- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Custom URL category *.github.com not matching/working
- LIVEcommunity
- Discussions
- General Topics
- Re: Custom URL category *.github.com not matching/working
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-29-2021 12:50 PM - edited 10-29-2021 12:56 PM
I read some posts here about the best way to allow github to only *.github.com IPs and I can't seem to find an easy way to do it.
If I do it this way:
Source IP – on-prem networks
Destination - Any
APP ID/Service – github/ssh/ssl/web browsing
URL category - Custom category for *.github.com
Action - Allow
That pretty much allows all traffic that matches the APPID/Service which leads me to believe that the firewall isn't looking at at that URL category or the traffic to match against *.github.com. So I then have to put specific github destination IPs to make this work like I want it to. There has got to be an easier way to do this, is there?
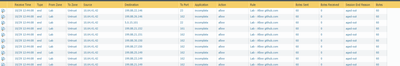
For reference with just the URL category specified on that rule above:
Versus when I have it locked down to giithub destination IPs:
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-29-2021 03:16 PM
Custom URL filters really only work for web traffic, it looks like your trying to use it to also capture SSH and SNMP traffic which isn't going to work. You could use something like FQDN address objects to accomplish essentially the same thing as long as your firewall and clients are using the same DNS servers.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-29-2021 03:16 PM
Custom URL filters really only work for web traffic, it looks like your trying to use it to also capture SSH and SNMP traffic which isn't going to work. You could use something like FQDN address objects to accomplish essentially the same thing as long as your firewall and clients are using the same DNS servers.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-01-2021 05:47 AM - edited 11-01-2021 05:55 AM
I didn't mean to accept this as a solution but not sure how to undo it.
I read somewhere that FQDNs only return 10 IPs? Is there a limitation to doing it this way? I mean if I just put the destination as *.github.com and the applications as github/ssh/ssl/web-browsing that should allow git commands to anything @*.github.com? Sometimes I really despise PAs, like there are so many options and functionality but for something as simple as this there doesn't seem to be any easy solution. Its almost like its too complex in some instances.
I forgot to mention I tried using minemeld pulling github public IPs from their website. Hoping this will suffice but either way its a lot of work for such a small task.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-01-2021 09:41 AM
You couldn't use a wildcard like that in an FQDN address object, you would have to actually create a address object for each required domain. The vast majority of content for GitHub is under GitHub.com, but you also have avatars.githubusercontent.com for avatar assets and github.githubassets.com for actual website assets. You could create a dynamic address-group if you just tagged the address objects and setup the proper filter on the address-group.
The FQDN object IP limit was hardcoded to 10 prior to 7.1 when it was raised to 32. I've honestly never run into an issue with any FQDN address post 7.1, but it is a limitation of using FQDN address objects.
You could also try restricting this to just GitHubs allocated public IP space, but I'm not positive that they don't utilize Azure services for anything being owned by Microsoft.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-01-2021 10:08 AM
So the problem is when a user resolves an @github.com address and it returns an IP not in the external dynamic IP list that minemeld is puling from github that traffic gets denied. I just confirmed this, github.com resolves to a 140.82.113.4 but if you look at their list of public IPs that IP is not there: https://api.github.com/meta Granted it says its not a completely accurate list but really defeats the purpose of even publishing it if isn't kept up to date (rant at github).
As far as the dynamic address group that would require that A) the address object is there and B) its tagged with the right tag. That doesn't scale well at all and is manual which I am trying to avoid.
Just to clarify what you are saying... I can just set the destination as an address object FQDN of github.com and as long as both the client and the PAN are using the same DNS,so they resolve the same IP it should work? I for sure had it set like that prior along with some /24 networks in the destination field and it did not work.
- 1 accepted solution
- 9397 Views
- 4 replies
- 1 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Service Health Probes in Prisma SD-WAN Discussions
- Cortex XDR Tenant Auto-Upgrade 3.17 → 5.0: UI mixed theme, AI pages stuck loading, Marketplace/Playbook Catalog empty + ingestion quota warning in Cortex XDR Discussions
- PAC Retention and URL Category Priority Behavior in Prisma Access in Strata Cloud Manager
- URL Category Change Request for www.intusjuntsparlament.com in General Topics
- What happens when the premium partner and subscription license expires? in Next-Generation Firewall Discussions