- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
SSL Decryption bug in PAN-OS 9.1.14
- LIVEcommunity
- Discussions
- General Topics
- SSL Decryption bug in PAN-OS 9.1.14
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-23-2022 10:58 AM
I recently upgraded from panos 9.1.13-h3 to 9.1.14 then SSL decryption stopped working, in the traffic monitor there wasn't any decryption error but when i excluded a PC the internet worked
and it seams other people are also having the same issue (Reddit ), but its not in the known issue list until now
so i had to revert to the previous version and its working now fine
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-06-2022 02:07 AM - edited 06-06-2022 02:08 AM
It looks like that a workaround has been published or am I wrong?
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-23-2022 11:54 AM - edited 05-23-2022 11:55 AM
I don't know if this is your exact issue, but it seems as if we are tracking something internally. PAN-194219, the software packet buffers are depleting erroneously during HTTP/2 inspection only post 9.1.14 upgrade, and subsequently not decrypting.
I am now following the issue and will post updates / workarounds.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-24-2022 03:06 AM
Ok thank you, will not update until the issue is resolved
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-24-2022 06:54 AM
Same here. Rolling back now....I wonder why there is not any statement by PA. Or is it and I didn't find it?
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-24-2022 10:32 AM
The issue is escalated to the senior support queue, they've successfully recreated it in a lab and are now identifying root cause.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-31-2022 12:39 AM
Hi,
could you confirm that the problem is present in both RSA and ECDSA algorithm?
There's a know issue (PAN-83215) for ECDSA but I got the error with RSA.
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-31-2022 12:50 AM
The certificate that i use is also RSA
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-01-2022 09:58 AM
Good news! Root cause identified, yes, RSA will get stumped here, too:
NGFW> debug dataplane show ssl-decrypt session 321122
Session 321122(local 321122), 1.0.0.2[50393]-->2.0.0.2[443]
Proxy Flow
Index: 721716, Type: proxy, Tag: 321122, Dir: cts
Rule: CRPNY-Decrypt
Profile: 18F-Outbound-Decrypt-Office
4 Packets Pending for L7 Proc
TCP state
Server Established
MSS 1460
DELACK timer is not on, RXMT timer is not on
Recv Next: 581584158, Window: 49152, Scale: 0
Send Next: 590184458, Window: 5792, Scale: 0
Send Max : 590184458, Send Unack: 590184458
Slow Start Threshold: 1073725440
Congestion Window: 17520, RTT: 0 ticks
# of Out-of-Order Pkts: 0
# of Retrans: 0, # of DupAcks: 0
# of Unsent Pkts: 0, # of Unacked Pkts: 0
SSL State
Protocol Version: TLS1.2
Cipher : TLS_RSA_WITH_AES_256_GCM_SHA384
Peer Flow
Index: 721703, Type: proxy, Tag: 321122, Dir: stc
Rule: CRPNY-Decrypt
Profile: 18F-Outbound-Decrypt-Office
Is Closed
4 Packets Pending for L7 Proc
TCP state
Client Closed Wait
Can't recv
MSS 1460
DELACK timer is not on, RXMT timer is not on
Recv Next: 590184464, Window: 49152, Scale: 0
Send Next: 581583672, Window: 5792, Scale: 0
Send Max : 581583672, Send Unack: 581583672
Slow Start Threshold: 1073725440
Congestion Window: 17520, RTT: 0 ticks
# of Out-of-Order Pkts: 0
# of Retrans: 0, # of DupAcks: 0
# of Unsent Pkts: 0, # of Unacked Pkts: 0
SSL State
Protocol Version: TLS1.2
Cipher : TLS_RSA_WITH_AES_256_GCM_SHA384It appears we are seeing upgrade requests from servers through a TLS session, TLS1.1 requests to 1.2 or in some cases 1.3, this is not allowed per RFC. The firewall reads the request as a header frame, and then tries to extract sequential data from the incoming packets of the session. Since the session isn't terminated, the bogus packet(s) aren't dropped, session depletion happens.
We are currently researching how to terminate the session when this type of request comes in out of order.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-03-2022 05:45 AM
Yep, we just had to roll our HA environment back to 9.1.13-h3 because of this issue (RSA certs). Too bad it wasn't listed in the Known Issues.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-06-2022 02:07 AM - edited 06-06-2022 02:08 AM
It looks like that a workaround has been published or am I wrong?
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-06-2022 07:15 AM
i will wait then for when its fixed, as i don't want to downgrade HTTP/2 connections to HTTP/1.1 as a workaround
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-06-2022 05:02 PM
Indeed, it is now documented in the known issues. If your security requirements allow for HTTP1.1 / strip ALPN workaround that will suffice. If not, we are still researching the TLS upgrade requests and out of order queue.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-13-2022 05:59 PM
Root cause identified, the fix is coming in 9.1.15-h1. Your choices are upgrade (when available), strip ALPN (if allowed), downgrade/stay on 9.1.13-h3. Final answer 🙂
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-14-2022 07:24 AM
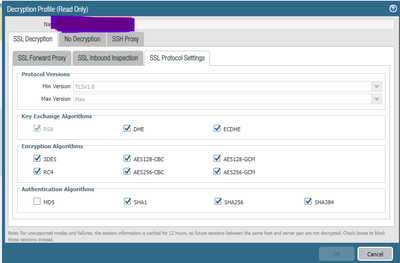
What is your TLS version? can you show the profile you are using this recommendation did not work. I will attached my profile here.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-14-2022 07:29 AM
Hi,
Min 1.0, max version "Max"
The configuration is the same as in your screenshot
- 1 accepted solution
- 13775 Views
- 22 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- URL citrix.rsieh.com is inaccessible through firewall in General Topics
- No "certificate used by" field when generating certs for SSL forward trust and untrust? in General Topics
- Action of allow but of Type policy deny in General Topics
- Google-base app, what its cpable of in escense of google apps. in General Topics
- Clientless VPN Decrypt error - 10.2.9-h1 in GlobalProtect Discussions