- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Secshow.net
- LIVEcommunity
- Discussions
- Security Operations
- Cortex XDR Discussions
- Re: Secshow.net
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-22-2023 10:54 PM
Hello All,
I am getting the same threat log with Threat ID tunneling: secshow.net. and continuously sinkhole the traffic. If anyone can help identifying what is that.
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-24-2023 11:58 PM
Hi @ade.reza , @amjadkhan ,
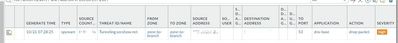
Can you shared a screenshot of the detailed log view?
Stay Secure,
Jay
Don't forget to Like items if a post is helpful to you!
Please help out other users and “Accept as Solution” if a post helps solve your problem !
Read more about how and why to accept solutions.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-27-2023 11:44 PM
Hello all,
I have the same problem, any updates ?
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-28-2023 06:49 AM
Same problem here also. The other strange part is, that they typically occur from one of my external IP's going to another of my external IP's.
Domain Name: SECSHOW.NET Registry Domain ID: 2793806009_DOMAIN_NET-VRSN Registrar WHOIS Server: grs-whois.hichina.com Registrar URL: http://wanwang.aliyun.com Updated Date: 2023-06-27T02:10:51Z Creation Date: 2023-06-27T02:07:57Z Registry Expiry Date: 2024-06-27T02:07:57Z Registrar: Alibaba Cloud Computing Ltd. d/b/a HiChina (www.net.cn) Registrar IANA ID: 1599 Registrar Abuse Contact Email: DomainAbuse@service.aliyun.com Registrar Abuse Contact Phone: +86.95187 Domain Status: ok https://icann.org/epp#ok Name Server: DNS23.HICHINA.COM Name Server: DNS24.HICHINA.COM DNSSEC: unsigned URL of the ICANN Whois Inaccuracy Complaint Form: https://www.icann.org/wicf/ >>> Last update of whois database: 2023-11-28T14:47:52Z <<<
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-28-2023 09:47 PM
Unfortunately, in my case, local host is behind NAT, so that I cannot see either Source User or machine IP or MAC.
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-13-2023 09:36 AM
secshow.net and secshow.online DNS traffic happening for us too, public IP to Public IP. The URLs not matching with typical syntax for DNS tunnelling so I don't think that's what's happening. One domain owned by alibaba.
Ever since the upgrade in October to 10.1.11 this has been happening - did not see any patch notes about this or DNS. Many changes though in this release.
Upgrading to 10.2.7 soon and wondering if this will fix it.
@JayGolf - if palo has any updates or communications for their customers about this it would be great. Seems like a widespread issue that hasn't been communicated. Given that this is setting off security alerts some sort of note would be great that Palo is at least aware if this is a bug and is working on a fix.
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-13-2023 02:23 PM
Unfortunately 10.2.7 does not fix this. It is still going strong on my 450's with 10.2.7
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-20-2024 01:31 AM
Hi, @jasonwald and @JayGolf we are having similar looking issue. Is there any progress finding out where such traffic is coming from?
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-20-2024 04:04 PM - edited 01-20-2024 04:07 PM
I'm not a Palo Alto user, but I've been receiving this traffic for several months. It appears to be someone spoofing an adjacent source address while making DNS queries to every IPv4 address, and checking which IPs end up forwarding the query to a recursive resolver. Presumably the goal is to find open resolvers for DNS amplification attacks or similar. The hex string in the secshow.net DNS name corresponds with the IP address being spoofed, and I've been messing with their results by making DNS queries for random IPs whenever the spoofer is active. It appears to be working, as they've ramped up the frequency of scans, and made some modifications to the hostname format. Hopefully they'll give up soon.
I haven't received any traffic for secshow.online, interestingly.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-28-2024 01:19 PM
I can confirm that it seems to be back. In addition to secshow.net, there's also now a "savme.xyz" producing the same type of traffic. Someone did a write-up on it here: https://dataplane.substack.com/p/destination-adjacent-source-address
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-28-2024 01:29 PM
Thank you for sharing this.
- 9256 Views
- 12 replies
- 1 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!