- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Thread-Log: Virus found
- LIVEcommunity
- Discussions
- Cloud Delivered Security Services
- Threat & Vulnerability
- Re: Thread-Log: Virus found
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-08-2018 03:15 AM
Hello,
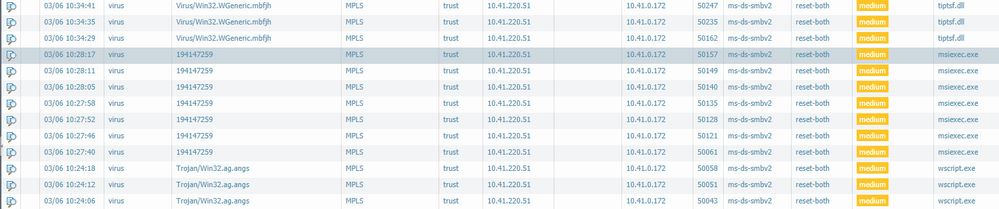
under our Threat-Log I found some Virus entries. The Attacker is an own PC from another vlan. We want to install windows updates over Ivanti-Patchmanagement with the original windows update service. And now the maschine, which we will patch, will do a virus attack - msiexec.exe and wscript.exe. Palo ID 194147259, Application ms-ds-smbv2...
We scanned both machines with a lot of tools and virus-scanner = nothing found!!!
Can somebody tell me the location of the infected files, which will shown in the thread log?
Have you some Tips for me?
Thank you verry much.
Cu
Wolfgang
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-20-2018 11:22 AM - edited 03-20-2018 11:24 AM
Thank you for the samples. The issue is resolved and the signatures will be removed from tomorrow's release of Antivirus. In the future please report these type of issues by opening a case with Support.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-08-2018 10:19 AM
To confirm this is on the firewall threat log? What was the action taken? If it droped or reset the session then traffic wouldn't have made it through to the host as it was blocked by the firewall.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-08-2018 03:19 PM
I found that multiple Palo Alto Networks customers have reported this issue.
After investigation, I've concluded these are caused by signature collisions with a signature for malicious sample 7e3bdff41913aadc0f5e1e0cf65a9197a060ad68bd9196d92ee240e0ab702085.
I've submitted a request to fine tune the associated signature, so that it is less likely to produce signature collisions.
The issue should be resolved by Monday COB.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-13-2018 04:23 AM
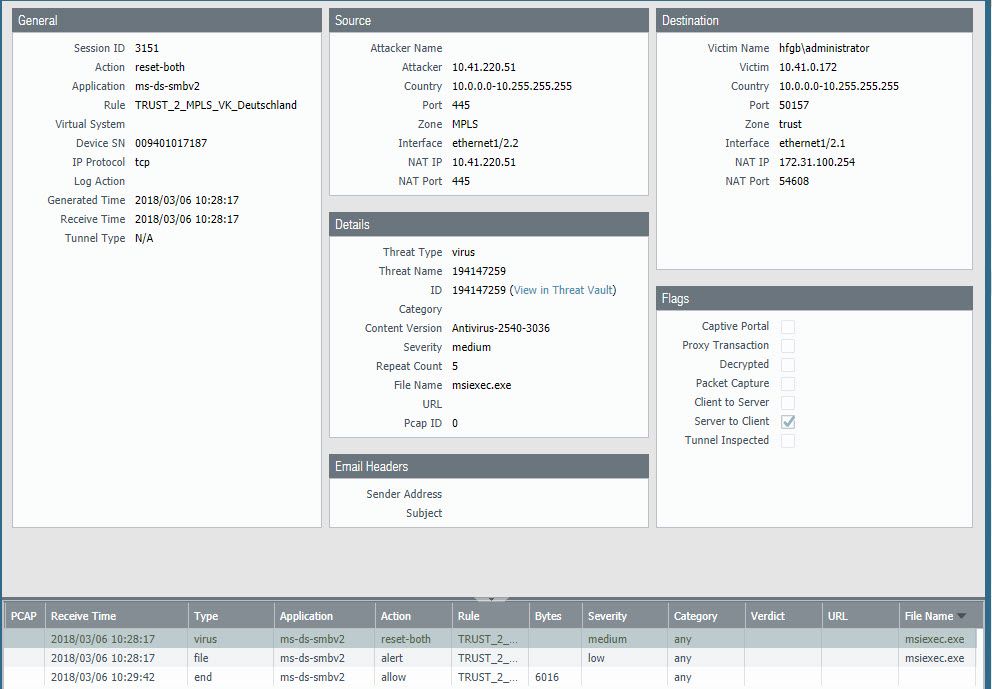
thanks for your responses 🙂
Did we talk about the same story?! How can I ensure that this virus message is a hoax or not?
