- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Packet flow not properly defined
- LIVEcommunity
- Discussions
- General Topics
- Packet flow not properly defined
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Packet flow not properly defined
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-15-2018 09:02 PM
Hi Team,
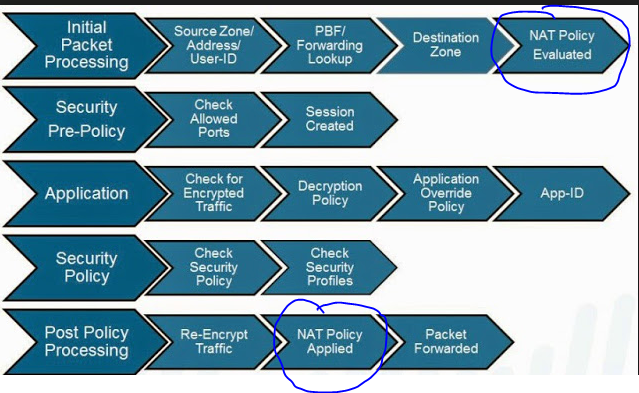
i have seen two diagrams of packet flow from palo alto website. in Below NAT Policy evaluated is shown in first step. which is part of Network processor (slow path) and NAT applied after Application and security Policy it means from security processor it is again sent to network processor for applying NAT. which says that packet is passed twice from one processor. It cant be considered as single pass.
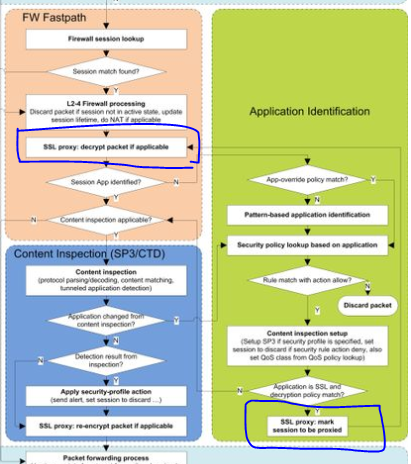
But in below diagram which is more descriptive. NAT is evaluated in slow path which is correct and NAT is applied in fast path here this makes sense to me that as network processor is continued so it should be applied here only. to avoid any multi pass.
1 QUESTION:- so question is which is correct? if both are correct then why in first one nat applied shown at last?
2. Question:- Decryption is shown in 2 places:- first one is in fast path:- after l2-l4 processing and second one is at the last of application identification.
3 Question:-there is no arrow which shows that before content inspection- application is identified. only session app is shown if session app not found then it should go for app identification and then it should come back where?????
.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-16-2018 11:22 AM
So there's a lot of documentation that you'll find all over the web about how this functions; but really the true one source of all correct information can actually be found right HERE.
1) Where the first diagram shows NAT Policy Evaluated it's the same as the second diagrams 'NAT policy lookup'. You are simply seeing if a NAT policy matches the traffic flow. This is due to how destination NATs actually function as the forward lookup changes if a DNAT is being done. Where the NAT policy gets applied is where the firewall would need to translate the L3/L4 header if needed.
2) The decryption policy lookup is part of the App identification process. This is when the firewall will actually decrypt the traffic. Why it gets mentioned twice is due to the firewall decrypting the traffic to analyze the traffic, and then encrypting the traffic again before it actually starts the forwarding process.
3) Yes there is. During the fastpath process where it says 'Session App Identified' the No would be where it actually goes through the app-id process. If the session app is already identified then it goes through to the Content Inspection process. If the application changes during the content inspection process then it goes back through the app-id process starting at 'Security policy lookup based on application'.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-17-2018 02:00 AM
I just want to be more elaborative to explain my doubt.
1.So as you answered NAT Evaluation = nat lookup. which i know. but my question is NAT applied in first policy is after all the things like packet decrypted, scanned and contenet inspection done in security profile and at last you are applying the NAT.
But in second diagram you have applied the NAT first and then you are doing other things like. app -id identification and content inspection. you are not doing NAT at last after all these things.
So first image says you will apply NAT Policy before forwarding packet to egress. after you wil check application by decryption etc; after you check security Policy,profiles and re-encrypt the traffic.
2. In second ;it is not decyrption policy lookup:- this is SSL Proxy:- decrypt packet if applicable (no lookup -direct decrypt if applicable)
session APP Identified is not explained even in link in detail, you have shared, so i expect this is ; it will create session of app once it will identify the app.
if it is new request then it wll not identify session app becuase it has not created session for that application and it will go for application Identification. so from here i can expect firewall create 2 sessions. one session is created with 6 tupple information and second is created for application which is session application.
i think this is PREDICT Session type.
3. my question is 2 time decypt is shown ; i am not asking once dycrypt then why encrypt. that i know packet need to be encrypted at last before sending.
but once your have done SSL Decryption then in application identification section at the last why decryption is added again and its arrow is going towards SSL Decrypt
SINGLE PASS:- what is meaning of single pass here ???? IN PALO ALTO??
like if a packet is processed in Network hardware engine it should not passed to again to that engine.
But in packet flow it is hapening. Or may be single pass is having different meaning.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-17-2018 09:45 AM
Throw the 'first' diagram that you posted out the window, forget about it and use the diagram that is posted on the official documentation. The linked document describes everything that you are asking and specifically calls out what SP3 is and why they call it that. Please read the provided article.
- 3824 Views
- 3 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- gp Always disconnect in GlobalProtect Discussions
- Service Connection and Cisco ASA - problem with establish VPN and BGP in Prisma Access Discussions
- Parsing and Mapping 3rd party log source logs in Cortex XDR Discussions
- I have a question about capture conditions, etc. when using packet dump in IPSec VPN. in Next-Generation Firewall Discussions
- How to trigger a "Response page" on Palo Alto NGFWs using URL filtering & Decryption in Next-Generation Firewall Discussions