- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Integration Office 365: Get mail reported by user
- LIVEcommunity
- Discussions
- Security Operations
- Cortex XSOAR Discussions
- Integration Office 365: Get mail reported by user
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-05-2022 09:22 AM
Hi,
one question about O365 integration. Maybe it's a O365 question, not a XSOAR one, but I'd like to know if I can do it with XSOAR.
I have an alert "Email reported by user as malware or phish" from Microsoft Graph Identity and Access integration. I have this data from the alert:
[{"aadUserId":null,"accountName":"xxxx.yyyy","domainName":"xxxxxx.com","emailRole":"unknown","isVpn":null,"logonDateTime":null,"logonId":null,"logonIp":null,"logonLocation":null,"logonType":null,"onPremisesSecurityIdentifier":null,"riskScore":null,"userAccountType":null,"userPrincipalName":"xxxxxx.yyyyyyy@xxxxxx.com"},{"aadUserId":null,"accountName":"Resilinc Partner Relations \xxxxxxx","domainName":"zzzzz.com\u003e","emailRole":"sender","isVpn":null,"logonDateTime":null,"logonId":null,"logonIp":"111.222.333.444","logonLocation":null,"logonType":null,"onPremisesSecurityIdentifier":null,"riskScore":null,"userAccountType":null,"userPrincipalName":"Resilinc Partner Relations \xxxxxxx@zzzzz.com\u003e"},{"aadUserId":null,"accountName":"xxxxxx.yyyyyyy","domainName":"xxxxxx.com","emailRole":"recipient","isVpn":null,"logonDateTime":null,"logonId":null,"logonIp":null,"logonLocation":null,"logonType":null,"onPremisesSecurityIdentifier":null,"riskScore":null,"userAccountType":null,"userPrincipalName":"xxxxxx.yyyyyyy@xxxxxx.com"}]I need to get the original mail that the user reported as malicious, but from the alert I have not any message Id or similar.
I have searched using the from and to fields, but it's not the right query.
Do you know how can I get the source e-mail? I have browsed the MS documentation but found nothing, and I don't know all the commands for XSOAR, maybe you know "any trick"...
Thanks for your help!!
M.
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-24-2023 02:12 PM
Hi all,
finally I did what I needed using MS Defender integration.
Using this integration, the incidentes fetched have the messageid and, using ews-search-mailbox with this messageid and the mailbox, i can get the message. I can also use the "Microsoft 365 Defender - Threat Hunting Generic" or "Get Original Email - EWS v2" Playbook to have more information or the message in EML format.
Office API and its integrations are, sometimes, difficult to manage and understand... 🙂
Regards!
M.
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-21-2022 04:31 AM
I'm not 100% sure, but I have strong doubts that the Graph integration / Microsoft SecurityCenter platform has this functionality. You can use the EWS O365 integration for this.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-02-2023 07:08 AM
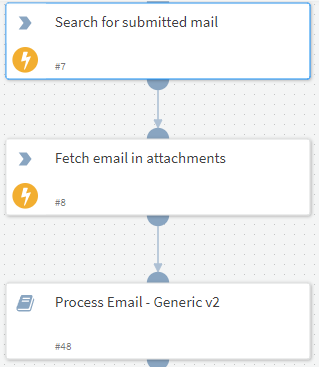
We set-up the report message add-in to send a duplicate in attachment to our phishing mailbox since you are unable to fetch an email that has been soft or hard deleted.
We use the Network Message ID from the alert to search the email in the phishing mailbox, extract the mail from attachment and process it as seen below:
1. ews-search-mailbox (EWSO365)
2. ews-get-attachment (EWSO365)
3. Process Email - Generic v2
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-10-2023 03:40 PM
Thanks for your help!! I've been a bit stuck researching this. The problem is that if I search the mailbox (with from-to-date filters), I can get several results, and I cannot be sure which mail has been involved in the alert.
I have been reading about the Hunting capacities in MS Defender addon (https://xsoar.pan.dev/docs/reference/integrations/microsoft-365-defender#microsoft-365-defender-adva...). I'll post anything if I get any result...
Regards.
M.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-24-2023 02:12 PM
Hi all,
finally I did what I needed using MS Defender integration.
Using this integration, the incidentes fetched have the messageid and, using ews-search-mailbox with this messageid and the mailbox, i can get the message. I can also use the "Microsoft 365 Defender - Threat Hunting Generic" or "Get Original Email - EWS v2" Playbook to have more information or the message in EML format.
Office API and its integrations are, sometimes, difficult to manage and understand... 🙂
Regards!
M.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-15-2024 12:19 AM
Hi Team
The customer received a notification email from Microsoft saying that they have telemetry data originating from the XSOAR EWS O365 integration that we use, is accessing MS Teams data. They will proceed to block such traffic in early April 2024 without exception. In that telemetry data they are seeing 'Get-Folder' executions against MS Teams data specifically. In looking up the EWS O365 integration documentation (https://xsoar.pan.dev/docs/reference/integrations/ewso365) there is no detail about it accessing MS Teams data.
I would like to clarify and confirm :
1) Is the EWS O365 integration accessing MS Teams data ? Does it use 'Get-Folder' executions ?
2) If the answer to the #1 is yes, when the traffic block occurs in April 2024, will it have a negative impact on the EWS O365 integration which we currently use to send/retrieve emails and move emails to different folders within a specific mailbox ?
Please assist.
- 1 accepted solution
- 4676 Views
- 5 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Cortex XDR email data integration in Cortex XDR Discussions
- Azure Active Directory users - Incorrect padding in Cortex XSOAR Discussions
- Find Incidents/Alerts triggered based on 3rd Party Integrations in Cortex XDR Discussions
- XSOAR incident in Qradar in Cortex XSOAR Discussions
- Fetching Microsoft Defender for Office 365 Alerts in Cortex XSOAR Discussions