- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Best practices for HA PANs and switch stack
- LIVEcommunity
- Discussions
- General Topics
- Re: Best practices for HA PANs and switch stack
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Best practices for HA PANs and switch stack
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-04-2014 08:24 PM
For this scenario, assume a simple setup. Two firewalls in HA and two switches in a stack. Also assume the firewalls are in active/passive. Consider the below setup, each firewall has one physical link to separate switch members of the stack.
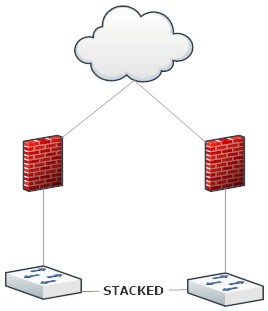
In this configuration, if switch member 1 fails and firewall 1 is the active firewall, does it automatically failover to firewall 2 if there is no link/path monitoring configured? Or are we to assume that without link/path monitoring, switch 1 failing and firewall 1 would remain active firewall and traffic to the internet would fail?
I typically always use the below configuration. Each switch has a port aggregate (802.3ad) and 1 connection in that LAG connects to each member switch. This utilizes double the ports but I was under the assumption the first scenario would only work with link/path monitoring. I also typically do the design so I can withstand any firewall failing AND any switch failing at the same time.
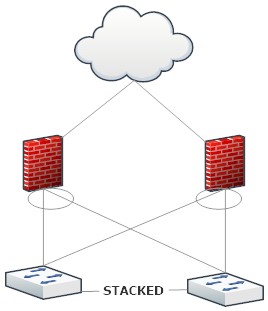
Finally, in the bottom configuration, does anyone have recommendation as far as setting up distribution configs on the switch side? (eg. mac src / dest). Are those needed?
- Labels:
-
Configuration
-
Networking
-
Set Up
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-04-2014 11:30 PM
Hi Mack,
Firewall1 will not trigger any failover if switch1 dies. Please refer following document.
HA active peer does not fail over when ethernet cable is pulled
You have to configure link monitoring for scenario 1.
Regards,
Hardik Shah
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-05-2014 05:23 AM
So just to confirm.. in scenario 1, if switch 1 dies and firewall 1 is active.. no traffic flows to the internet unless link monitoring is enabled, correct?
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-05-2014 06:45 AM
Hi Mack,
It will follow bellow sequence of event.
1. Switch 1 dies
2. Which means port connected with Firewall1 dies.
3. Firewall will ignore the event because its not configured for link monitoring.
4. No Incoming traffic on Trust interface.
7.However Untrust interface remains active, you can ping internet from Untrust.
8. But Firewall1 remains active and rest of the interface remains active.
I would suggest to configure link monitoring, its a intelligent deciwsion.
Regards,
Hardik Shah
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-05-2014 06:53 AM
Thank you! And to 100% confirm, internal to external traffic will not flow because the secondary firewall remains in a passive state.. correct?
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-05-2014 06:55 AM
Hi Mack,
I confirm 100% Internal to External Traffic will not flow, and secondary remains in passive state.
Regards,
Hardik Shah
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-05-2014 06:57 AM
Thank you!
Can you provide insight in regards to my question for scenario 2?
"Finally, in the bottom configuration, does anyone have recommendation as far as setting up distribution configs on the switch side? (eg. mac src / dest). Are those needed?"
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-05-2014 06:57 AM
Hi Mack,
ITs wise to configure interface monitoring, only in few circumstance people dont configure it.
Do you have any reason for not to configure it?
Regards,
Hardik Shah
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-05-2014 07:02 AM
Hi Mac,
Lets say you have implemented scenario 2, then cabling is good on Switch. You dont need any cabling changes.
However, Ports connected with Firewall remains in Access VLAN of Trust interface.
Let me know if that answers your query.
Regards,
Hardik Shah
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-05-2014 07:31 AM
And Inteface on the firewall should be aggregated interface in L3 Mode with an IP address.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-05-2014 07:38 AM
Thanks.. though my question is in relation to distribution algorithms for the 802.3ad channel.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-05-2014 07:41 AM
Hi Mac,
On the switch there is no Etherchannel, its an individual Ethernet Ports.
Aggregate interface exist on PANW Firewall. You can leave it to default as its outgoing traffic from firewall. It doesnt matter which switch recieves it.
Regards,
Hardik Shah
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-05-2014 07:43 AM
So you're suggesting to have the aggregate on the firewall but have that aggregate connect to standard interfaces on the switch with no port-channeling configured? The switch doesn't have to be configured for an 802.3ad aggregation as well?
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-05-2014 07:50 AM
That is right Mackwage, Firwewall in aggregate, and it goes to stand alone port of Switch. And it will work just fine.
Let me know if my answer is Helpful.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-06-2014 10:29 AM
Check out the full sample design in the Design Guide example 4.6 on page 80 and following. I think this is the scenario for your setup.
Designing Networks with Palo Alto Networks Firewalls
ACE PanOS 6; ACE PanOS 7; ASE 3.0; PSE 7.0 Foundations & Associate in Platform; Cyber Security; Data Center
- 12949 Views
- 14 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- HA Failover Issue on PA-3420 with AE LACP – Both Nodes Active (Split Brain ?) in General Topics
- Cortex XDR on Windows blocks Ansible in Cortex XDR Discussions
- HA Passive interfaces not coming up. in Next-Generation Firewall Discussions
- error: azure marketplace vm-series do not bootstrap in VM-Series in the Public Cloud
- Multiple ISP with PalAlto in General Topics



