- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Prevent virus with Data Patterns
- LIVEcommunity
- Discussions
- General Topics
- Re: Prevent virus with Data Patterns
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
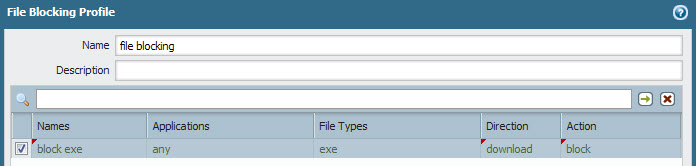
Prevent virus with Data Patterns
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-22-2012 01:59 AM
We are receiving some spam e-mails that containing links to zipped exe files with malicious code.
All the exe files have in common a series of underscore characters, for example: fattura.pdf_________________.exe or informazioni.pdf____________________.exe We send to Palo Alto Support the exe file for the threat identification by Wildfire, but currently there aren't signatures that recognize it.
We try to block the download of the exe file setting up a custom data pattern signature with this Regex: .*(__________.exe) but it doesn't works. We also try .*(__________\.exe) but users can still download it. In security profiles - data filtering we see the alert and block threshold to 1. How can we block the file download? Note that the zip filename and the download path often change, the only common attribute is the underscore characters in the .exe filename.
Thanks
Matteo
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-22-2012 03:13 AM
Thanks Roland for the reply, but I don't want to block all the exe files, but only the ones with the underscore characters in the filename.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-22-2012 10:24 AM
Do you really want to take part of that cat and mouse game ? Today it's an underscore tomorrow it's a dash....
Usually our customers security policies do not allow to download "risky" filetypes, exe files are considered to be a risky file type by most of our customers. If there should be a justified need to download an exe for example an exception can be configured and the download will be carried out from a dedicated "download PC", a single IP address or user for which a sec. rule has been made up.
However if you really want to play the game, how does your custom data pattern look like ? In particular the regex is the interesting bit.
rgds Roland
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-22-2012 10:37 AM
If you dont want to block all .exe's sent to your mailserver then I think its best to setup this rule within the mailserver itself to not forward mails that contains "*_.exe" attachments.
Because when you try to do this with DLP (Data Leakage Prevention) rules you might get false positives when someone just in the body of the mail types "blablbla _.exe" since the DLP is looking on the stream passing by and not "exploding" the transmitted object into stuff like attachment etc. On the other hand writing a custom threat prevention rule should be possible for this.
Also note that the filenames can be encoded in various ways so a DLP rule will miss some of those mails aswell (unless you write a rule that covers all variants).
Use whitelisting is a far better approach (hitrate wise) than blacklisting due to the number of ways of encoding and other tricks to avoid detection.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-22-2012 10:45 AM
To my understanding it's not an exe attachment in an email it's rather a hyperlink to a zip file in an email message.
We are receiving some spam e-mails that containing links to zipped exe files with malicious code.
rgds Roland
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-22-2012 11:23 AM
Oops 🙂
Disallow "view as html" in your email clients then - problem solved... NEXT! 😉
I think this is a bit tricky...
Even if you do succeed with a DLP rule (detecting when a client tries to download "*_.exe") you would fail when the attacker change this "_" into "." or whatever char.
I think you could try setting up a URL-category filter and filter on urls ending with _.exe
A better approach would perhaps be to setup a continue page for all kind of .exe downloads (including .pif, .bat, .whs and other shit which the microsoft operatingsystems (windows) swallows without blinking).
I still believe that the blocking of these mails should be able to be taken care of in your mailserver but sure add the above methods to take care of the case when the spam bypasses your mailfilters and your clients are a bit too triggerhappy regarding clicking on links.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-23-2012 02:57 AM
However if you really want to play the game, how does your custom data pattern look like ? In particular the regex is the interesting bit.
that's my question! ![]() . Is the data pattern / data filtering functionality able to analize exe files? :smileyconfused:
. Is the data pattern / data filtering functionality able to analize exe files? :smileyconfused:
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-23-2012 04:10 AM
Is the data pattern / data filtering functionality able to analize exe files?
What's your definition of "analize exe" files in this context ?
With data pattern filtering you can match a regex to a given string like an URL for example. When the regular expression matches a string you can define actions like block or alert.
But data pattern filtering itself is not analyising file contents for malware or exploits etc.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-24-2012 03:11 AM
Thanks for the reply. I understand that data patterns / data filtering can "search" inside document files, not exe...
There is a way to block the download of zip files filtering by filename of the file included into zip file?
Ok, this is not an elegant solution, but it's simple and speedy, and we can prevent donwload of these files.
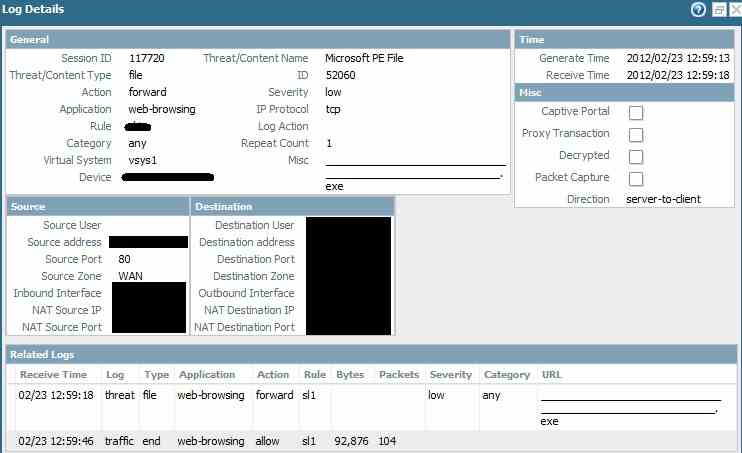
In monitor - data filtering i have the log of these files:
- 6646 Views
- 9 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!