At the top some Images about my virus troubles
How can I determine the directory of the affected file?
Thank you
Kind regards
Wolfgang
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-14-2018 03:38 PM
Wolfgang,
Please upgrade to the latest Antivirus package and do let me know if you still see the signature triggering.
I tried to resolved this issue, but the msiexec.exe sample I had to work with was not triggering the signature collision any longer.
If yours continues to trigger after updating Antivirus, please locate the msiexec.exe file that triggers the signature, and share its sha256 hash with me.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-16-2018 04:02 AM
Hi Mivaldi,
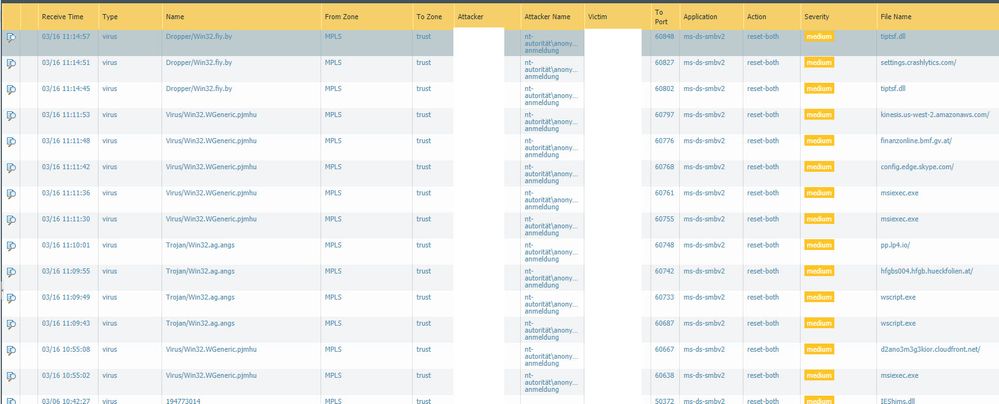
Take a look on my uploaded image, please.
I don't unterstand this....
For Explanation:
On the Victim Machine we scan the attacker with a patchmanagement software. No login on the attacker machine!
Why does the palo shows urls unter the file name?! We also scanned the victim machine with different anti virus software as TrendMicro and Kaspersky - nothing found!
I hope you have any ideas?
Thank you 🙂
cu
Wolfgang
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-16-2018 10:16 AM - edited 03-20-2018 11:25 AM
The URL's in the file names looks like a product defect. If I remember correctly, it is caused by limitations with the SMB decoder, which by the way has been significantly improved in PAN-OS 8.1. I would focus my attention on resolving the collision though. Have you been able to spot the msiexec.exe file causing the signature to trigger?
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-19-2018 12:40 AM
Hello Mivaldi,
I have uploaded the msiexe.exe and wscript.exe...
Thank you
cu
Wolfgang
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-20-2018 11:22 AM - edited 03-20-2018 11:24 AM
Thank you for the samples. The issue is resolved and the signatures will be removed from tomorrow's release of Antivirus. In the future please report these type of issues by opening a case with Support.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-20-2018 11:28 PM
Hello Mivaldi,
Thank you for your Support.
Can I assume that this was really a virus false report?
I will test the problem after Antivirus update oh the firewall and give you a Feedback!
Thanks 🙂
cu
Wolfgang
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-21-2018 02:54 PM
Wolfgang,
They weren't false positives. False positives are when WildFire gives a Benign file a Malicious verdict.
In this case, WildFire gave the files a Benign verdict, but they were triggering Antivirus signatures. We call these Signature Collisions. These happen when the digital patterns that the firewall looks at to identify a file, concide between a Benign sample and an Antivirus signature that has been generated from a Malicious sample that is similar in structure to the Benign file.
You can read more about these at:
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-26-2018 06:47 AM
Hi Mivaldi,
Your Changes was successfully 🙂
But can you check also this file: https://we.tl/cu2QR8Uxh2
I think, it's the same...
Thank you very much!
cu
Wolfgang
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-12-2018 11:41 PM
Hello Mivaldi,
I need your help once again...
Thank you
cu
Wolfgang
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-17-2018 09:49 AM
It was a virus false report caused by a Signature Collision.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-17-2018 09:50 AM
Wolfgang, for the new sample please open a case with support.
- 1 accepted solution
- 18971 Views
- 16 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Newsletter: Cloud Delivered Security Services, Oct-2025 in Advanced Threat Prevention Discussions
- critical control points in Advanced Threat Prevention Discussions
- most effective for protecting in Advanced Threat Prevention Discussions
- cortex-xdr-payload.exe access lsass.exe in Advanced Threat Prevention Discussions
- VLC update - "Virus" alert PA in Advanced Threat Prevention Discussions