- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Havex Malware
- LIVEcommunity
- Discussions
- General Topics
- Re: Havex Malware
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Havex Malware
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-24-2014 03:47 AM
Hi all,
Do you have any information about PAN detection capability for the Havex malware family: http://www.f-secure.com/weblog/archives/00002718.html
Threat vault seems to produce no hits at the moment.
Tuomo
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-02-2014 09:54 AM
I only see one SHA reported as malware and rest as benign.
Please open a case with palo alto support and they'll address the issue with wildfire.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-02-2014 09:56 AM
I don't have a sample of the malware, I'm just "stirring the pot" to be honest
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-03-2014 02:42 AM
Interesting info in Brightclouds Webinar on Dragonfly/havex right now,
I asked if there has been any information exchange between Symantec (which has a lot of information - and protect users - on Dragonfly/havex) and Paloalto. They said the did info ex with a lot of company, but not PAN - why not?
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-04-2014 03:44 AM
Based on your responses here, I assume you work for PA. Can you explain what happens with new signatures like this against the existing file database that was deemed benign?
Some of these "benign" files will be previously unknown viruses like Havex. Does Wildfire check them again against new signatures?
If a previously flagged benign file is uploaded again, is this automatically benign from the previous verdict?
In short, how does PA clean up the hash database to be sure the new viruses are successfully identified?
ACE PanOS 6; ACE PanOS 7; ASE 3.0; PSE 7.0 Foundations & Associate in Platform; Cyber Security; Data Center
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-09-2014 12:27 AM
Hi
According to latest Application and Threat Content Release Notes for version 445
New Anti-spyware Signatures (5)
| Severity | ID | Attack Name | Default Action | Minimum PAN-OS Version | Maximum PAN-OS Version |
|---|---|---|---|---|---|
| critical | 13471 | DeepPanda.Gen Command And Control Traffic | alert | 3.1.0 | |
| critical | 13472 | DeepPanda.Gen Command And Control Traffic | alert | 3.1.0 | |
| critical | 13479 | Gypthoy.Gen Command And Control Traffic | alert | 3.1.0 | |
| critical | 13480 | PowerLoader.Gen Command And Control Traffic | alert | 3.1.0 | |
| critical | 13488 | Havex.Gen Command And Control Traffic | alert | 3.1.0 |
Regards
Slawek
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-09-2014 08:54 AM
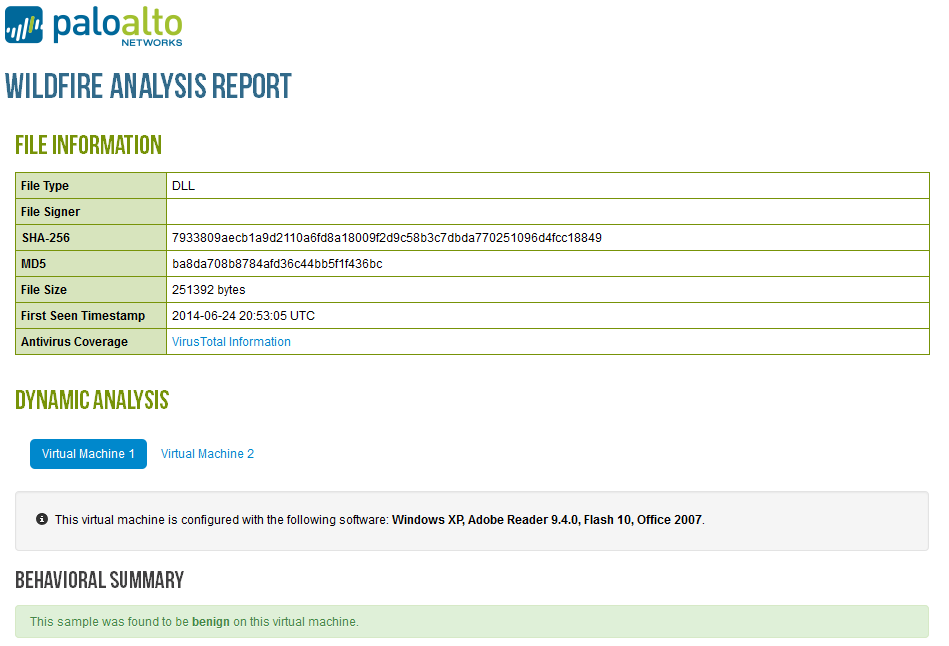
Havex is still flagged as benign by the public WildFire page.
Havex is listed here:
https://threatvault.paloaltonetworks.com/Home/VirusDetail/2889719
But the hash shows benign, here:
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-09-2014 04:28 PM
I've been looking for an official answer on how the information from AV feeds back into Wildfire and the answer seems to be it does not. Wildfire is viewed as an early warning behavioral analysis and the verdicts from this are currently remaining in place. The feeling is that the AV signatures will catch the file anyway so there is no need to feed the information back into Wildfire.
I don't think I like that answer. But I do understand that creating that feedback process and re-evaluation on issues like Havex are just an investment of time PA is not making right now.
ACE PanOS 6; ACE PanOS 7; ASE 3.0; PSE 7.0 Foundations & Associate in Platform; Cyber Security; Data Center
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-09-2014 06:21 PM
Hi Steven -- The confusion here stems from the fact that folks are looking at threatvault2.paloaltonetworks.com rather than wildfire.paloaltonetworks.com. To be clear, the Havex samples are classified as malware, have been since June 24, and would show up with that verdict if seen on a firewall that has access to the WildFire cloud today. There absolutely is a feedback mechanism in place here.
The individual VM verdicts shown in ThreatVault (e.g. "This sample was found to be benign on this virtual machine") are an oversight on our part -- they don't always correspond to the current disposition of the sample, and weren't intended for display in ThreatVault reports. I've filed a bug to have them removed so we can avoid confusion on this issue in the future.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-10-2014 04:51 AM
Thanks for the response on the process. This is the response I was looking for ultimately from PA. I do have one question then.
If the threat vault vm verdict is not the correct procedure to determine a files status, what is the procedure we should use to verify a files status in Wildfire?
ACE PanOS 6; ACE PanOS 7; ASE 3.0; PSE 7.0 Foundations & Associate in Platform; Cyber Security; Data Center
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-11-2014 09:33 AM
Hi Steven -- In the case of ThreatVault, the mere inclusion of a file indicates its status: Every file in ThreatVault meets the criteria of 1) Is a threat, and 2) Has protections available. If a file doesn't appear in ThreatVault, you can check it through the WildFire portal (or on the firewall), or by retrieving the PDF or XML report using the WildFire API.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-11-2014 02:07 PM
cblackmore, thanks for the further clarification. These are all the answers I wanted to hear. I appreciate knowing that the integration of all these threat detection methods is complete.
ACE PanOS 6; ACE PanOS 7; ASE 3.0; PSE 7.0 Foundations & Associate in Platform; Cyber Security; Data Center
- 15265 Views
- 26 replies
- 1 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!