- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Multiple ISP load balancing
- LIVEcommunity
- Discussions
- General Topics
- Re: Multiple ISP load balancing
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Multiple ISP load balancing
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-02-2013 07:59 AM
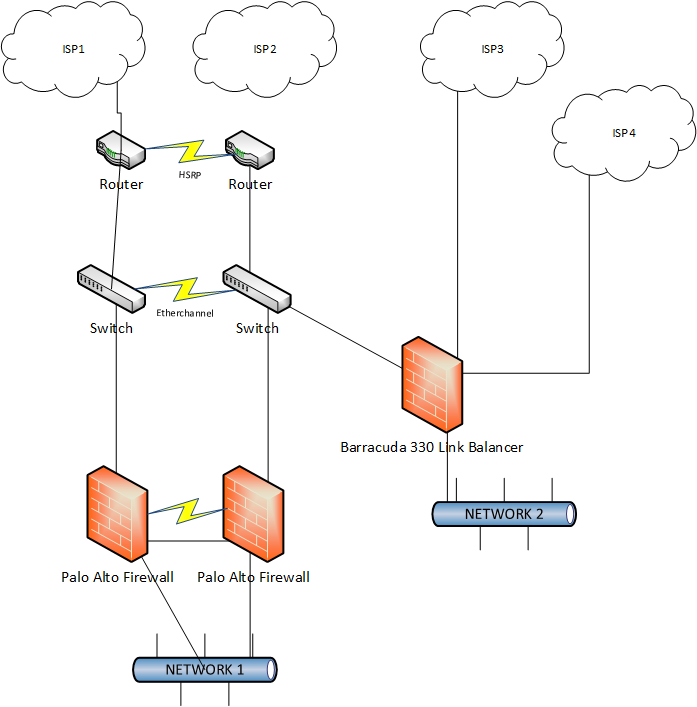
We currently have an Internet setup as shown in the image below. ISP1 is Metro Ethernet running over a disparate fiber path at 100Mbps symmetrical bandwidth. ISP2 is ATM over 1Gb Fiber, with a disparate fiber path and 250Mbps symmetrical bandwidth. ISP1 and ISP1 are running BGP. I use padding to control my preferred link, which changes depending on conditions. ISP3 and ISP4 are business class cable modems with 105Mbps down and 10Mbps up. The cable modems are significantly cheaper than the other connections, they are usually peered better (go figure), and they allow me to use their entire bandwidth without having to worry about usage fees.
I have a /22 on my BGP connection on ISP1 & 2, and a /32 on each of my ISP3 and ISP4 connections. I currently have ISP3 and ISP4 plugged into Ethernet ports on my Barracuda Load Balancer. This firewall services a separate physical open public WIFI network and performs basic NAT, DHCP, and DNS functionality.
I would like to be able to take outbound requests from network 1, behind the Palo Alto firewalls, and send the traffic through ISP3 and/or ISP4. I don't expect to utilize BGP on these cable modems. I expect I would NAT the outbound connection.
It's my understanding the Palo Alto can't do this on it's own. It can do PBF, but not load balancing. I'm looking for suggestions on how to best accomplish outbound load balancing. I do not expect nor do I want inbound load balancing (connections initiated from the Internet to my servers.)
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-02-2013 08:51 AM
Hi,
Load-Balancing is not supported on PA platforms.You can play with Policy Based Forwarding to route/ classify certain traffic based on Network address/Applications etc through ISP-3/ISP-4 Outbound connection.
Thanks
Subhankar
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-02-2013 09:19 AM
I suppose I could purchase two Barracuda Link Balancers, set them up HA, and then use PBF on the Palo Alto to send specific traffic to the inside vIP of the Barracudas. Such traffic would likely need to be double NATed. I would need to exclude B2B destinations that have IP filters in place based on our BGP network, or get static IPs on the cable modems and have those added to the IP filters.
I suppose I could connect a port from ETHERNET2 to each of the Palo Alto firewalls on a new Ethernet port, then use PBF to redirect traffic to the existing Barracuda. Such traffic wold be double NATed. As I've never used the police based forwarding before, I'm a bit concerned about making this change on my production firewall.
In this scenario, say I gave the Palo Alto Firewalls a 192.168.0.9/24 address on the private inside of the Barracuda Link Balancer. I assign it as zone WIFI and interface 1/7. Then I create PBF rule that says if the source is (PC VLAN RANGE, Zone TRUST) and the destination is (Akamia CDN Netblock) I forward this to egress from interface 1/7 (right?) with a next hop of 192.168.0.1, my Barracuda inside vIP. I would create a fail-over monitor and specify an IP address to ping. Preferably, the IP address would be a remote IP address at Akamia, not something on my LAN. This way I can fail over if there is an upstream failure.
Do I understand correctly? If not, what mistakes am I making?
- 5864 Views
- 2 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Cortex XDR Tenant Auto-Upgrade 3.17 → 5.0: UI mixed theme, AI pages stuck loading, Marketplace/Playbook Catalog empty + ingestion quota warning in Cortex XDR Discussions
- High Bandwidth on Broker VM: Cluster Mismatch (v29 vs v28) & P2P in Cortex XDR Discussions
- Cortex XDR_Broker VM Cluster and Externel Load Balancer with active/active applets usage. in Cortex XDR Discussions
- WTH is process 'touch' and hwy is it showing zombie? in General Topics
- Prisma Access with ECMP in Prisma Access Discussions



