- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
ssh problem on mac os x
- LIVEcommunity
- Discussions
- General Topics
- Re: ssh problem on mac os x
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-25-2017 11:13 PM - edited 01-25-2017 11:44 PM
Hey guys,
I have such a weird problem.
A user has to connect to a samba server. He does it on his mac with cyberduck, Port 999 and ssh.
in the monitor, the application is "incomplete", the action is "allow", and session end reason is "aged-out".
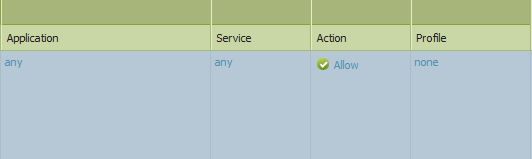
Currently, the concerning firewall policy to this public server is any app and any service.
However, the connection doesn't work. It can't connect.
What's the deal here?
PS: It worked yesterday! So I think there is something wrong with the firewall (PA 3020).
I also restored the backup from yesterday, however, it doesn't work!
What can I do? Restart dataplane? Restart the whole device?
Thank you very much.
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-26-2017 12:52 AM
Looks to me that the server is not responding to the ssh request on port 999.
Can you try from the cli on Palo and do PCAP put the filter to the server ip addrtess :
> ssh port 999 source (external ip) host (server ip)
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-25-2017 11:39 PM - edited 01-25-2017 11:41 PM
Hi,
Can you ping a server from PA? Looks like TCP handshake is not complete. Any NAT in place? Check detailed traffic log reason and bytes received/sent.
Thx,
Myky
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-25-2017 11:50 PM
Yes I can ping the public ip of the server. as source interface I used the gateway which the mac uses.
Yes, there is NAT in place.
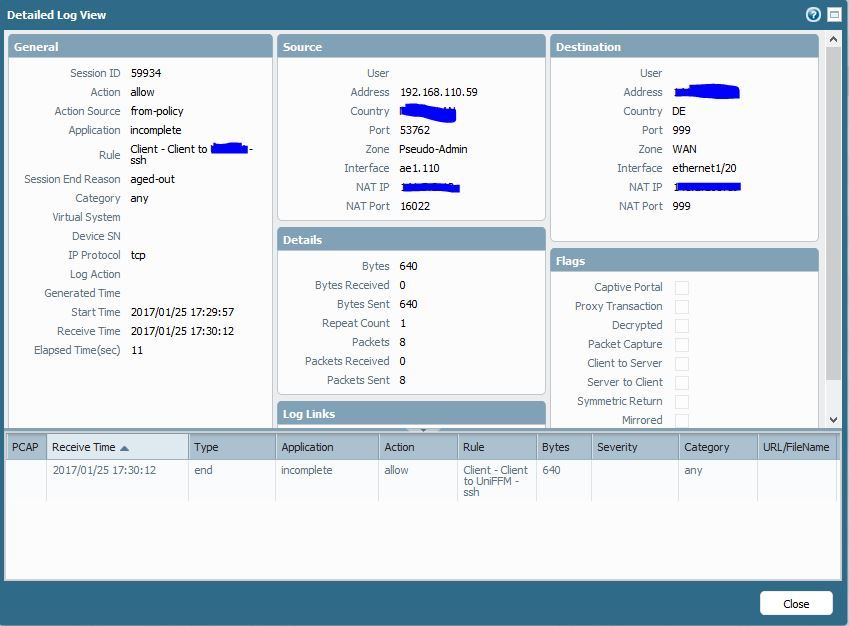
detailed log view:
Bytes send: 640
Bytes received: 0
Repeat Count: 1
Packets: 8
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-26-2017 12:04 AM - edited 01-26-2017 12:06 AM
Hi,
Looks like you stealing an information:) Just post snip of your detailed session and NAT rule for the client (wipe sensitive info from logs). What version of PAN-OS you running?
Thx,
Myky
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-26-2017 12:11 AM - edited 01-26-2017 12:17 AM
Hey Myky,
sorry.
Security Rule:
NAT Rule is just a dynamic-ip-and-port Source Translation.
PAN OS: 7.0.7
The weird thing is, this worked yesterday.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-26-2017 12:52 AM
Looks to me that the server is not responding to the ssh request on port 999.
Can you try from the cli on Palo and do PCAP put the filter to the server ip addrtess :
> ssh port 999 source (external ip) host (server ip)
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-26-2017 01:59 AM
Hi MPI-AE,
does the server listening to port 999 or is it 22 which is often used for ssh. As it worked before did you do nat as well ?
Regards,
Klaus
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-26-2017 03:02 AM
You were right, our public NAT IP was blocked in the server's internal firewall.
Thank you!
PS: What effect does "Restart Dataplane" under Device -> Operations have?
When do I use it?
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-26-2017 04:41 AM
Good point actually. As it was a silent drop (no RST or reject received by PA). Dataplane @reaper should have an answer. l never use that option
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-26-2017 05:59 AM
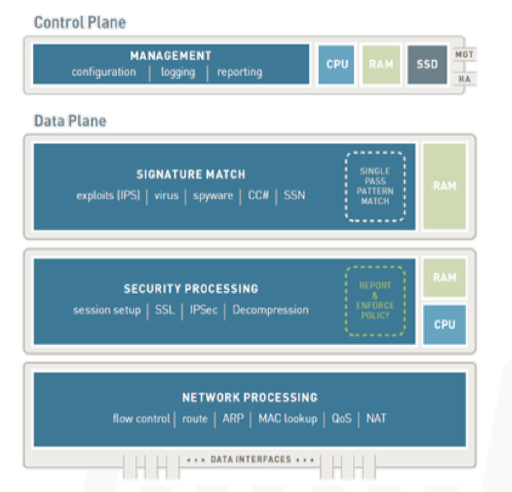
The dataplane is what actually processes all of your traffic. Restarting it would essentially temporarly stop traffic from being processed while the dataplane comes back up. You really only use it if you suspect that one of the processes isn't functioning correctly and need to restart it without actually restarting the box. It's quite a bit faster than restarting the whole thing as you only have to wait for 'half' the box to come back up. This graph might help.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-26-2017 06:06 AM
@BPry Pretty good explanation l would say. I did play with management plane process restart where the issues seen more often
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-26-2017 06:18 AM
@TranceforLife I would say that the majority of issues that people run into can be attributed to a management process and not a dataplane process. Really since restarting the dataplane is going to have an impact anyways most of the time if we do run into an issue that could be fixed with a dataplane restart we just restart the whole thing.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-26-2017 07:10 AM
Agreed same time control plane will get refreshed wich is also a good thing :0
- 1 accepted solution
- 8075 Views
- 12 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- XSIAM API pagination in Cortex XSIAM Discussions
- Palo Alto FW manage by SCM - problem with HA in Strata Cloud Manager
- HA ACTIVE firewall is failing when commit in General Topics
- Understanding the Agent Security Problem in AI Runtime Discussions
- Migration problem from PA220 to PA540 - Virtual Router in Next-Generation Firewall Discussions