' ) AND action.lastaccess.days <= 7 AND dest.cloud.resource.tag ( 'data_type' ) = 'sensitive' - Find inactive IAM users who haven’t accessed the environment in the last 180 days:
config from iam where source.cloud.resource.type = 'User' AND action.lastaccess.days > 180
7. Find policies that allow to encrypt and decrypt kms keys without any conditions:
config from iam where grantedby.cloud.policy.condition ( 'aws:SourceArn' ) exists AND action.name IN
('kms:Decrypt', 'kms:Encrypt' )
8. Find all Okta identities that can assume roles:
config from iam where action.name IN ( 'sts:AssumeRole', 'sts:AssumeRoleWithSAML', 'sts:AssumeRoleWithWebIdentity' ) AND source.idp.service = 'Okta'
Graph Visualization
The IAM graph view provides a visual representation of the connections between various entities which help you understand the relationships among source entities; those granting access, and the destinations or resources being accessed.
This visualization aids in answering critical questions, such as identifying who has access to specific resources and how that access was initially granted. Graph visualization is an excellent way to create IAM queries on the go by simply clicking the desired component and the query completes automatically. As you modify these connections visually, the corresponding Relationship Query Language (RQL) statements are automatically updated in the background.
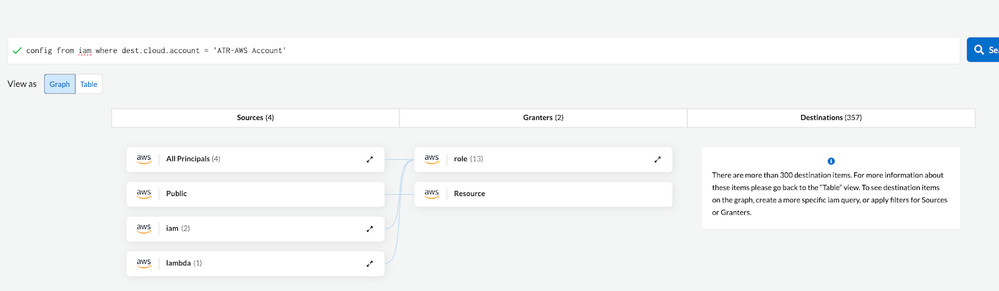
Figure 3: Graph visualization snippet from Prisma cloud_palo-alto-networks
This is only supported for source, granters and cases in which destinations are less than 300.
Least Privilege Access Enforcement
The asset inventory page shows the IAM relationships of the cloud resources when the IAM module is enabled. You can also remediate overly permissive roles and groups:
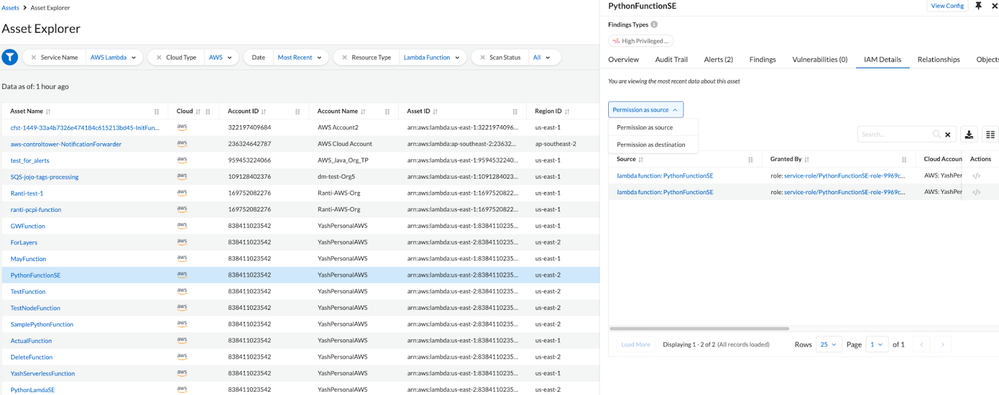
Figure 4: IAM details tab in the asset inventory view_palo-alto-networks
(In the image above, we can see what IAM identities can take action on this lambda function “PythonFunctionSE”. Switching to Permission as Destination, tells what actions on all resources this Lambda function can perform.)
You can also view policies as to which resources, groups and roles a policy is attached to along with permissions.
