- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
How to Avoid Remote SSH Scan
- LIVEcommunity
- Discussions
- General Topics
- How to Avoid Remote SSH Scan
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
How to Avoid Remote SSH Scan
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-24-2015 09:18 AM
Hello
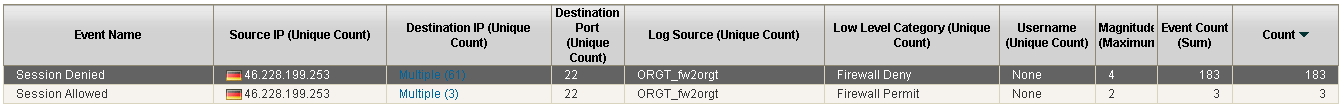
I have a lot of events "deny" followed by other "allow"; All of these to port 22 (SSH) from remote host to several IP(s) in my Untrust and DMZ Zone.
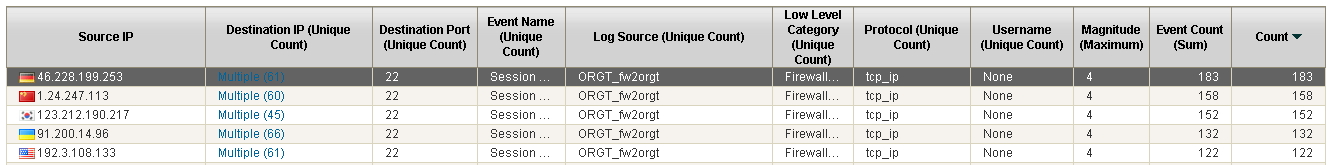
<14>Jun 24 04:01:17 fw2orgt 1,2015/06/24 04:01:16,0003C102047,TRAFFIC,drop,0,2015/06/24 04:01:16,46.228.199.253,213.0.58.124,0.0.0.0,0.0.0.0,rule76,,,not-applicable,vsys1,Untrust,Untrust,ethernet1/3,,ACUNTIA,2015/06/24 04:01:16,0,1,43007,22,0,0,0x0,tcp,deny,74,74,0,1,2015/06/24 04:01:17,0,any,0,418084793,0x0,DE,ES,0,1,0 �
http://www.abuseipdb.com/report-history/46.228.199.253
https://cymon.io/46.228.199.253
Categories for this IP 46.228.199.253: Hacking, FTP Brute-force,
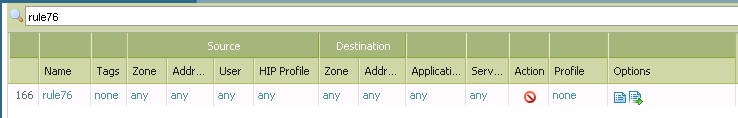
The "rule76" is the last in my security policy rules:
These attempts could indicate an attack SSH (SSH Port Scan, Brute Force SSH, etc) and more if the source IPs have bad reputation.
Reputation of the other source IP:
http://www.abuseipdb.com/report-history/1.24.247.113
http://www.abuseipdb.com/report-history/123.212.190.217
https://cymon.io/123.212.190.217
http://www.abuseipdb.com/report-history/91.200.14.96
http://www.abuseipdb.com/report-history/192.3.108.133
https://cymon.io/192.3.108.133
Actually I have this Zone Proteccion Profile in my firewall:
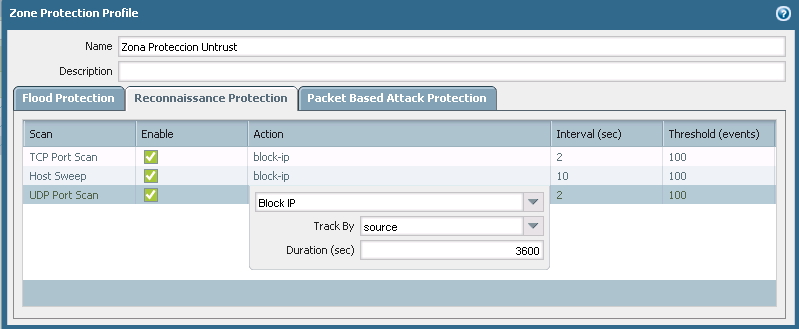
And I applied my Untrust zone:
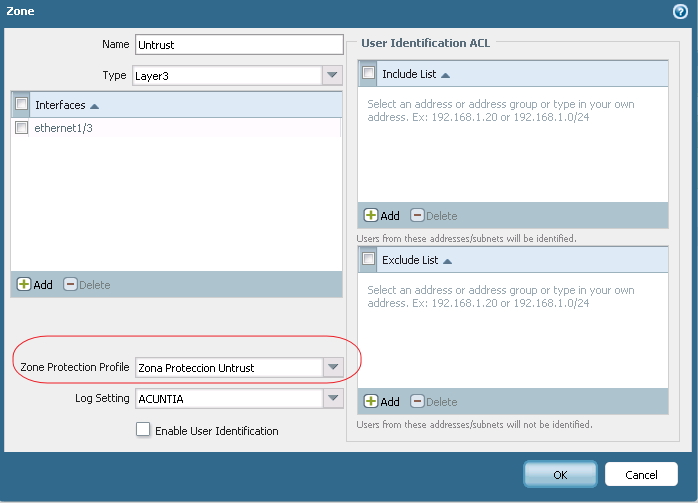
How to Avoid Remote SSH Scan?
I appreciate any help with this issue.
Regards,
- Labels:
-
Configuration
-
Management
-
Troubleshooting
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-24-2015 04:44 PM
Based on your Zone Protection Profile, the TCP port scan should trigger if there are 100 entries within a 2-second span. From the first screenshot you uploaded I see that there are 183 events from the IP in question, but no info on events per second (apologies if I missed it). Were those 183 in a very fast time frame or were they spread out?
Regarding your logs, the first 99 entries in a 2-second span would be skipped by the Zone Protection Profile, and would go through normal rule processing. So you should expect to see a fair amount of logs showing it denied by your catch-all rule 76.
With respect to IP reputation, that is not something the Zone Protection Profile would trigger on. Reputation can become a gray area because a legitimate host could be compromised, leading to a false negative.
If you want to increase your interval or decrease the threshold, you should see sooner triggering for scans. You do take the risk of stopping legitimate traffic with too low a threshold, so you may have to experiment with it to find the right levels for your specific environment.
Best regards,
Greg Wesson
- 4116 Views
- 1 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Admin GUI Login Fails on WAN Interface - Slow Load & "Single Sign-On" Error on PA-410 in Panorama Discussions
- Palo Alto VM-Series in Azure DMZ - AVS in VM-Series in the Public Cloud
- How can I do a staggered roll out of Global Protect in GlobalProtect Discussions
- PAN-GPLimiter: Limit Concurrent GlobalProtect Sessions/Connections Per Unique User in General Topics
- NAT configuration in Next-Generation Firewall Discussions



