- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Feature Request List
- LIVEcommunity
- Discussions
- General Topics
- Re: Feature Request List
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Feature Request List
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-07-2018
02:00 PM
- last edited on
10-07-2020
08:08 AM
by
![]() BPry
BPry
Hi community
In a lot of topics there are discussions and questions about PAN-OS enhancements and missing (not yet implemented) features. So far the PaloAlto Feature Request list isn't available to the public but in a lot of these existing topics feature request IDs (FR ID) are mentionned. Even knowing that PAN-OS is already a feature rich firewall operating system, there is always room for improvement, so I thought it might be helpful for others (and myself) to collect these existing public available FR IDs and summarize them in one topic.
| ID | Description | Additional Information/Workaround | Implemented in |
| 130 | Filter Logs by Adress Groups | - | - |
| 204 | Automatic rollback to last "good" configuration | - | - |
| 241 | SMTP authentication in Email server profile | - | - |
| 339 | Add negate function to all security policy columns | ||
| 776 | increase custom report limit beyound Top 500 | Also in FR ID 1636 and 1693 | - |
| 889 | Mac Address as match criteria in security policy | - | - |
| 913 | Preview response pages directly in the WebUI without having to download them | - | - |
| 919 | Support for ICAP (Internet Content Adaption Protocol) | - | - |
| 986 | Custom Reports for System logs | - | - |
| 1172 | Ignore usergroup from User-ID | - | - |
| 1225 | Participation of PA firewalls in Spannin Tree | - | - |
| 1370 | URL column length limit in Reports | - | - |
| 1696 | Include Interface IP in SNMP MIB | - | - |
| 2153 | Terminal Server Agent for Linux | - | - |
| 2287 | Different ACLs for https, snmp, ... | - | - |
| 2666 | VRRP Support for clusters between PA and other devices | - | - |
| 2924 | Optain Global Protect IP from DHCP Server | - | - |
| 3051 | User Activity Report Enhancement (detailed web-browsing statistics including time spent) | - | - |
| 3060 | DHCPv6 client support | - | - |
| 3495 | Custom reports for system Logs | - | - |
| 3591 | /31 subnetmask support for HA1 link | - | - |
| 4035 | Dedicated Log category for Global Protect | - | - |
| 4443 | Support for USB modems (3G/4G/5G ...) | - | - |
| 4454 | gray out policies with expired schedules | - | - |
| 4507 | Show current interface bandwidth in a dashboard widget and log over time. | - | Not a dashboard widget but throughbut statistics and other device health metrics are implemented in PAN-OS 8.1 |
| 4603 | Concurrent GP VPN session limit per User | - | - |
| 4669 | Generate system log upon schedule end | - | - |
| 4670 | Proactive notification for policies with soon expiring scheduled | - | - |
| 4788 | Block emails based on domains in "to", "cc" or "bcc", also log these in addition to only "to" and reply with smtp 541 when blocked | - | - |
| 4920 | Display SFP, SFP+ and QSFP serial number | - | - |
| 5000 | SCEP Server integrated in the firewall | - | - |
| 5078 | per-IP Traffic shaping | - | - |
| 5357 | Global Protect Agent Uninstall Password | - | - |
| 5612 | Automatically disable and remove policies with expired schedules | - | - |
| 5678 | Log the TLS version of websites and enable reporting about this | - | - |
| 5686 | DHCP Client Class-ID Setting | - | - |
| 5844 | BGP SNMP monitorings | - | - |
| 6186 | Log and report search keywords | - | - |
| 6548 | Customizable SMTP Response for Vulnerability Protection | - | - |
| 6609 | Add "Threat Email" to email subject when something malicious was detected and also log "cc" and "bcc" | - | - |
| 7365 | DHCPv6 Server support | - | - |
| 7654 | Support of DIPP with non-strict recognition by devices (Cisco ASA like) | - | - |
| 7832 | User-ID for Azure-AD authenticated users | - | - |
| 9113 | Integrated addressobjects for well-known cloud services | - | - |
| 9195 | OCSP stapling support for inbound decryption | - | - |
| 9285 | Custom configrable MFA integration | - | - |
| 9509 | DoH (DNS over HTTPS)/DoT (DNS over TLS) Support for DNS Sinkhole Feature | - | - |
| 9522 | App-ID for DoH (DNS over HTTPS) / DoT (DNS over TLS) | Custom App-ID for DoH | - |
| 9563 | Configurable Time when Global Protect Captive Portal Notification should be shown | Captive Portal Notification Delay | GlobalProtect 4.1 |
| 9958 | Azure Information Protection (AIP) Tag support for Data Filtering | Release Notes Content Version 8129 | PAN-OS 8.0 starting with Content Update 8129 |
