- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Antivirus Decoder Action
- LIVEcommunity
- Discussions
- General Topics
- Antivirus Decoder Action
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Antivirus Decoder Action
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-24-2014 03:43 PM
I feel silly asking this - wouldn't you want a deny on any decoder where a virus is detected rather than allowing the traffic and just throwing an alert?
- Labels:
-
Content-ID
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-24-2014 03:58 PM
Hello mrsoldner,
As per my understanding, action is taken based on the different severity level of that virus. If that virus is having typically very little impact /or no impact on an organization's infrastructure. Then the action will be set to "alert".
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-24-2014 04:06 PM
Setting a block for viruses on smtp will cause the originating server to keep trying to relay the email until a timeout occurs. This could potentially cause a lot of unwanted traffic pointed at your smtp server that is getting blocked over and over by the firewall. That may still be preferred to allowing a virus in via smtp, but it's just something to be aware of.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-24-2014 04:26 PM
Is there somewhere that Virus severity is noted?
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-24-2014 04:53 PM
jtyler wrote:
Setting a block for viruses on smtp will cause the originating server to keep trying to relay the email until a timeout occurs. This could potentially cause a lot of unwanted traffic pointed at your smtp server that is getting blocked over and over by the firewall. That may still be preferred to allowing a virus in via smtp, but it's just something to be aware of.
Good point, I did some digging and found this: Threat Prevention Deployment Tech Note
It looks like some intelligence is built in for SMTP and will send back a 541 response so that the other side doesn't keep resending the email. POP and IMAP however don't have any intelligence built in. So, per the doc:
Note: The reason why SMTP, POP3 and IMAP have the default action set to ALERT is because in most cases there is
already a dedicated Antivirus gateway solution in place for these protocols. Specifically for POP3 and IMAP, it is not
possible to clean files or properly terminate an infected file-transfer in-stream without affecting the entire session.
This is due to shortcomings in these protocols to deal with this kind of situation.
Thanks for the help. I think we'll stick with the defaults for now and potentially ratchet up SMTP.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-24-2014 05:25 PM
Hello Mrsoldner,
Every virus signature has different severity. You can find that information from following link. Select type as a "virus".
https://threatvault.paloaltonetworks.com/
You need to feed either virus name or ID.
Regards,
Hardik Shah
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-26-2014 09:52 AM
hshah wrote:
Hello Mrsoldner,
Every virus signature has different severity. You can find that information from following link. Select type as a "virus".
https://threatvault.paloaltonetworks.com/
You need to feed either virus name or ID.
Regards,
Hardik Shah
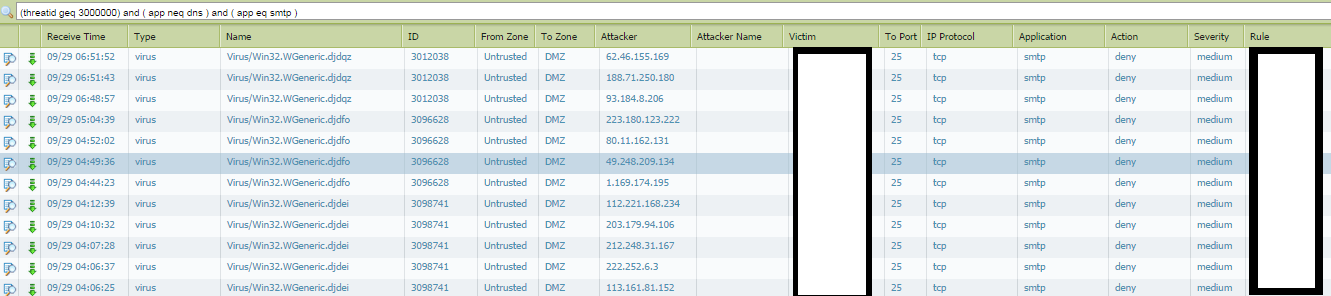
Thanks hshah - I've never seen a severity included with a virus though which is why I'm puzzled. For example:
ID: 3088393
The threat vault just calls it a virus. It came in via SMTP (which by default, the action is alert) however in the logs it shows it was blocked.
Just making sure I fully understand.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-26-2014 10:08 AM
Hello Mrsold,
My bad, its vulnerability which has sev not anti-virus. Thanks for correcting me.
Regards,
Hardik Shah
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-26-2014 10:12 AM
HULK wrote:
Hello mrsoldner,
As per my understanding, action is taken based on the different severity level of that virus. If that virus is having typically very little impact /or no impact on an organization's infrastructure. Then the action will be set to "alert".
Thanks
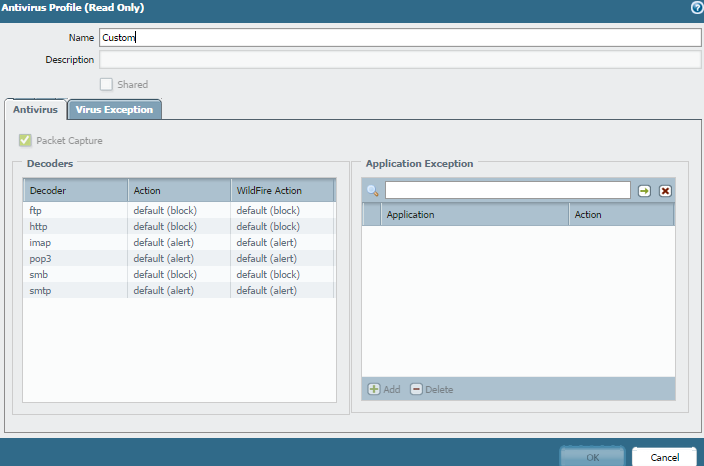
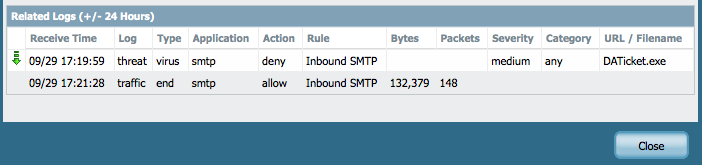
HULK could you clarify? My antivirus decoder for SMTP is set to "alert" for WildFire and Threat however I am seeing Virus blocks for SMTP traffic.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-26-2014 02:46 PM
you use alert profile but you see block logs ? that is interesting.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-27-2014 04:59 AM
Another reason the action may be set to alarm rather than deny as the default action is the possibility of false positives. Palo Alto is pretty good about only setting drop/reset actions to signatures are have virtually no false positives. You don't want to be blocking too many legitimate sessions.
The alarm option then can give you a report on suspects that can be researched and confirmed. If you subsequently find that virtually all the alarms are real then you have the option to change the action to a deny/reset instead of alarm.
ACE PanOS 6; ACE PanOS 7; ASE 3.0; PSE 7.0 Foundations & Associate in Platform; Cyber Security; Data Center
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-29-2014 05:19 AM
panos wrote:
you use alert profile but you see block logs ? that is interesting.
Yeah, very interesting indeed. I need to do some more digging...
- 12091 Views
- 16 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Help me understand wildfire please!!! in General Topics
- wildfire is not reporting in the wildfire submission in Next-Generation Firewall Discussions
- XDR data lake and related questions in Strata Logging Service Discussions
- wildfire-virus threatID 602574714 false positive ? in Advanced Threat Prevention Discussions
- Antivirus Profile - Wildfire Inline ML - best approach to enabling? in General Topics