- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Problem with PANOS UserID Agent and client probing using WMI.
- LIVEcommunity
- Community Legacy Content
- Automation / API
- Automation/API Discussions
- Problem with PANOS UserID Agent and client probing using WMI.
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Problem with PANOS UserID Agent and client probing using WMI.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-01-2013 03:44 AM
I am having some difficulty configuring our PAN environment to take advantage of the User-ID feature.
The current configuration is as follows:
- "Enable User Identification" has been selected on all zones where user identification is required
- A PAN200 device is configured as a User-ID Agent and redistribution point (only the Mgt interface is being used on this device)
- The receiving firewalls have been configured with the details of the PAN200 UID Agent
I can manually update the PAN200 with user / IP data using the vb scripts provided by PAN (nickp) and via the RESTful API and the data is distributed to the receiving firewalls. However, I would like to use the WMI client probing feature and was under the impression that if the receiving firewall doesn't have a mapping for a given IP address it would request the UID Agent to collect it on it's behalf. This doesn't seem to work. I have entered appropriate credentials within the WMI configuration page on the PAN200 and have enabled 'Client Probing'. I have run the command "wmic /node:remotecomputer computersystem get username" from my desktop with the credentials entered in the WMI section for a given remotecomputer and I get a result so I am confident the user permissions are correct.
Where have I gone wrong? What changes are necessary? Which logs should I investigate?
Any assistance would be welcome.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-01-2013 04:06 AM
How did you test wmi is not working ? what timeout values are you using for wmi and user identification ?
Dont forget that PaloAlto will send a probe to each learned IP address in its list to verify that the same user is still logged in when you use wmi.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-01-2013 04:23 AM
So, the probe interval is 20 mins and the user identification timeout value is 45 mins for WMI settings under the User Mapping. To give you an idea of the size of the environment, there are around 2500 Windows clients.
I know WMI is not working as the PAN200 device is not updating it's mapping information i.e. it shows only the mapping information for the user / IP address mapping I sent to it via the RESTful api:
https://pan200ipaddress/api/?type=user-id&vsys=vsys1&cmd=<uid-message><version>1.0</version><type>update</type><payload><login><entry name="lab\test1" ip="192.168.1.1"/></login></payload></uid-message>
It seems to me that either the receiving firewalls are not 'asking' the PAN200 to carry out the WMI probe or the PAN200 is unable to for whatever reason. The PAN200 is configured on the internal client network so there isn't an issue with network filtering. I should also state that the PAN200 is only linked to the network using it's mgt interface - there are no other connections.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-01-2013 04:46 AM
what do you see output
debug user-id dump probing-stats
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-01-2013 05:09 AM
So, on the PAN200 (UID Agent) the result is:
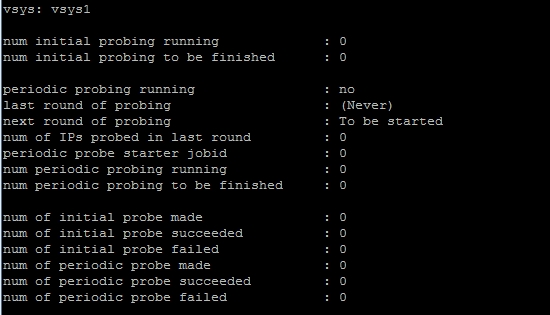 I
I
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-03-2013 01:13 AM
Thanks for your assistance Panos. The issue is now solved.
It seems that if you enable WMI client probing on the policy enforcement firewalls (i.e. not the PAN200 which is being used as a UID agent) the probes do in fact take place. So it stands to reason that PANOS UID Agent does not carry out a WMI probe on behave of the policy enforcement firewalls. This behaviour is not very well documented.
- 6669 Views
- 6 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Unable to delete users sessions on the firewalls (using Panorama API or FW cli) that managed by Panorama when the client=Panorama in Automation/API Discussions
- Packet capture for specific ip like signature match in Automation/API Discussions
- Custom Application Signature in Automation/API Discussions
- Activeync, iislogs and user-id in Automation/API Discussions