| 10173 | Automatically open browser when Global Protects a Captive Portal and opens a configurable website | Automatically Launch Webpage in Default Browser Upon Captive Portal Detection | Global Protect 5.0.4 starting with Content Update 8181 |
| 10931 | use logd disk space (33%) for elasric search in Panorama | Panorama disk space allocation | - |
| 11012 | Windows Server 2019 Support for User-ID Agent | - | User-ID Agent/PAN-OS 9.0.2 |
| 11153 | Completely remove Global Protect 4.0 Design out of Global Protect 5+ | - | - |
| 11211 | Forced Global Protect network rediscover after IP change | - | - |
| 11251 | Panorama High Availability: MFA using SAML (Okta) | - | - |
| 11524 | Use FIB for route monitoring instead of gateway of the route itself | - | - |
| 11763 | Include the username in the csv with the URL logs when running a user activity report | Download thelogs directly from the URL logs | - |
| 11764 | Allow for more "User Activity Report" customization - pie charts, different bar charts, color, tables, etc. | - | - |
| 11765 | WebUI Color/Theme changes (Dark mode) | already possible with some browser extensions (or maybe even directly in the browser) by modifying the css | - |
| 12264 | Reporting based on HIP match failures, specially which failed items | - | - |
| 12783 | Log E-Mail links forwarded to Wildfire | - | - |
| 13046 | Support gMSA accounts for User-IP-Mappings | - | - |
| 13414 | Negate source User | - | - |
| 15246 | Import/Export ACC and Dashboard Widgets. | - | - |
So far I found a few and I'll try to update this topic regularly. If you also know about existing requests, please write them here.
Regards,
Remo
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-15-2019 06:26 AM
Added FR ID 889 - Mac Address as match criteria in security policy
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-15-2019 06:29 AM
Added FR ID 11135 - Completely reomve Global Protect 4.0 Design out of Global Protect 5+
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-25-2019 02:49 AM
Added FR ID 11211 - Forced Global Protect network rediscover after IP change
(This one is fo situations where the network is changed from external to an internal, Global Protect should do a network rediscover instead of just reconnecting to the GP Gateway)
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-25-2019 05:57 AM
@Remo wrote:Added FR ID 11211 - Forced Global Protect network rediscover after IP change
(This one is fo situations where the network is changed from external to an internal, Global Protect should do a network rediscover instead of just reconnecting to the GP Gateway)
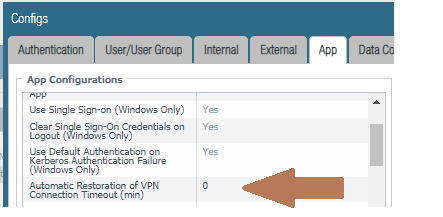
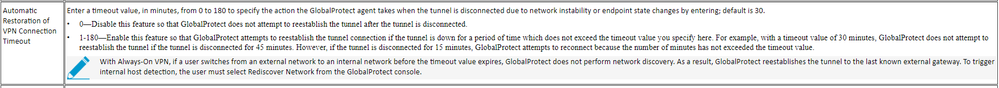
I thought this was already there. I worked with eTAC and some GP issues we were having. One thing I wanted was for every network event, from just a disconnect / reconnect, to changing IPs I wanted the connection to always "reverify" the state the client should be in. I was told this field in the config "Automatic restoration of VPN connection Timeout" needed to be set to 0. This would make the client always do a network discovery.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-25-2019 06:35 AM
Yes, you are right. When setting this value to 0 then this is correct, but this results (in the situation of our customer) that also in short connections losses the user has to log in again using MFA. Because of that I created this feature Request so that after short connection losses (for example when a user works in a train) the connection restoration is possible but still GP does not reconnect when changing from external to inernal.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-17-2019 08:10 AM
Added FR ID 4443 - Support for USB modems (3G/4G/5G ...)
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-19-2019 08:37 AM
I'd like to add a feature request:
run a "user activity report"
in the "Download URL logs" link which open up a CSV file, please in this file include either the original Username or IP address whihch was entered into the box on the original "User Activity Report" diaglog.
We are concerened that Lawyers might not hold the file up in court since it doesn't have a username / IP tied to it. Only the "Download User Activity Report" has that.
Thanks,
dannon
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-19-2019 08:42 AM
To actually request a feature request you need to reach out to your SE. This simply tracks the existing feature requests that already have a FR associated with them. Once your SE has the FR number please update us here.
