- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Cortex XDR Auto Quarantine
- LIVEcommunity
- Discussions
- Security Operations
- Cortex XDR Discussions
- Cortex XDR Auto Quarantine
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Cortex XDR Auto Quarantine
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-12-2023 11:10 AM
Hey all,
Does anyone have experience with turning auto quarantine on?
I don't see much documentation on it but I'm assuming its as simple as quarantining the files associated with Wildfire verdicts.
We're looking to set up recurring malware scans on groups of assets at a time.
I know that when malicious files are found, they create alerts/incidents..
1 - If something is auto quarantined, are alerts/incidents still created?
2 - Has your experience with auto quarantine been mostly a positive experience?
Any insight would be appreciated.
Kind Regards,
Bojan
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-12-2023 07:40 PM - edited 10-12-2023 07:41 PM
Hi @Bojan-Totic ,
Thank you for writing to live community!
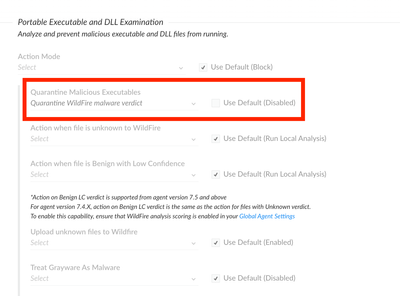
Cortex XDR malware profiles have quarantine options which dictates automatic quarantine on malicious activity detection. By default these are disabled and security admins can choose which module they need to enable the quarantine for. A classic and most widely used module is Portable executable and DLL examination where you get multiple options to choose to quarantine files based on Wildfire or Local analysis or both.
When the agent detects a malicious file and if the agent policy enforces a quarantine, the executable is automatically quarantined as part of malware scan or as a part of execution.
Screenshot attached. Hope this helps!
Please mark the response as "Accept as Solution" if it answers your query.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-18-2023 08:52 AM
Do you have internally deved apps?
Do you have code signing in place?
Have you excluded your signature from XDR Malware?
If you've answered yes to all 3 questions you are good to move forward or if you don't have any internally deved apps.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-13-2024 07:06 AM
When Quarantine is disabled, what sort of action does Cortex take with the detected "malware"? Does it delete it from the disk? Ignore it, or just blocks it from executing?
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-13-2024 08:12 PM
Hi @MosR ,
The fundamental principle of Cortex XDR is that it is an execution based detection and prevention solution. As a result the file if written to the disk if malicious stays on the system until executed or scanned. If the execution happens and quarantine is disabled, the execution, if malicious will still be blocked and you should have alerts as "Prevented(Blocked)". Alternatively, if the malicious file is scanned by the xdr agent as part of malware scans without quarantine enabled, it should alert as "Detected(Scanned)"
The unique distinguisher of any executable being quarantined or not, is what we can see from the causality view is the lock icon on the causality card depicting if the file is quarantined or not, but the execution action may still be prevented.
With the advent of Cortex XDR 3.9 and agent 8.3 and above, we also have on write file protection module which if enabled can also provide alerts on detections of disk write events(if quarantine is not enabled) and prevent and remove the file from the disk to the quarantine folder(if quarantine is enabled).
Hope this answers your query.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-14-2024 05:48 AM - edited 03-14-2024 05:50 AM
@neelrohit Thank you for the response, it certainly does. This topic is also covered in the following thread https://live.paloaltonetworks.com/t5/cortex-xdr-discussions/block-versus-quarantine-malware-module-s...
- 4246 Views
- 5 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Cortex XDR Tenant Auto-Upgrade 3.17 → 5.0: UI mixed theme, AI pages stuck loading, Marketplace/Playbook Catalog empty + ingestion quota warning in Cortex XDR Discussions
- Other Network Source Checkpoint,Fortinet Cortex can auto stich in Cortex XDR Discussions
- Quarantined File Automatically Moved to Allow List from Block List after File Restore Action in Cortex XDR Discussions
- Cortex XDR file quarantine in Cortex XDR Discussions
- Managing Updates (Content & Agent Upgrades) in Cortex XDR Discussions