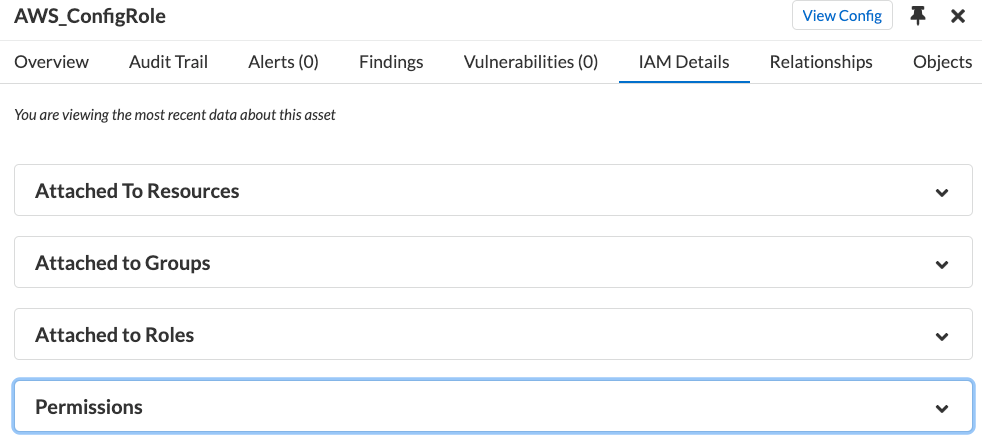
Figure 5: Different IAM attributes for a particular cloud resource as seen in the asset inventory view_palo-alto-networks
The least privilege wizard goes a step further and analyzes unused permissions and generates files as needed.
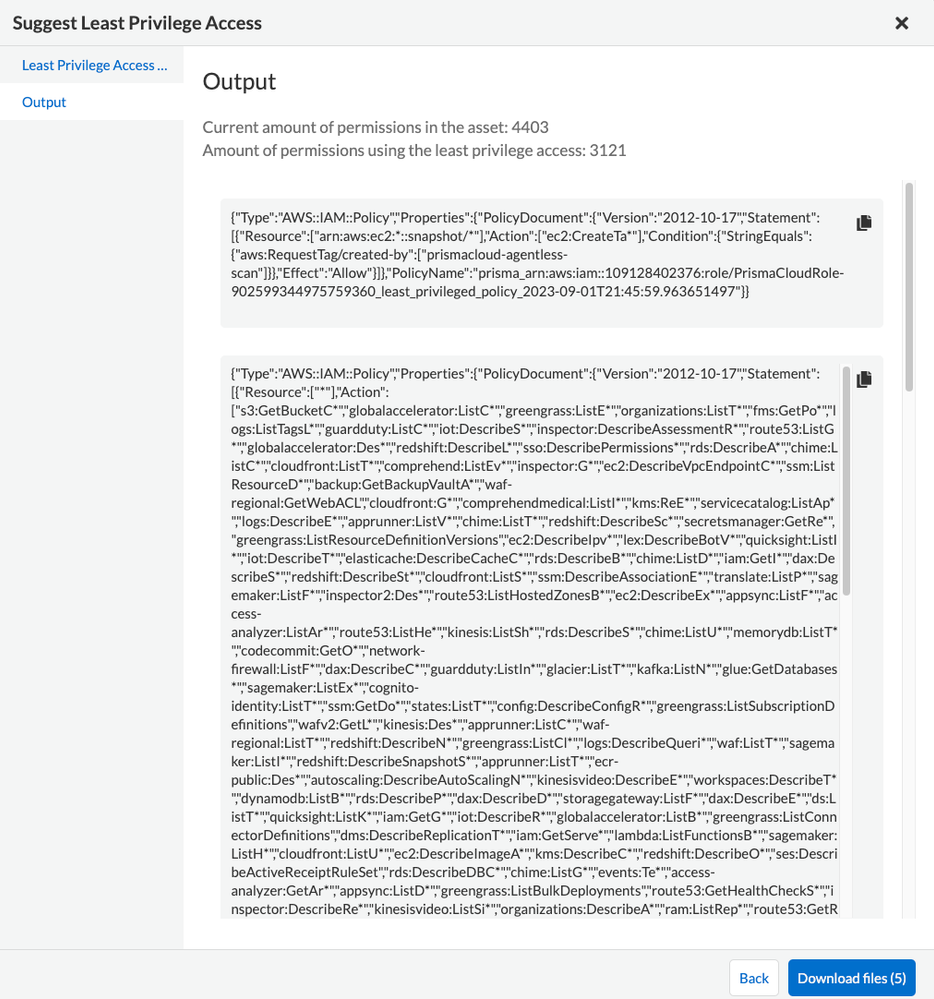
Figure 6: Least privilege recommendation by Prisma cloud for an overly permissive role_palo-alto-networks
Conclusion
Identity and Access Management (IAM) is a fundamental component of security and operational efficiency in today's digital world. IAM establishes a critical framework to safeguard sensitive data, applications, and resources by ensuring only authorized users and systems can access them.
