- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
message security over http
- LIVEcommunity
- Discussions
- General Topics
- Re: message security over http
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-21-2017 08:22 AM
How does PA handle message security over http ?
Whereas https secures the communication, message security secures the content.
I would expect PA does not touch http content. But we are having issues with an application that connects to a partners server.
Application throws this error, I guess it's a pretty default .net error:
An error occurred while receiving the HTTP response to http://blabla/blablaConnectorHostService.svc. This could be due to the service endpoint binding not using the HTTP protocol. This could also be due to an HTTP request context being aborted by the server (possibly due to the service shutting down).
Partner says it has something to do with large transfers that get interrupted. I'm guessing it happens somewhere on the firewall.
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-27-2017 07:55 AM
@dieterb wrote:
@TranceforLife wrote:This is how l understand 3-way handshake :0 If you are not using user-id on trust zone please disable this future under the zone configuration
We heavily use user-id for that zone. But for some traffic, that doesn't matter. User Any solves that problem for most cases.
Ok, problem is indeed related to user-id: http traffic triggers an NTLM authentication request (if there's no user-ip-mapping) on the firewall. Application did not know how to handle that and resets session.
The trick was to put the client's fixed IP address in the exclude list for user identification for the zone. Not only in the user-id agent exclude list and/or PA user-id exclude list (what most of the time just worked because it was no http traffic).
Now the firewall doesn't ask for NTLM auth and traffic passes fine.
I also found out that it's not possible to disable NTLM entirely, is that correct ? Maybe because of captive portal ?
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-21-2017 08:42 AM - edited 03-21-2017 10:20 AM
Hi,
Good place to start is a traffic logs for this particular session (s), session-end reason and application identification. What can you see?
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-21-2017 10:11 AM
Look at your threat logs and make sure the PA isn't resseting something due to it identification anything as a possible threat.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-21-2017 10:14 AM - edited 03-21-2017 10:15 AM
good point threat logs, totally forgot about them :0 busy day............
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-22-2017 05:56 AM
Right now the application seems to generate no logging at all...
I will get back when I have something useful 🙂
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-22-2017 06:11 AM
@dieter_b make sure that you actually have logging enabled on your security policies that you suspect this should be hitting, sounds like you likely don't have it set to log at start or end.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-22-2017 06:12 AM
or traffic is not even hitting that policy!
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-23-2017 03:43 AM
I have logging enabled for start and end. And I'm pretty sure the traffic should hit the rule. Logging is enabled for almost everything (except for some dns, ntp and "internal" traffic). So if there would be a deny somewhere or a threat blocked, I would see it.
So here's the fun part:
If there's no user-to-ip mapping for the clients ip, nothing is logged.
If there is a user-to-ip mapping, I have log entries.
Session end reasons are tcp-rst-from-client and tcp-fin, so pretty normal.
Known user or not should not even matter. The rule allows Any app/service for Any user from clients fixed ip. And for troubleshooting I don't even have a security profile attached.
In a wireshark capture on the client I only get a dry RST from the server. But that could be the firewall sending a RST.
Would the option "Disable Server Response Inspection" do any good ?
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-23-2017 04:05 AM - edited 03-23-2017 04:48 AM
DSRI option may be useful under heavy server load conditions. Post the security policy here same as PCAP snip. Firewall, as far as l know, will not intercept the session (in your case as you can see tcp-rst-from-client and tcp-fin logs). If the firewall sends you RST you should see its IP address as a source. Firewall only generates a logs based on how it seing the session between client-server.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-23-2017 05:39 AM
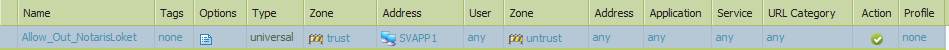
That's all there is to the rule:
Sorry I can't give PCAP, would reveal too much info.
You say firewall ip would be seen as source ip of RST. That's not the case so I assume RST is really coming from remote server.
Can anyone confirm PA does not alter http content ? There's no such thing as http message security decryption ? Or an option that blocks encrypted http messages ?
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-23-2017 05:50 AM
This is how l understand 3-way handshake :0 If you are not using user-id on trust zone please disable this future under the zone configuration:
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-23-2017 06:00 AM
@dieter_b if you don't have a profile associated with it the firewall should never issue a reset, since it should just be allowing the traffic. I would take a look at what the identified applications TCP Timeout, TCP Half Closed, and TCP Time Wait settings are. Just for giggles customize those to something completely unreasonably high and see if the issue persists. The firewall may not be seeing any type of response from the other server and terminating the session because it believes the session has gone stale.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-23-2017 07:23 AM
@TranceforLife wrote:This is how l understand 3-way handshake :0 If you are not using user-id on trust zone please disable this future under the zone configuration
We heavily use user-id for that zone. But for some traffic, that doesn't matter. User Any solves that problem for most cases.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-23-2017 07:25 AM
@BPry wrote:@dieter_b if you don't have a profile associated with it the firewall should never issue a reset, since it should just be allowing the traffic. I would take a look at what the identified applications TCP Timeout, TCP Half Closed, and TCP Time Wait settings are. Just for giggles customize those to something completely unreasonably high and see if the issue persists. The firewall may not be seeing any type of response from the other server and terminating the session because it believes the session has gone stale.
Good idea, I will give this a try. I just hope our session limit is not reached, since we're talking about http 🙂
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-24-2017 04:20 AM
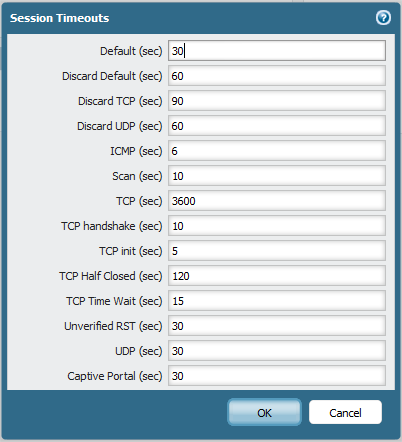
I have pretty much default general session timeouts
Connections are dropped way faster than that.
Where can I find application specific timeouts ?
- 1 accepted solution
- 10538 Views
- 16 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Global Protect Portal / Clientless VPN does not recognize SAML username after update to 10.1.14-h20 in GlobalProtect Discussions
- Why do the same Windows Server data collected using XDRC and WEC agents show different statuses in the following fields? in Cortex XSIAM Discussions
- Decryption suddenly failed for all Webpages using Sectigo Certs in General Topics
- [Cortex XSIAM ] XDR Collector Collect Windows Security Log。XDR Collectors Administration Status display "Error". in Cortex XSIAM Discussions
- Not able to log XFF (Actual Client IP) in PaloAlto Logs even when we enable XFF and URL filtering profile in Palo's in Next-Generation Firewall Discussions