"We are concerened that Lawyers might not hold the file up in court since it doesn't have a username / IP tied to it. Only the "Download User Activity Report" has that."
Just FYI, Lawyers could still throw out this report unless you have other logs to back up what's reported to the firewall. You would need proof that the firewalls indicated user is actually correct via other logs, such as DHCP logs and Event Security logs if in a Windows environment.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-01-2019 05:30 PM
I've arranged an FR for an issue I raised in a post here a few weeks back to allow for Static route path monitoring to be done using the FIB as opposed to being locked to the gateway of the route itself.
11524
This is my OP which outlines the issue which this resolves.
https://live.paloaltonetworks.com/t5/General-Topics/Route-Monitoring-Possible-FR/m-p/257932#M73180
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-01-2019 05:45 PM
@El-ahrairah wrote:I've arranged an FR for an issue I raised in a post here a few weeks back to allow for Static route path monitoring to be done using the FIB as opposed to being locked to the gateway of the route itself.
11524
This is my OP which outlines the issue which this resolves.
https://live.paloaltonetworks.com/t5/General-Topics/Route-Monitoring-Possible-FR/m-p/257932#M73180
FR ID 11524 is added to the list. Thanks @El-ahrairah for sharing.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-15-2019 03:07 PM
Added FR ID 11012 - Windows Server 2019 support for User-ID Agent
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-04-2019 08:23 AM
Reached out to my SE with these:
1. run a "user activity report"
in the "Download URL logs" link which open up a CSV file, please in this file include either the original Username or IP address which was entered into the box on the original "User Activity Report" dialog. We are concerned that Lawyers might not hold the file up in court since it doesn't have a username / IP tied to it. Only the "Download User Activity Report" has that. - FR11763
2. Log and report search keywords - user typed in suicide into Google - FR6186
3. Show current interface bandwidth in a dashboard widget. Be able to log over time. - FR4507
4. Log /report / make a column header the TLS/SSL version detected on HTTPS sites. - FR5678
5. Allow the GUI to change colors - themes. Maybe a dark theme?- FR11765
6. In "Response Pages", have a "Preview" link, so that we can see the page quickly without having to download and open in another browser. Useful when making changes.- FR913
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-09-2019 11:20 AM
Hi @dannon
I have added your FR IDs to the list. And in addition I have some comments:
@dannon wrote:1. run a "user activity report"
in the "Download URL logs" link which open up a CSV file, please in this file include either the original Username or IP address which was entered into the box on the original "User Activity Report" dialog. We are concerned that Lawyers might not hold the file up in court since it doesn't have a username / IP tied to it. Only the "Download User Activity Report" has that. - FR11763
What abour simply downloading the logs directly from the URL logs?
@dannon wrote:3. Show current interface bandwidth in a dashboard widget. Be able to log over time. - FR4507
Since PAN-OS 8.1 there is a device health monitoring in panorama which includes bandwidth
@dannon wrote:5. Allow the GUI to change colors - themes. Maybe a dark theme?- FR11765
This is already possible with browser extensions (maybe even directly in the browser) by enabling high contrast modes or by changing the css.
@dannon wrote:6. In "Response Pages", have a "Preview" link, so that we can see the page quickly without having to download and open in another browser. Useful when making changes.- FR913
Because of the low number of this feature request this one is already pretty old so I think the chances that this (checkpoint) feature will be implemented are not that high...
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-10-2019 01:59 PM
FR-11251: Panorama High Availability: MFA using SAML (Okta)
When using SP-initiated SSO from PAN-OS via Okta and SAML, the SSO profile selection is sync'd between Active/Passive. Thus, you can only log in to one of your devices from an HA pair--e.g. if your SAML auth profile and its associated configuration in Okta redirects to the Active device's ACS URL, then you can only authenticate to the Active device. If you initiate SSO from the the Passive device, it will fail because you are redirected to the Active device's ACS URL and the assertion is for the Passive device.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-11-2019 07:06 AM
We desperately need PANOS to support more than 8 ae interfaces. We have some large chassis (with multiple vsys) that are embarrassingly underutilized because we can't assign more ae interfaces to them. This seems like such a minor tweak, but it would help us fully use the hardware investments that we have made. Please help!
- 106681 Views
- 147 replies
- 21 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Assistance with LDAP Authentication in General Topics
- ServiceNow CMDB data to XSIAM in Cortex XSIAM Discussions
- XSIAM Dynamic filtering in exclusions in Cortex XSIAM Discussions
- GRPC status UNAVAILABLE in intelligent offload in VM-Series in the Private Cloud
- Cortex XDR - How do I open a new feature request? in Cortex XDR Discussions