Least privilege using IAM minimizes security risks: data breaches; unauthorized changes; and insider threats. IAM streamlines workflows by granting appropriate access to users when needed, improving productivity and compliance.
The importance of IAM lies in its ability to protect organizations against evolving cyberthreats, enhancing operational effectiveness, and building trust among users and stakeholders. IAM's capacity to secure organizations, enable efficient operations, and foster trust makes it an essential pillar of modern digital security and workflow management.
This article has shown examples of simple through complex IAM RQLs which can implement IAM policies in your organization. By simply changing one parameter, the RQL can determine IAM policies for different users, cloud objects or actions.
Reference
[1] Prisma™ Cloud Resource Query Language (RQL) Reference, IAM Query Attributes
[2] Prisma™ Cloud Resource Query Language (RQL) Reference, IAM Query Examples
[3] Prisma™ Cloud Resource Query Language (RQL) Reference, IAM Query Conditions
About the Authors
Bishvesh Pachauli is a Customer Success Engineer and Paul Burega is a CSE Team Lead. Paul and Bishvesh utilize a collaborative approach to break down complex problems into solutions for global enterprise customers and leverage their multi-industry knowledge to inspire success.
- 969 Views
- 0 comments
- 2 Likes
-
Access Control
1 -
Active Directory Groups
1 -
Agentless
1 -
Agentless VM Scanning
2 -
Approach
1 -
Asset inventory
1 -
Assets
1 -
Authentication
1 -
Authorization
1 -
Auto Map
2 -
auto-remediation
2 -
AWS
1 -
AWS Account Onboarding
1 -
AWS Secrets Manager
1 -
Azure
1 -
Azure Cloud Accounts
2 -
Azure RBAC
1 -
Azure Single Sign On (SSO)
1 -
Beginner to Intermediate Level
5 -
CLI command
2 -
Cloud Security
12 -
Cloud Security Posture Management
1 -
Cloud Security Posture Management (CSPM)
7 -
Cloud Workload Protection
1 -
Cloud Workload Protection Platform (CWPP)
2 -
Collection Scoping
1 -
compliance scanning
1 -
Compute
1 -
Compute Edition
5 -
Compute SaaS
2 -
Configuration
2 -
Containers
1 -
CSPM
2 -
CVE
1 -
CWP Token
1 -
CWPP
2 -
DaemonSet
1 -
Defender Deployment
2 -
docker swarm
1 -
GCP Organization Onboarding
2 -
General Articles
3 -
GitOps
1 -
host vulnerabilities
1 -
Hosts
1 -
IAC
1 -
IAM
1 -
Identity federation.
1 -
Ingress
1 -
Intermediate Skill Level
1 -
JIT
1 -
JWT Token
1 -
Kubernetes
3 -
Kubernetes Clusters
1 -
Least Privilege
1 -
Least privilege Principle
1 -
Log4j
1 -
MFA (Multi-Factor Authentication)
1 -
Microsoft Azure subscriptions
1 -
Microsoft Entra.
1 -
Nested Account Groups
1 -
Nested Account Groups.
1 -
NGINX
1 -
onboarding
1 -
Organizing Cloud Resources
1 -
PAM (Privileged Access Management)
1 -
PCEE
2 -
playbooks
2 -
prioritize risk
4 -
Prisma "cloud code security" (CCS) module
1 -
Prisma Cloud
6 -
Prisma Cloud Code Security
1 -
Prisma Cloud Compute
3 -
Prisma Cloud Compute Edition
6 -
Prisma Cloud Compute Edition Administrator’s Guide
1 -
Prisma Cloud Enterprise Edition
3 -
Prisma Cloud Intelligence Stream(IS)
2 -
Prisma Cloud Intelligence Stream(IS) feed
2 -
Prisma Cloud Presentations
1 -
Prisma Cloud SaaS API
1 -
Prisma Cloud Terraform Provider
1 -
Radar
1 -
RBAC (Role-Based Access Control)
1 -
Recursive Hierarchy
2 -
reference “Prisma Cloud Administrator’s Guide”
1 -
reference “Prisma Cloud Compute Edition Administrator’s Guide”
2 -
RQL
1 -
Runtime Security
2 -
Secrets
1 -
Security Posture
1 -
Serverless
1 -
Service Account
1 -
SSO (Single Sign-On)
1 -
Terraform
1 -
thread feed
4 -
threat intelligence
4 -
Visibility
1 -
VM Scanning
1 -
vulnerability detection
6 -
Vulnerability management
5 -
WAAS
1 -
XSOAR
2
- Previous
- Next




