- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Unlock your full community experience!
VM-Series on Azure Deployment Resources
How to Videos and Tutorials
Reference Architectures/How to Guides
Ignite User Conference Session Recordings
KnowledgeBase Articles
Note: In order to view ALL of the articles in this section and to engage in discussions on this platform, you must register for an account on LIVEcommunity. Some articles may not be viewable to unregistered users.
Customer Support Portal Resource
Note: In order to create a case, please create or active an account and register your device, which can be done in the Customer Support Portal. This area provides product support for all Palo Alto Networks Customers.
Templates, Scripts and Deployment Resources
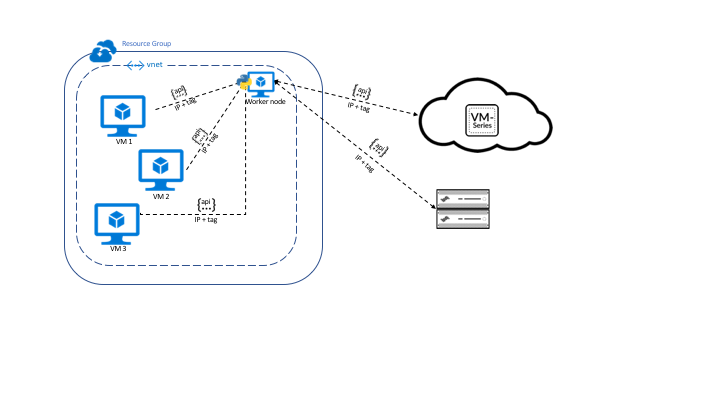
Terraform Template that deploys a two-tier containerized application on AKS secured by VM-Series
Uses a Terraform template to deploy (2) two-tiered containerized applications (Guestbook app and a WordPress server) within an AKS cluster that is protected by the VM-Series in an Application Gateway/Load Balancer sandwich.
Palo Alto Networks Community Supported
https://github.com/PaloAltoNetworks/AKS-k8s-north-south-inspection
Azure-FW-4-Interfaces
Deploys a VM-Series with 4 interfaces into an existing Microsoft Azure environment.
Palo Alto Networks Community Supported
Azure-FW-3-Interfaces
Deploys a VM-Series with 3 interfaces (1-MGMT and 2-Dataplane) into an existing Microsoft Azure environment.
Palo Alto Networks Community Supported
Multiple Azure interface variations
Several ARM templates for the VM-Series with varying options including multiple interfaces.
Palo Alto Networks Community Supported
Azure-2-Firewalls-Public-Load-Balancer
Deploys a Public Azure Load Balancer in front of 2 VM-Series firewalls with the following features:
- The 2 firewalls are deployed with 4-8 interfaces. 1 MGMT and 3-7 data plane.
- Static IP addresses are assigned to the interfaces based on the input in the starting ip address fields.
Note: This template deploys into existing VNETs and storage accounts within the same region. As a result, the storage account and VNET must be created before deploying this template.
Palo Alto Networks Community Supported
https://github.com/kytx42/Azure/tree/master/Azure-2FW-Public-LB
Managed Scale and Resiliency for the VM-Series on Microsoft Azure
An ARM template that deploys two VM-Series firewalls between a pair of Azure load balancers to deliver managed scale and high availability for internet facing applications.
Palo Alto Networks Community Supported
https://github.com/PaloAltoNetworks/azure-applicationgateway
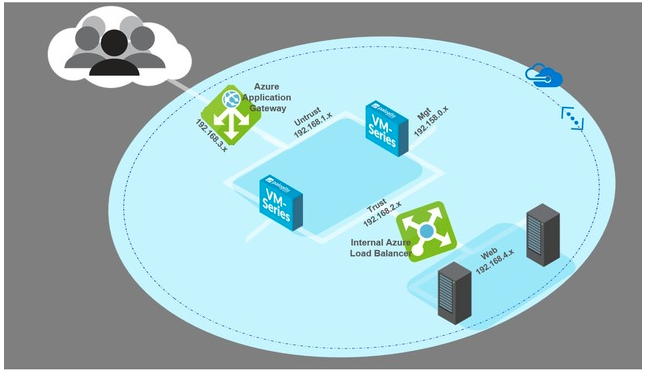
Using VM-Series Firewalls to Secure Internet-Facing Web Workloads
This template creates a highly available VM-Series security solution for Azure for both inbound traffic and outbound traffic. It uses VM-Series firewall pairs coupled with Azure load balancers for a fully redundant security solution.
Auto Scaling the VM-Series-firewall on Azure v1.0
Templates and scripts that deploy Azure Load Balancers and the VM-Series firewalls to deliver security for internet facing applications. Allows for protecting of new or existing workloads.
