- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Problems with the firewall (web-browsing specifically)
- LIVEcommunity
- Discussions
- General Topics
- Re: Problems with the firewall (web-browsing specifically)
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-20-2014 03:58 AM
Hello,
I have just configured our new firewall, but I'm having a small issue with it. Basically, I have a security policy set with web-browsing application-id enabled (Facebook App-ID is also enabled). Now, every time I test it I'm unable to open Facebook.com on my test machine, nor any other website. However, when I modify the security rule to include a service port of 80, all the webpages open just fine. Do you know what might be going on?
Thank you in advance.
Best regards,
Marcin
- Labels:
-
App-ID
-
Configuration
-
Troubleshooting
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-20-2014 05:45 AM
Hi Marcin
While building security rules you need to take into account that applications and services are mutually dependant, so for example defining any in the services will allow web-browsing on all possible ports including 65000 etc. setting the services to application-default would then limit web-browsing to ports 80 and 8080, if you set service manually to tcp-50, web-browsing would only be allowed on port 50
if you, as another example, then were to set applications to any and service to tcp80, you would be allowing web-browsing but also ftp, ssh, smtp, ... over port 80
so if you want to stick to the default ports it's good to simply set application-default in the services to limit each protocol to it's own ports. If you do need to add non-default ports keep in mind you need to add services for the default ports also
PANgurus - Strata & Prisma Access specialist
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-20-2014 04:36 AM
Hi Marcin
Would you be able to add a screenshot of your policy, this may help visualize the issue you are encountering.
If you add a security policy with the same zones and action "drop" at the bottom, your traffic log may also shed some more light on what is being discarded and why.
regards
Tom
PANgurus - Strata & Prisma Access specialist
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-20-2014 04:55 AM
Hi Tom,
Thank you for your answer. I'm attaching the screenshot below (staff rules is the problematic entry).
Best regards,
Marcin
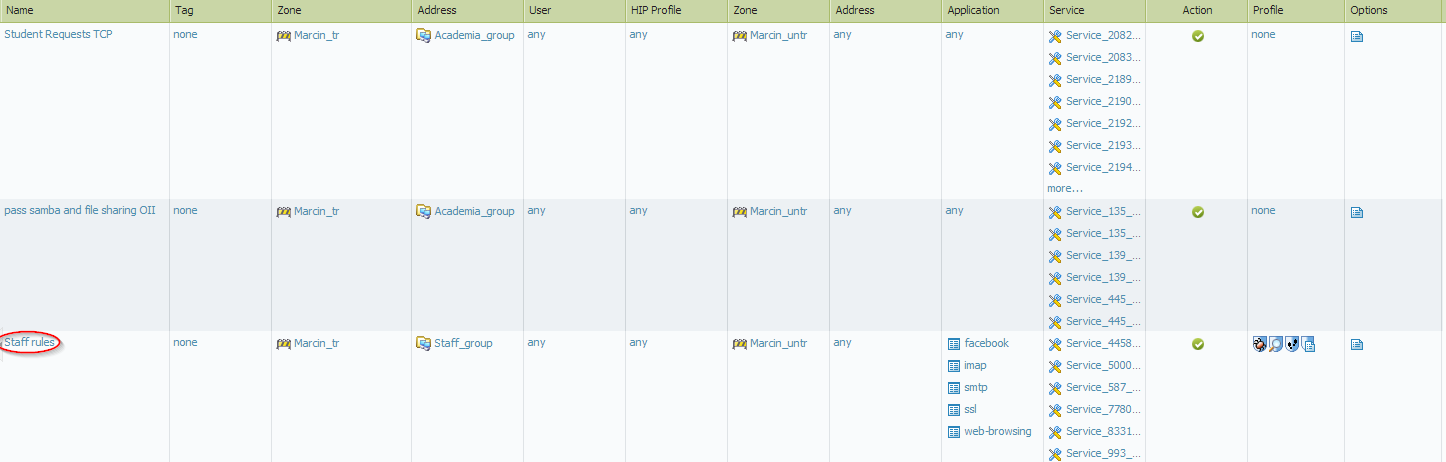
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-20-2014 05:18 AM
What's interesting, when I change the IP address of the machine, so that it belongs to a different address group, I'm able to browse the Internet just fine. This is despite the fact that a very similar application-ID are used for that second address group.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-20-2014 05:36 AM
Strange rule you have there.
Why are there so many services allowed?
If you have not included the default services of webbrowsing and / or facebook (tcp80, tcp8080, tcp443...), it can not work.
Best practise is to define applications to allow and choose "application default" in the service field.
Otherwise all the applications are allowed on all ports you define under the service field.
If you have applications that are not defined by PA you can create custom application and use a special rule for them.
So your rule for webbrowsing and facebook should look like:
from trust - to untrust - application webbrowsing, facebook - service application default - action allow (maybe define some groups or users to limit the rule).
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-20-2014 05:45 AM
Hi Marcin
While building security rules you need to take into account that applications and services are mutually dependant, so for example defining any in the services will allow web-browsing on all possible ports including 65000 etc. setting the services to application-default would then limit web-browsing to ports 80 and 8080, if you set service manually to tcp-50, web-browsing would only be allowed on port 50
if you, as another example, then were to set applications to any and service to tcp80, you would be allowing web-browsing but also ftp, ssh, smtp, ... over port 80
so if you want to stick to the default ports it's good to simply set application-default in the services to limit each protocol to it's own ports. If you do need to add non-default ports keep in mind you need to add services for the default ports also
PANgurus - Strata & Prisma Access specialist
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-20-2014 05:53 AM
In addition:
when needing and adding non-default ports to an application, i would use a separate rule for this.
If you e.g. allow webbrowsing and smtp in one single rule and choose application default on the services, each application will only be allowed on its own default ports. So webbrowsing would not be allowed on port 25.
But if you in addition need port 9090 for webbrowsing and take one rule with application webbrowsing and application smtp and choose manually the services (so you would take tcp80, tcp8080, tcp9090, tcp25, tcp587), that would also allow smtp on port 80 or webbrowsing on 587....
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-20-2014 06:35 AM
Thank you kbe, I have managed to sort the issue out, thanks to your and tpiens advice.
- 1 accepted solution
- 7781 Views
- 7 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Global Protect Connectivity Issue in GlobalProtect Discussions
- Request for VPN Capability Enhancement on Palo Alto Networks Firewalls in Next-Generation Firewall Discussions
- Issue with IOS 26 and SMTP in Next-Generation Firewall Discussions
- Allowing access to a specific IP while blocking the rest of IPs in XDR host firewall in Cortex XDR Discussions
- Policy processing order in General Topics



