- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Analysis ransomware
- LIVEcommunity
- Discussions
- General Topics
- Re: Analysis ransomware
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Analysis ransomware
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-01-2019 05:04 AM
Hi,
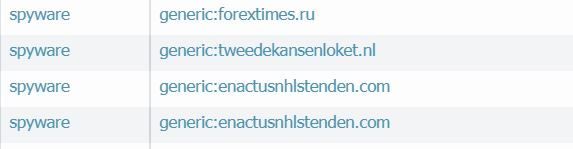
One of our servers have been infected by any kind of ransomware. We can see several files encripted. So we are seeing any evidence about the infection in the PA. The only trace that we saw in PA is that the infected server sends many dns sessions to strange domains:
S is there any way to prevent these external dns sessions? are these sessions related with ransomware virus?
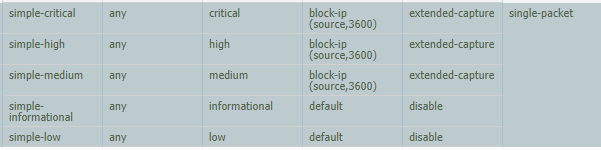
I tried to find the ID in spyware profile in order to chenge the action from alert (current) to drop) but i cant not find it.
any advice to know what it happened and solved it in future?
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-01-2019 06:42 AM
you should enable DNS sinkhole in the antispyware profile, and if you're on PAN-OS 9.0 you can consider adding the DNS security service
protectionwise it would be good to have full protection profiles (AV, TP, AS, WF, URL) set up on all your policies on the firewall , and traps on the endpoint to defend against 0-day
you could also look into running a BPA to tighten up your security posture
PANgurus - Strata & Prisma Access specialist
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-01-2019 09:35 AM
To make suggestions relevant to your environment we'll need a lot more information about your device config (security policy and other subscription services you have and how they're configured.)
That said, like @reaper mentioned using the BPA to shore up your config. To help prevent this in the future you should make sure you're using file blocking profiles to at least track all files devices on your network are downloading from the Internet. You should also look into blocking file types which hosts typically have no business downloading from the Internet.(VBS for instance.) You can look into implementing GEO blocking which will help prevent some infections. Make sure you have SSL decryption deployed in your environment to help add visibility in your firewall to catch potentially malicious payload which is delivered via an encrypted session.
Before making any changes though be sure to understand what you're looking at blocking and making sure there aren't any business processes which might be impacted from any changes you might make.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-02-2019 01:10 AM
Is there any way to change the default action (Alert) for "Spyware generic"? I tried to look but i cant not find it
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-02-2019 01:49 PM
Hello,
You can set exceptions. However I would recommend using the criticallity as a best practice.
Also as described above, set up DNS sinkhole as well as wildfire. If you setup packet capture, you might only get the DNS requests. You can use a free safe DNS source such as quad9 until you are comfortable with purchasing one. This service is not a replacement for sinkhole, it is a compliment to it.
- 5379 Views
- 4 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Wildfire False Positive on Detection of .XLSX extension in General Topics
- Microsoft Photos.exe in Cortex XDR Discussions
- Palo Alto for email security in Next-Generation Firewall Discussions
- Local Analysis Malware and WildFire Malware Alerts in Cortex XDR Discussions
- Discussion Forum Analysis in General Topics