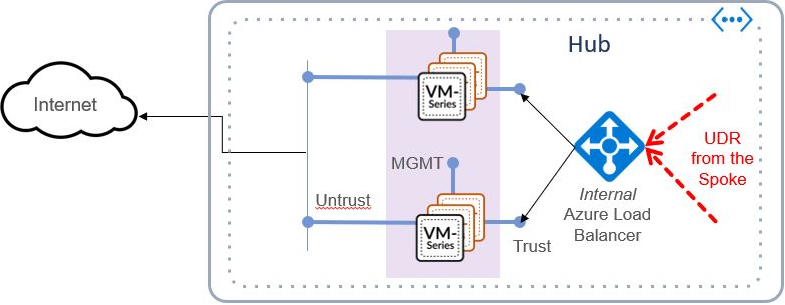
Azure Transit VNet with the VM-Series
Deploys a Hub and Spoke architecture to centralize commonly used services such as security and secure connectivity. All traffic to and from the Spokes will 'transit' the Hub VNet and will be protected by the VM-Series next generation firewall.
Azure Transit VNET architecture with auto scaling VM-Series in application spoke
Deploys a Hub and Spoke architecture to centralize commonly used services such as security and secure connectivity. All traffic to and from the Spokes will 'transit' the Hub VNET and will be protected by the VM-Series next generation firewall. Version 1.1 adds ability to do auto scaling for VM-Series to protect Internet facing applications running in a spoke VNET.
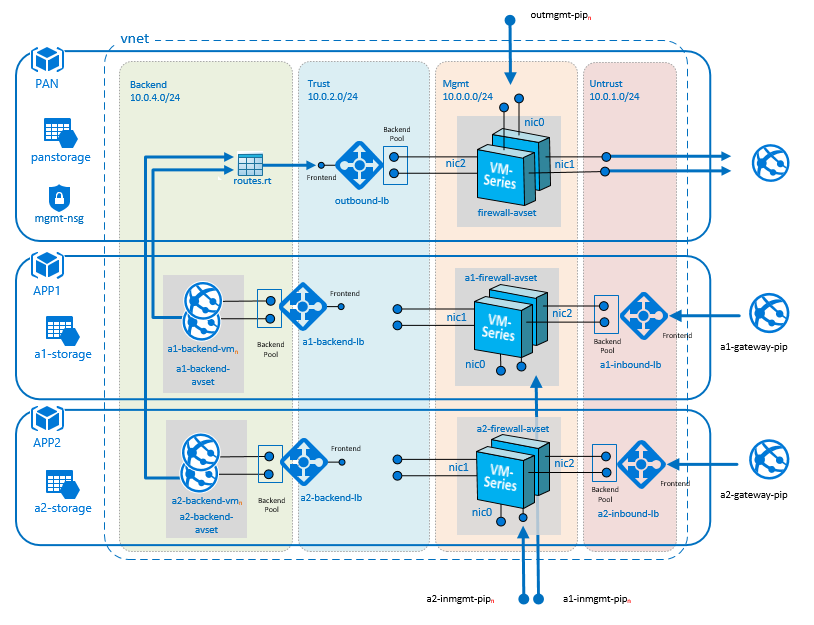
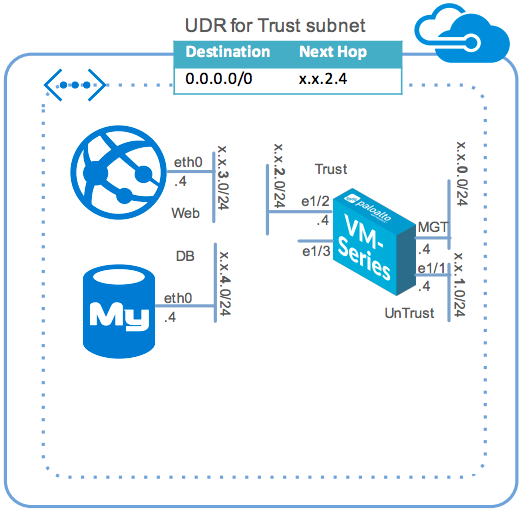
Two tier application environment protected by VM-Series
ARM template that deploys a two-tiered web/DB application environment secured by a VM-Series firewall. Template includes relevant User-Defined Route (UDR) tables to send all traffic through the VM-Series firewall.
Terraform two tier application environment protected by VM-Series
A Terraform Template that deploys two-tiered web/DB application environment secured by a VM-Series firewall.
Palo Alto Networks Community Supported
https://github.com/PaloAltoNetworks/terraform-templates/blob/master/azure_two_tier_sample
Azure VM Monitoring
Python script that harvests Azure VM properties and publishes them as IP-tag mappings that can be used in a Dynamic Address Group.
Palo Alto Networks Community Supported
Discussions
| Views | Replies |
|---|---|
| 865 | 0 |
| 4615 | 7 |
| 1041 | 0 |
| 3497 | 1 |
| 406 | 0 |
| 1039 | 0 |
| 3929 | 1 |


 VM-Series on Azure Configuration Overview
VM-Series on Azure Configuration Overview Review the Azure articles posted in our Knowledge Base
Review the Azure articles posted in our Knowledge Base Go to Customer Support Portal to Create a Case online
Go to Customer Support Portal to Create a Case online