- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Using custom URL categories
- LIVEcommunity
- Discussions
- General Topics
- Using custom URL categories
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Using custom URL categories
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-06-2019 06:21 AM
Hi guys,
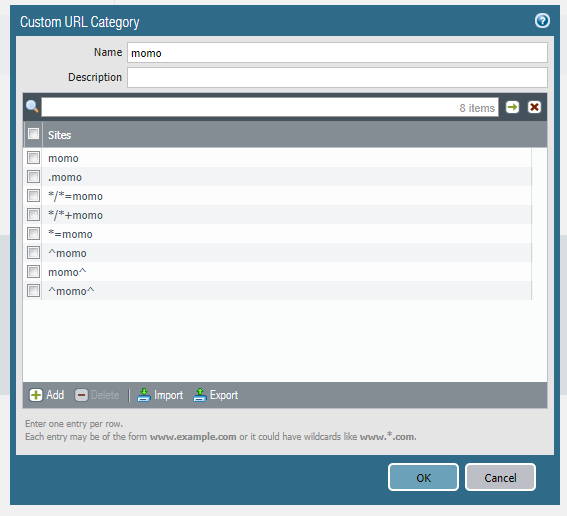
We're trying to stop users from accessing webpages featuring 'momo' content.
We've set up the below custom URL category and it only blocks Google searches for momo while in incognito mode, and still allows Google image and Youtube results. Is there anything wrong with this, we may have gone OTT trying to get this to work:
Using asterisks gives us errors.
Thanks,
J
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-06-2019 10:25 AM
You would be better off creating a custom threat signature for something like this instead of a URL category.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-07-2019 04:37 AM
I agree with @BPry , url filtering will limit your scope while a custom threat will be able to inspect payload etc
PANgurus - Strata & Prisma Access specialist
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-12-2019 03:11 AM
Thanks for the help. I've been looking into this and it certainly seems the right path.
I'm running into a brick wall at the moment though. My Regex's only work with limited effect, and once a search for the malicious term 'momo' has sucessfully established, my vulnerability protections no longer work. Could you please advise, I've listed them below.
A big part of the problem is that regex's have to be 7 bytes or larger without wildcard objects; so momo on it's own won't work.
Interestingly, one of my Regex's - momohoax|momo|momodanger|momowhatsapp|momochallenge|momo.|.momo|.momo. - context = http-req-message-body - will block me from working on the custom vulnerability object after it's been commited. This is a good thing, since it shows the protection is working on websites holding 'momo' content, but it is only working on the firewall config. I have set up the security profiles and policies correctly, and decryption is enabled.
Here's the regex's that have only limited scope:
Context: http-req-params - Value: search\?q=(.*momo\+.*)
Context: http-req-params - Value: search\?q=(.*.momo.*)
Context: http-req-params - Value: search\?q=(.*.momo*.*)\&source=.
Context: http-req-params - Value: .*(q=momo&rlz=).*
Context: http-req-params - Value: search_query=(.*.momo.*).*
Context: http-req-message-body Value: momohoax|momo|momodanger|momowhatsapp|momochallenge|momo.|.momo|.momo.
I know it's possible to create a condition that will block any webpage with momo on it, I'm just stumped as to how!
Thanks,
J
- 5159 Views
- 3 replies
- 1 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- New cert GP cert prompt for people testing Yubikeys for windows logon in GlobalProtect Discussions
- Address Group and Tag limitations in General Topics
- Custom BIOC Rule won't apply to Prevention Profile in Cortex XDR Discussions
- Playbook stuck after upgrade in Cortex XSOAR Discussions
- Cortex XDR Tenant Auto-Upgrade 3.17 → 5.0: UI mixed theme, AI pages stuck loading, Marketplace/Playbook Catalog empty + ingestion quota warning in Cortex XDR Discussions