- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Authentication failed from AD
- LIVEcommunity
- Discussions
- General Topics
- Re: Authentication failed from AD
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Authentication failed from AD
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-03-2020 05:19 AM
Hello,
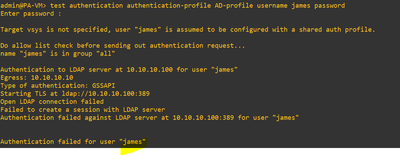
I have integrated the AD with Paloalto , it is working fine and i can see the IP user mapping is correct, once i tested authentication profile
I got the below error:-
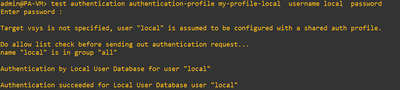
Once i tested the authentication by local profile it is working fine.
Can anyone help me on this to reolve this issue.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-03-2020 12:49 PM
IP to UserMapping is separate than LDAP.
Based off your error message in the first screenshot, 'Failed to create a session with LDAP server', I would point towards a network level issue from the firewall MGMT IP (assuming no custom service routing) and the LDAP controller. Could also be permissions on the service account used, but I would bet dollars to donuts it's network level. Also - TLS/389? I know it's possible, but...might need to swap to port 636
Local auth used in second is just authenticating against the local user database on the FW, no LDAP connection needed
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-03-2020 05:08 PM - edited 08-03-2020 05:12 PM
Is this new setup?
Please check below document it has step bu step info on troubleshooting
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClpoCAC
Also try below commands to do the TCPdump on the management port
Command to capture LDAP traffic if using management port
> tcpdump filter "port 389"
Command to view the pcap taken off the management port
> view-pcap mgmt-pcap mgmt.pcap
Regards
Help the community: Like helpful comments and mark solutions.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-04-2020 12:05 PM
Yes this is a new setup. i have gone through the documents and changed the service account with ssl/tls 636 port.
My LDAP, UID, DNS service route changed via data plane interface I have tried everything but still, the issue is the same.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-04-2020 12:26 PM
Will need to check your authd.log if you've checked everything from above. I would also double check your firewall policy to ensure that dataplane source interface/zone is allowed to the other zone that 10.10.10.100 exists in.
I've also noticed theres more helpful information in group mapping failures versus auth attempts (lists bad password/fail to connect/etc). Do you have group mapping configured for the associated ldap profile? If you show the group mapping state, what is the output?
CLI
show user group-mapping state <name of group mapping profile referencing the LDAP Profile>
Future troubleshooting for auth specific, if group mapping is successful.
SSH to firewall, issue the following command
tail follow yes mp-log authd.log
while that is running, test authentication via another SSH window and paste results (sans business specific information that may be present)
- 8145 Views
- 4 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Prisma cloud console is failing to launch in General Topics
- Geo blocking after GP login in GlobalProtect Discussions
- New cert GP cert prompt for people testing Yubikeys for windows logon in GlobalProtect Discussions
- Address Group and Tag limitations in General Topics
- Assistance with LDAP Authentication in General Topics