
- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Palo Alto Networks recently became aware of an issue impacting PAN-OS features where SAML based authentication is used, which may allow a malicious attacker to authenticate successfully to various services without valid credentials. Impacted devices and software include the GlobalProtect Gateway, GlobalProtect Portal, GlobalProtect Clientless VPN, Captive Portal, and Prisma Access, including PAN-OS and Panorama web management interfaces.
The vulnerability requires specific configuration settings on PAN-OS to be enabled for successful exploitation. We believe the potential for impact is high, and the required configuration may be common when single-sign-on providers like Okta are used.
Advisory Link: https://security.paloaltonetworks.com/CVE-2020-2021
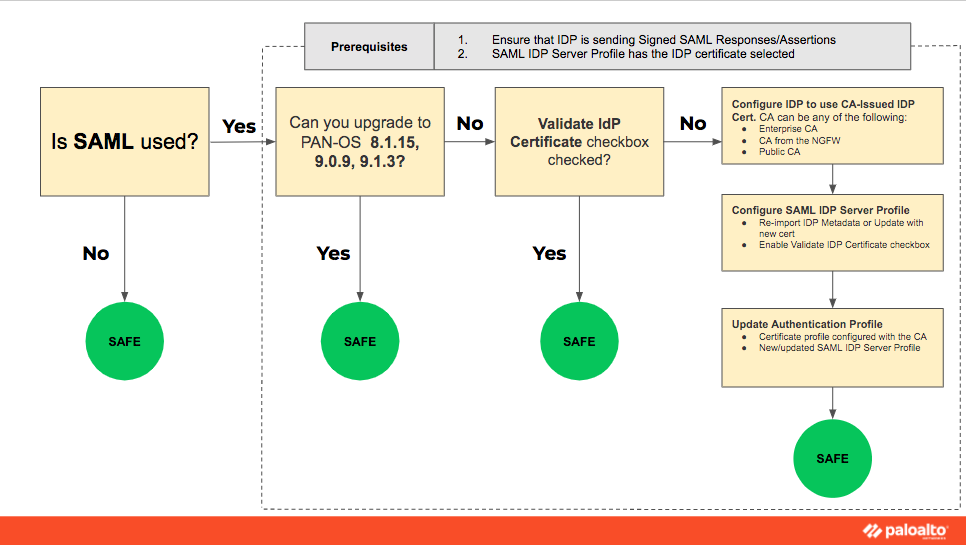
Devices and software leveraging SAML authentication are vulnerable to this issue. Resources that can be protected by SAML-based single-sign-on authentication are:
Devices must leverage SAML authentication to be vulnerable. This issue can not be exploited if SAML is not being used for authentication. This issue can not be exploited if the 'Validate Identity Provider Certificate' option is turned on.
| Versions | Affected | First Fixed | Unaffected |
|---|---|---|---|
| 9.1 | < 9.1.3 | 9.1.3 | >= 9.1.3 |
| 9.0 | < 9.0.9 | 9.0.9 | >= 9.0.9 |
| 8.1 | < 8.1.15 | 8.1.15 | >= 8.1.15 |
| 8.0 | 8.0.* | ||
| 7.1 | 7.1.* |
* Indicates all minor releases in PAN-OS version
For available mitigation options please see the Knowledge Base article on "Securing your SAML Deployments." Additional steps may be required to invalidate Authentication Override Cookies for existing sessions as discussed in "How To Invalidate Previously Issued GlobalProtect Authentication Override Cookies."
While leveraging the mitigation options posted will reduce the attack surface, customers are advised to treat the need to upgrade all impacted devices globally with a high sense of urgency. The guidance provided below is intended to act as a short-term countermeasure until customer devices can be upgraded. For customers not leveraging SAML authentication as of this time, it is strongly advised to proceed with the upgrade to ensure a vulnerability is not introduced should a SAML integration be added in the future.
Advisory Link: https://security.
Knowledge Base Articles:
Securing your SAML Deployments
Identity Provider Configuration for SAML
How To Invalidate Previously Issued GlobalProtect Authentication Override Cookie
Verifying Prisma Access Configuration
Tips for Identification of Authenticated Users and GlobalProtect Authentication:
How to Check User Access by GlobalProtect for Specific Time Period
How to Run a Report for Previous Logged in GlobalProtect Users
Thanks for taking time to read my blog.
If you enjoyed this, please hit the Like (thumbs up) button, don't forget to subscribe to the LIVEcommunity Blog.
Stay Secure,
Kiwi out!
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
| Subject | Likes |
|---|---|
| 5 Likes | |
| 3 Likes | |
| 3 Likes | |
| 3 Likes | |
| 2 Likes |
| User | Likes Count |
|---|---|
| 12 | |
| 4 | |
| 3 | |
| 3 | |
| 2 |




