- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
External Data Port Cabling
- LIVEcommunity
- Discussions
- General Topics
- External Data Port Cabling
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-29-2014 02:18 AM
Hallo
i am setting up a new PA 3050 FW. I dont want to use the management port to connect to internet and download updates. So I am following the admin guide to "Set up an External Data Port" for updates. Now as per that:
1. I set up a port, say e1/4 on PA 3050, as an internal port in "L3-Trust" Zone and give it a static IP address 192.168.35.100.
2. I set up an external facing port, say e1/5, in zone "L3-Untrust". This port is connected to my ISP Router and has a publicly routable IP.
Where should I cable the internal facing port e1/4 mentioned in point 1 above? Can I somehow NAT the private address to use the Interface e1/5 IP address?
Thanks!
- Labels:
-
Configuration
-
Management
-
Set Up
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-29-2014 04:30 AM
Hello Amit,
Ethernet-1/4 should be connected to your LAN segment ( there is no physical connection required between MGMT interface and L3-Trust interface) and you need a valid NAT & security policy for all outgoing traffic through L3-Untrust (towards internet).
For an Example: I am using Ethernet 1/3 -192.168.10.100( L3-Trust interface) for my service route.
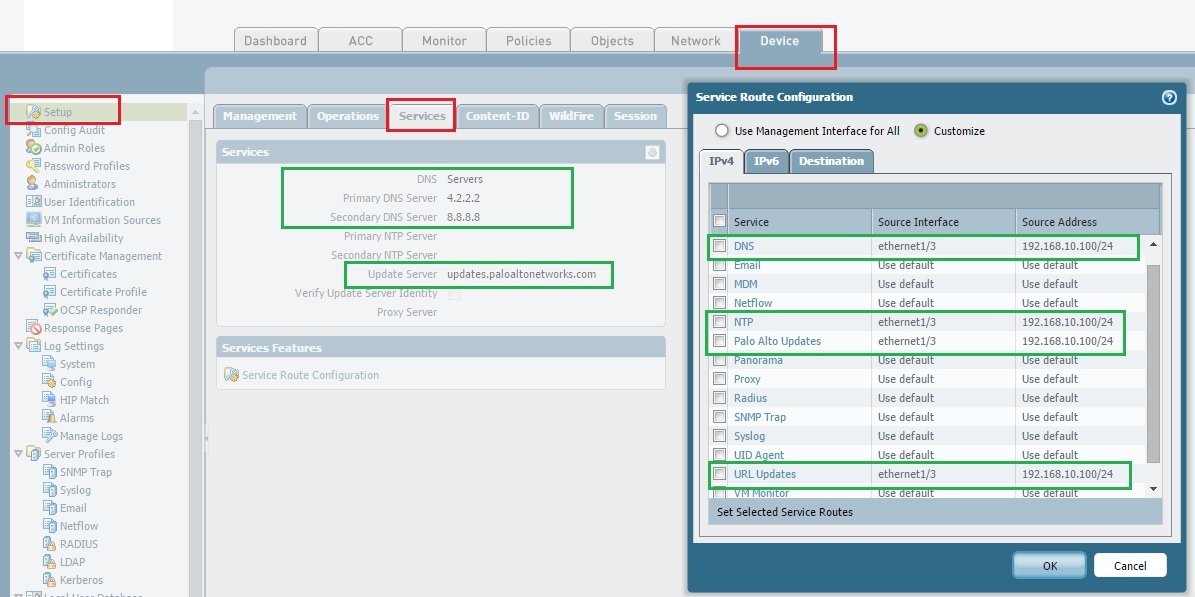
Hope this helps.
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-29-2014 04:30 AM
Hello Amit,
Ethernet-1/4 should be connected to your LAN segment ( there is no physical connection required between MGMT interface and L3-Trust interface) and you need a valid NAT & security policy for all outgoing traffic through L3-Untrust (towards internet).
For an Example: I am using Ethernet 1/3 -192.168.10.100( L3-Trust interface) for my service route.

Hope this helps.
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-29-2014 04:39 AM
Answer to your last query: Yes, you can create a source-NAT for all private address to use the Interface 1/5 IP address.
FYI: In this example, i am using ethernet-1/1 as my L3-Untrust interface ( towards ISP).
NAT RULE:
![]()
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-29-2014 06:48 AM
Hi Amit,
You can achieve this through service route. I would suggest to have PANW updates through untrust interface directly. That way you dont need any special NAT or Security policy. Its much simpler.
Device > Setup > Services > Service route Configuration > Customize > Palo Alto Networks Updates through Ethernet 1/5.
This should work.
Regards,
Hardik Shah
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-29-2014 06:49 AM
And if you want to have updates from ethernet 1/3 than NAT and aditional security policy might require. Which is extra over had.
In that case in above step select interface Ethernet 1/3 to route the PANW update traffic. I dont see any necessity of it.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-29-2014 07:09 AM
Even if you will configure the service route ( through through Ethernet 1/5-Untrust interface), I hope you have to configure a "Untrust-to Untrust" security rule to allow traffic for management. Which will potentially allow anyone from internet to initiate an attack ( not recommended). There should be some valid logic, why ADMIN guide suggested to have a L3-Trust interface for service route.
Try to understand the fact, instead of "extra over had" ![]()
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-29-2014 07:16 AM
Hi Hulk,
There is a default policy which allows "Untrust to Untrust" Traffic. I dont see any security threat with that. Do you see ?
Regards,
Hardik Shah
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-29-2014 07:19 AM
Most of the customers will not have a default allow rule in their production network, which will allow all unwanted traffic through the firewall. Hence, we should suggest some resolution which will be valid and secure for a production network. ![]()
Thanks
- 1 accepted solution
- 4480 Views
- 7 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- PA-820: Cable Type/Lengths and HA Port Questions in General Topics
- Security Policy in Next-Generation Firewall Discussions
- Policy destination field when using URL filtering in Next-Generation Firewall Discussions
- Feature Request – LLDP/CDP Support for Network-Based Endpoint Discovery in Cortex XDR Discussions
- How to trigger a "Response page" on Palo Alto NGFWs using URL filtering & Decryption in Next-Generation Firewall Discussions



