- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Prisma Access - additional agent config for gateway settings
- LIVEcommunity
- Discussions
- Secure Access Service Edge
- Prisma Access Discussions
- Re: Prisma Access - additional agent config for gateway settings
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-25-2020 12:40 AM
Hi,
Does anyone know if there is a possibility for another agent config for gateway settings within the Mobile_User_Template ?
It seems that whatever I put in there it's been ignored and always the DEFAULT config is given to the clients.
On on-premise devices it works as expected.
Thanks
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-02-2020 11:53 PM
Hi @SuperMario
Thanks your for response.
You are right, config order and correct Group-format are mandatory for Prisma Access.
I had to create a TAC case.
We found a mismatch between SAML authenticated users and group-mapping from Active-Directory.
pan_user_group_user_prime_uid_lookup(pan_user_group_multi_attr.c:1281): For domain\username user, domain example does not exist in group-mapping
Once the customer provided his NetBIOS domain name we got a match and it works as expected.
Case closed 🙂
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-27-2020 07:02 PM - edited 05-27-2020 07:03 PM
Hi @marceli.namyslo ,
Yes, it is possible.
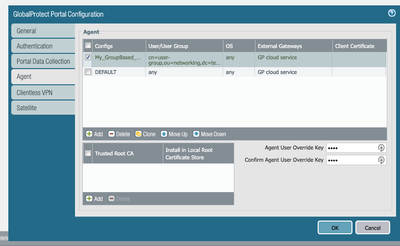
Keep in mind that the configuration will be applied from top to bottom, hence, if the default config is at the top of your configuration list, it will always be used if the user/group and OS are set to match any.
However, if you created a new config, which is at the top and is specific to a set of users/groups, and still is not being picked up, this means that our Prisma Access device is not able to recognize the user-id/group. You may need to open a TAC case to further troubleshoot your user-id configuration.
Note: for Group based configurations should be configured via their distinguished name (CN=xyz,....DC=corp,DC=com)
Here is an example:
Let us know if you have any further questions.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-02-2020 11:53 PM
Hi @SuperMario
Thanks your for response.
You are right, config order and correct Group-format are mandatory for Prisma Access.
I had to create a TAC case.
We found a mismatch between SAML authenticated users and group-mapping from Active-Directory.
pan_user_group_user_prime_uid_lookup(pan_user_group_multi_attr.c:1281): For domain\username user, domain example does not exist in group-mapping
Once the customer provided his NetBIOS domain name we got a match and it works as expected.
Case closed 🙂
- 1 accepted solution
- 5526 Views
- 2 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Unable to establish tunnel during Service Connection configuration (Details Added with Screenshot) in Prisma Access Discussions
- GlobalProtect Portal Connection Timeout when not connected to Portal in Prisma Access Discussions
- GlobalProtect App: Portal Connection Retry Expected Behavior in Prisma Access Discussions
- Replacing the vm-series firewall with prisma access in Prisma Access Cloud Management Discussions
- GP agent as user to ip mapping method for Prisma remote network in Prisma Access Discussions